- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Remote Access improvements
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remote Access improvements
Hello CheckMates members,
In the past weeks, due to this new remote work requirements, I have been doing otimizations and fine tunning in many VPN gateways, this time with much more demanding scenarios.
While performing such configurations, I've noticed some questions / constraints:
- How to specify that a given group (ex: LDAP group) is tied to a specific authentication method ? If we are talking about the same domain (LDAP Account Unit) there seem to be no means for that.
- For the case where several gateways are managed by the same management (most of the cases) it should be possible to have more than one Remote Access community, for several reasons....
- Mobile Access (Unified vs Legacy)
Previously on Legacy Mobile Access, only users posing on at least one MAB Access rule were allowed to authenticate to the portal. Now, with Unified Mobile Access, users must belong to remote access community in order to authenticate properly.
This brings a limitiation where I can no longer differentiate who can authenticate on the Mobile Acess Portal from who can authenticate using remote access clients. I have to rely on access rules to permit or forbid access to resources, but in what concerns authentication process it didn't improved from legacy to unified...
I think this constraints are affecting many people and therefore it should be improved, don't you think ?
Regards
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you provide a concrete example of the different LDAP Groups requiring different authentication methods?
Right now, there is only one Remote Access community per management domain.
I can see where that might be useful but you can achieve the same effective result with appropriate Access Rules.
As for issue with Unified versus Legacy, I suspect there is more work to do in terms of simplifying this.
Right now, there is only one Remote Access community per management domain.
I can see where that might be useful but you can achieve the same effective result with appropriate Access Rules.
As for issue with Unified versus Legacy, I suspect there is more work to do in terms of simplifying this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
Of course, an easy example is to have a given set of users (regular users) who belong to a specific ad group (say group A) and another set of users (power users) belonging to another specific group (say group B), both within the same Active Directory.
Now, the goal is to assign to group A (regular users) a specific method for authentication (eg: username and password) and to group B (power users) another specific method (eg: Two Factor - username and password + DynamicID).
So if one want to make a more strong /secure authentication for group B (power users) BUT simultaneously want to provide simple method for group A (regular users), this will subvert such principle because power users can also access with username and password....
Now imagine that you want to have several authentication methods and several users profiles (groups), tied to their respective methods. How would you solve this ?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
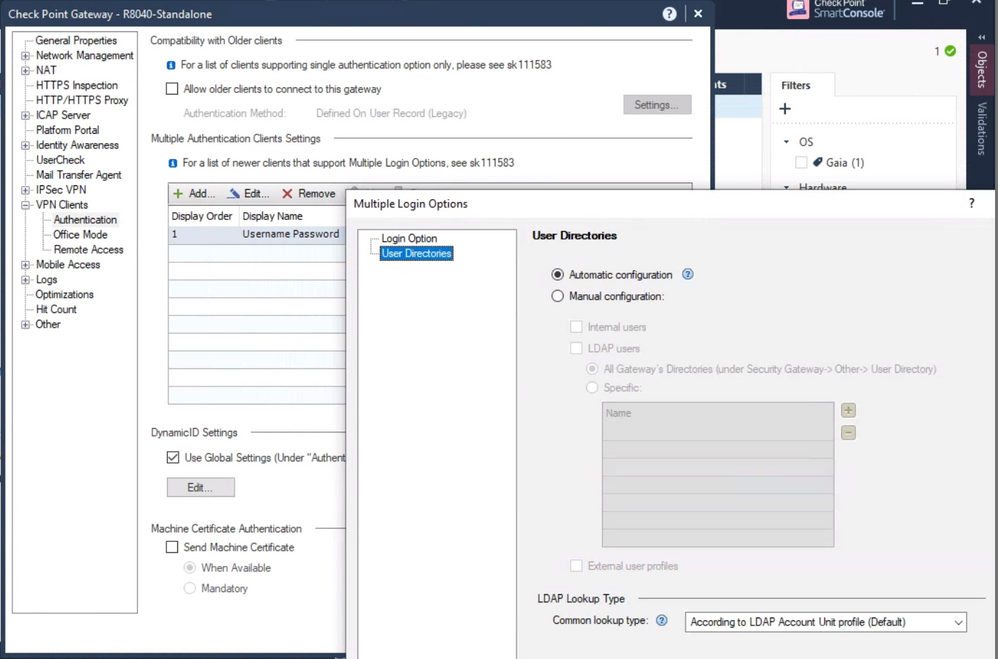
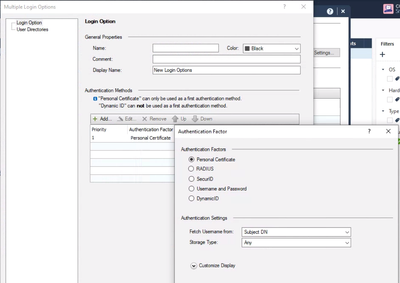
I believe a lot of what you want is right here in the gateway object:
In short you can:
- Define multiple authentication schemes.
- Tie each one to specific LDAP groups.
I will admit, I don't know if this will work exactly the way you want it, but this seems the most promising.
I'll check with R&D.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For that you need two different directories. It can't be tied to individual groups in the same directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon,
Thanks for your answer but like I described earlier the challenge is between LDAP_Groups within the same directory - wich is the most common scenario.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems to me you can choose different LDAP groups within the same directory for the different authentication methods (at least as I understand this dialog).
What happens when you do that?
What happens when you do that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Unfortunately you cannot. You can only choose a specific directory or a set of directories but not an LDAP_Group.
Also, you cannot have two LDAP Account units for the same domain (with different search bases).
I think it's a "dead end".... thats why I was suggesting an improvement.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah. I agree with Pedro.
I am facing same issue. We want to use 2 different authentication for different user group but it is not possible as we have only one LDAP account unit.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter