- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: remote client VPN authentication with Certific...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
remote client VPN authentication with Certificate
hi
at the moment we have the standard remote vpn for our users with office mode, authentication done through LDAP and MFA, which works perfectly, no complaints here until so far ![]()
but i want to start implement certificate based authentication on the remote vpn clients.
the CA is internal, our Active Directory will issue the certificates for the users.
i have an NPS server(RADIUS), policy is created, although could be wrongly configured.
i have the RADIUS server defined on the management.
but i am missing 2 steps :
1st : how do i enforce/allow users to user to use the certificate to authenticate.
2nd : could someone provide some step-by-step or a policy configuration for the NPs server
at the moment i have this :
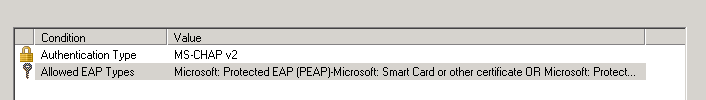
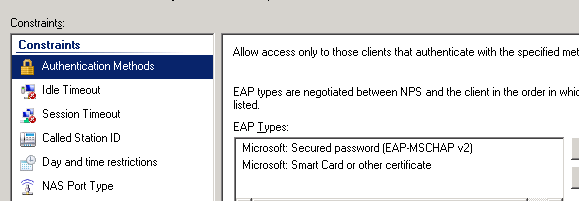
and of course the firewalls defined as clients on the radius server.
Regards
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
During new Site creation at Remote VPN, You can select Certificate as authentication method.
Also there are option that which type of certificate you will use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
thanks for the feedback.
that is something i saw and tried it, but fails the authentication.
looks like i am missing more configuration the checkpoint and i am looking for a step-by-step how to enable it.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is the R80.10 RemoteAccess VPN AdminGuide and the R77 VPN Admin Guide where the needed steps can be found.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
i spent some time reading the manual and something is not clear.
i did the following, but something is missing :
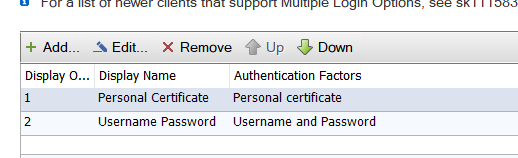
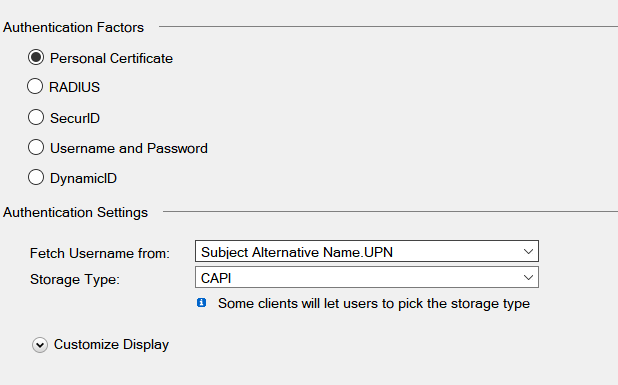
i created a user_template
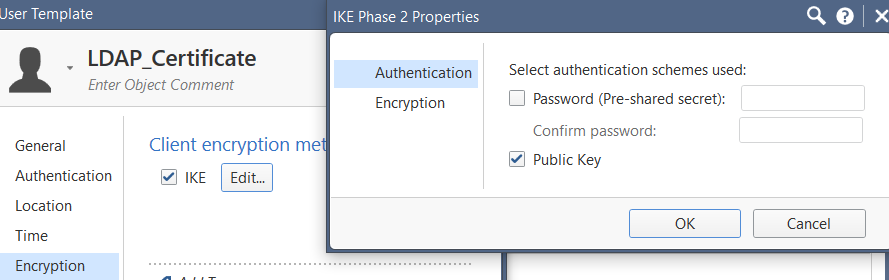
but here is what i am missing, on the ldap account unit i have no idea what option to chose , nothing is related to the certificates, just the radius, but i dont want to have a radius to do the certificate authentication.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then i would follow Using Certificates Using Third Party PKI in Remote Access VPN Administration Guide R80.10 p.43f !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i already read that part, and what is says is to create local users on the dashboard and this is not manageable.
as for the normal username+password authentication you do not need to create local users on the dashboard, but the firewall passes the authentication to the LDAP server, there should be a similar option for the certificates.
Configuring Third-Party PKI Certificates To use a third-party PKI solution:
1. In SmartConsole, from the Objects Bar click Users > Users.
2. Create a new user or double-click an existing user. The User Properties window opens.
3. From the navigation tree, click Encryption.
4. Click Edit. The IKE Phase 2 Properties window opens.
5. Click the Authentication tab and select Public key.
6. Define the third party Certificate Authority as an object in SmartDashboard.
9. Transfer the certificate to the user.
please provide a proper answer, i read the manual from top to bottom and i am missing just one configuration which i am not able to find it.
sending me all the time to the admin manual doesn't help.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry - look here:
User Authentication Options
Select the scheme to be used to authenticate users defined with this template. These schemes are used in authentication rules and in Remote Access (when the user is not identified using a certificate or an IKE preshared secret).
Select one of these authentication methods:
- Undefined - means that either no authentication is performed and access is always denied, or IKE authentication is used, as defined in the Encryption tab.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i had it set up as Undefined on the authentication method
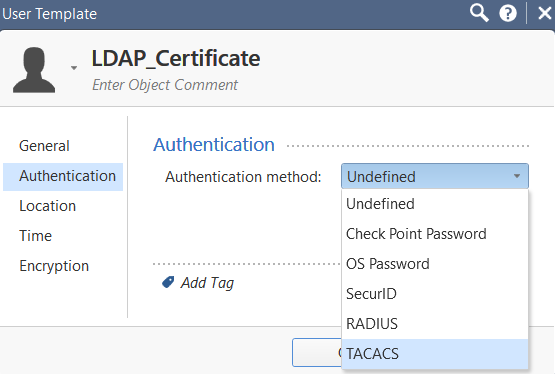
and then on the encryption i have this.

for some reason it always the same error, i masked the username
Category: Session
Event Type: Login
Name: Endpoint Security VPN
Version: E80.80
Build Number: 986005503
User: ******@*****.com
Authentication Method: Certificate
Login Option: Personal Certificate
Failed Login Factor: 1
Data Protocol: IPSec
Status: Failure
Reason: DN ****@****.com unknown.
although i think the missconfig comes from here since it doesnt give a proper authentication scheme for certificates.
any idea ? what i should pick or change? is this config correct?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to add the users to a user group that is a participant in the RemoteAccess Community and add option Personal Certificate in GW > VPN clients > Authentication. Then you have to install databes and policy.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that is already done, and works for username+password.
is the authentication scheme correctly selected to allow certificates ? because as you can see i selected only the checkpoint password.
https://community.checkpoint.com/people/dwelccfe6e688-522c-305c-adaa-194bd7a7becc maybe you could give some hint ? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you follow the steps here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i would say i tried, but after so many tests i am not sure anymore ![]()
i will try again this afternoon.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just tried this option and still the same error.
Category: Session
Event Type: Login
Name: Endpoint Security VPN
Version: E80.80
Build Number: 986005503
User: *****@******.com
Authentication Method: Certificate
Login Option: Personal Certificate
Failed Login Factor: 1
Model: PC
OS Name: Windows
OS Version: 10
OS Edition: Professional
OS Build: 16299
OS Bits: 64bit
ID: 9240021C-799E-4DB0-A2CC-E7A23670C716
Re-authentication every:
Login Timestamp: 2018-04-12T16:15:21Z
IP Protocol: 6
Destination Port: 443
Data Protocol: IPSec
Status: Failure
Reason: DN ******@*****.com unknown.
Suppressed Logs: 0
Action: Failed Log In
Type: Log
Blade: Mobile Access
Origin: *********
Service: TCP/443
Product Family: Access
Marker: @A@@B@1523549079@C@2464621
Data Encryption: AES-256 + MD5
Severity: Informational
Rounded Sent Bytes: 0
Confidence Level: N/A
Rounded Bytes: 0
Rounded Received Bytes: 0
OS: Windows 10 Professional 64bit (build 16299)
Login Option Factors: Certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would suggest to let TAC find what goes wrong here!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
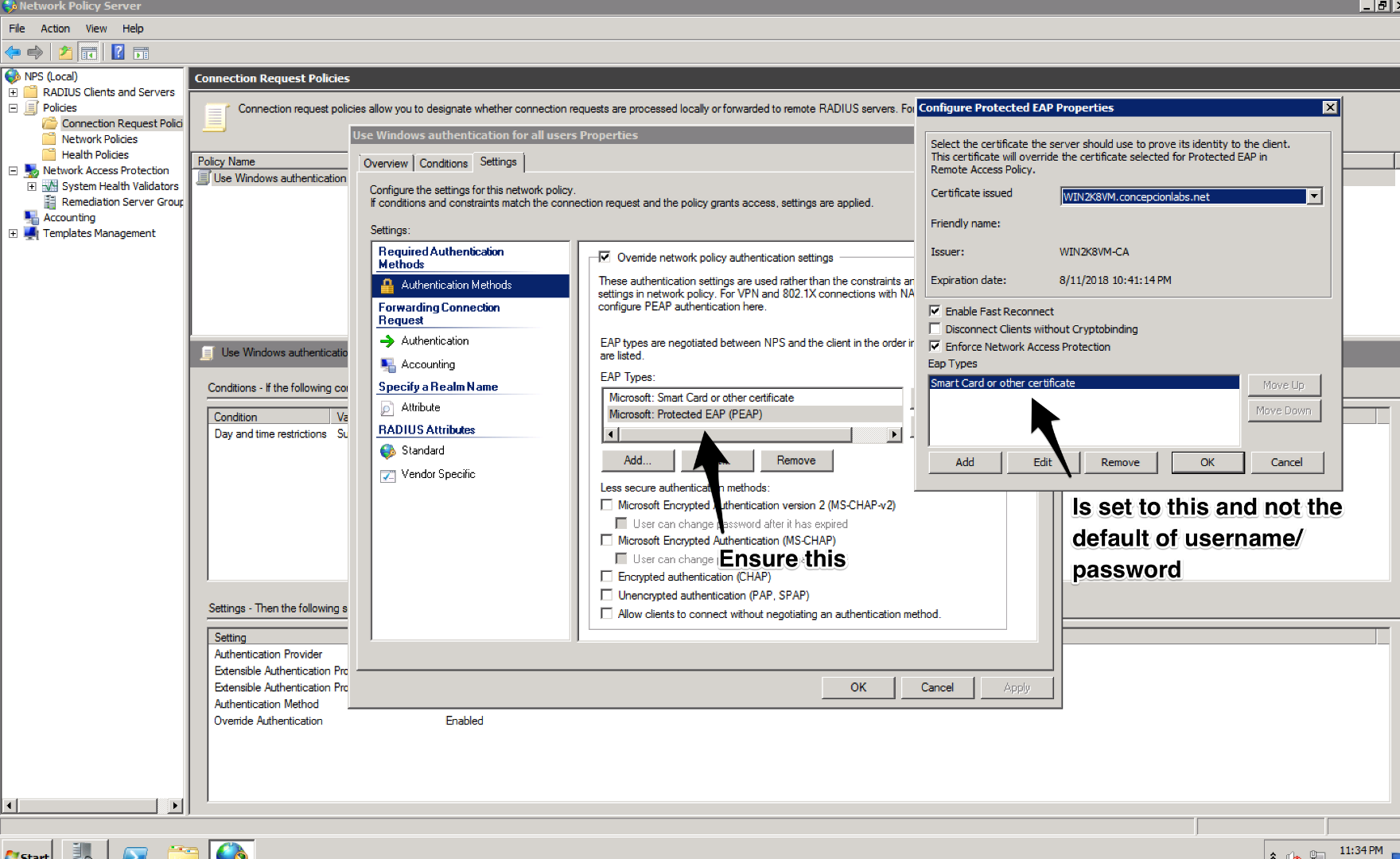
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did anybody managed to solve this issue? I have the same issue here with the same log
It looks like something is missing with the authentication configuration but it is not stated in the R80.10 remote access documentation (or I missed it somehow)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would still suggest to let TAC find what goes wrong here and post the result ! 😉
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After great remote session with Check Point Support we figured out that the microsoft CA has to be configured in SmartDashboard in addition to the LDAP server
Unlike Domain User authentication It is a must to configure the Microsoft CA in order to authenticate with a certificate.
The documentation is lacking and can definitely be improved since you need to search in 3 different locations (and in Check Mates) in order to figure out the complete configuration of this deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
will you kind enough to share the details or the steps to proceed with the configuration ?
i really don't feel going through TAC for this, it should be documented since the config should be straight forward.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ovdia,
sorry about the late reply, I missed this thread. Apparently even after configuring everything right including the CA, there is a bug in R80.10 which authenticate with the CA using the wrong login factors (the gateway uses default authentication factor and and sends the wrong user login name to the CA). you will have to contact TAC to get it fixed. This is a small change in guidbedit but certificate authentication will not work without it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is all hilarious to me, because I agree on all points about their documentation lacking! Hell, I have too many other things to do, and hired a security consultant to do the cert based VPN, because we use 3rd party devices with dynamic IPs. These devices have to have dynamic IPs because of the LTE connection, along with some type of landline Internet eventually (construction sites). Well, even the the sec engineer and Check Point are having a problem with it right now. Check Point firewall portion is great. Everything else is pretty flaky!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And....two weeks later, they are still working on the site to site cert. Endpoint went pretty smoothly, but now it's time to try cert based auth. Fun!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever get this working? If yes do you recall what was required?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you are signing the CSR at the 3rd Party CA (windows in this case) what certificate template are you using? Documentation does not specify if it should be user, web server, subordinate ca???
Thanks in advance,
Juan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wondering why NPS would need to be part of the scenario? We used to do AD/LDAP (username+password)+Identity Cert from an on-prem CA as you suggest and then flipped over to Azure MFA. Never had a need for a RADIUS server in the middle, not to mention I never liked NPS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that was also my understanding that NPS was for RADIUS which we don't want to use. Just AD/LDAP but we keep getting the unknown user message and can't figure out what we're missing.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


