- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: lice Secure Client License Overview Oneliner (...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
license count remote access (not MOB)
Hello CheckMates,
is there a way to check the available and used licenses of EndPointSecurityVPN connected to the VPN blade not MOB.
For the MOB this is easy with "cvpnd_admin license all".
With "fw tab -t userc_users -s" I can count all currently connected users, does this mean if there is a value of 100. 100 licenses are used ? If one user logged out one license is freed and available for another user immediately?
Wolfgang
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
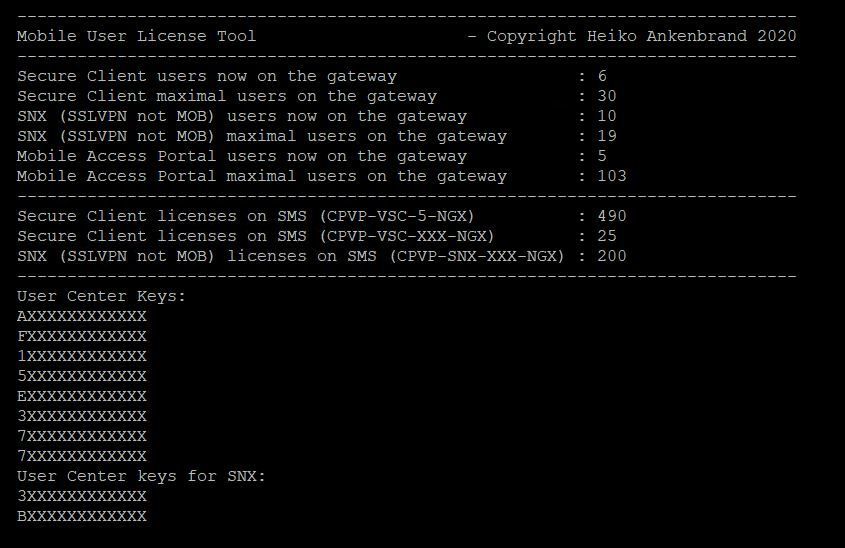
In the past days I have been working on a CLI script that can display all Secure Client license information centrally. This script creates a new command on the management server to read the Secure Client licenses. It displays all Secure Client licenses in total (sum). Furthermore, it can read out the currently used licenses on the gateway. If a connection to the gateway can be established, the following values are read out: Currently used Secure Client licenses and the maximum used Secure Client licenses.
If you execute the script via "copy and past" on the management server, a new CLI command "sclic" is created. Afterwards you can use this command to display all licenses in an overview. Please note that the execution of the new command may take a few seconds. This is a normal behaviour.
Now for following:
- Secure Client licenses
- Mobile Access Portal licenses
- SSLVPN licenses
More read here: R80.x - Mobile User License Tool - replaces "dtps lic"
Here an example:
# sclic 10.0.0.1
Now all license parameters for Secure Client are displayed:
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The official way EndPointSecurityVPN was licensed was by Installed client.
The only check that was done was the number of connected clients, when a client disconnects that slot will be freed again for another client.
The only check that was done was the number of connected clients, when a client disconnects that slot will be freed again for another client.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm working on a script to show that information at the moment, here is a raw draft:
mob_clients=$(cvpnd_admin license all | grep "Total used" | uniq | awk '{ print $5 }')
echo "MOB Clients: $mob_clients"
overall_clients=$(fw tab -t om_assigned_ips -s | grep localhost | awk '{ print $4}')
echo "Overall Clients: $overall_clients"
endpoint_security_clients=`expr $overall_clients - $mob_clients`
echo "Endpoint Security VPN Clients: " $endpoint_security_clients
You could change the script and get the output value via snmp by using the info from sk90860
mob_clients=$(cvpnd_admin license all | grep "Total used" | uniq | awk '{ print $5 }')
echo "MOB Clients: $mob_clients"
overall_clients=$(fw tab -t om_assigned_ips -s | grep localhost | awk '{ print $4}')
echo "Overall Clients: $overall_clients"
endpoint_security_clients=`expr $overall_clients - $mob_clients`
echo "Endpoint Security VPN Clients: " $endpoint_security_clients
You could change the script and get the output value via snmp by using the info from sk90860
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could use cprid_util and collect that info to the management server, this is how I currently collect the information on an MDS:
echo "Customer"
mdsenv DMS
cprid_util -server 1.2.10.10 -verbose rexec -rcmd bash -c "fw tab -t userc_users -s"
echo "Customer"
mdsenv DMS
cprid_util -server 1.2.10.10 -verbose rexec -rcmd bash -c "fw tab -t userc_users -s"
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is not so hard - this is taken from my post Remote Access Users license + count
The "old" RA VPN client licensing worked by counting client IPs (called "seats", CLI "dtps lic" on policy server), and the used licenses count showed the number of clients that did connect during the last 30 days. This is different with MAB licenses, they are defined as the number of concurrent clients; MAB even has five grace clients, so the maximum number of concurrent clients is the number of licenses plus five.
...
From sk39034: How to check the number of currently connected Remote Access users and sk14496: How to check the names of remote access users that have sent traffic through the Security G...
To see the number of currently connected Remote Access users, run this command (in Expert mode) on the VPN Security Gateway:
[Expert@HostName]# fw tab -t userc_users -s
To see the username of each "connected" remote access user (in the last 15 minutes), run this command (in Expert mode) on VPN Security Gateway:
[Expert@HostName]# fw tab -t userc_rules -f
You can also run the following command on the gateway, in order to see the number of OM IPs which are currently assigned by the gateway:
# fw tab -t om_assigned_ips -s
HOST NAME ID #VALS #PEAK #SLINKS localhost om_assigned_ips 372 1 1 0
The above output (#VALS=1 ) means currently one client is assigned an OM IP. This includes SNX users with OM IPs as well, who take up from a different license (MAB). In order to find out how many there are of those and subtract them to leave only IPsec VPN clients (i.e. SecureClient, Endpoint Security VPN, Endpoint Connect), check the following table:
# fw tab -t sslt_om_ip_params -s
HOST NAME ID #VALS #PEAK #SLINKS localhost sslt_om_ip_params 372 1 1 0
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the past days I have been working on a CLI script that can display all Secure Client license information centrally. This script creates a new command on the management server to read the Secure Client licenses. It displays all Secure Client licenses in total (sum). Furthermore, it can read out the currently used licenses on the gateway. If a connection to the gateway can be established, the following values are read out: Currently used Secure Client licenses and the maximum used Secure Client licenses.
If you execute the script via "copy and past" on the management server, a new CLI command "sclic" is created. Afterwards you can use this command to display all licenses in an overview. Please note that the execution of the new command may take a few seconds. This is a normal behaviour.
Now for following:
- Secure Client licenses
- Mobile Access Portal licenses
- SSLVPN licenses
More read here: R80.x - Mobile User License Tool - replaces "dtps lic"
Here an example:
# sclic 10.0.0.1
Now all license parameters for Secure Client are displayed:
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter