- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Intermittency in remote VPN user connections
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intermittency in remote VPN user connections
Hello, everyone.
We have an R80.30 running on an OPEN SERVER.
We have been having problems for several days now, in which, several users connecting to our company's VPN, mostly using the ENDPOINT SECURITY VPN agent, which is running on version E85 onwards, are "experiencing" problems of "outages and/or intermittency" in their connections.
The Hotfix package for this version is available in Take 237.
VPN users are AD users.
Is there an action plan that can be executed to help us determine whether or not the "intermittency" problem experienced by several users is the responsibility of the VPN solution?
Thanks for your support.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have some experience in this, as I worked with few customers having similar issues. Here are my questions for you:
1) Does it ever happen that client(s) connect and then get disconnected after about 20 seconds?
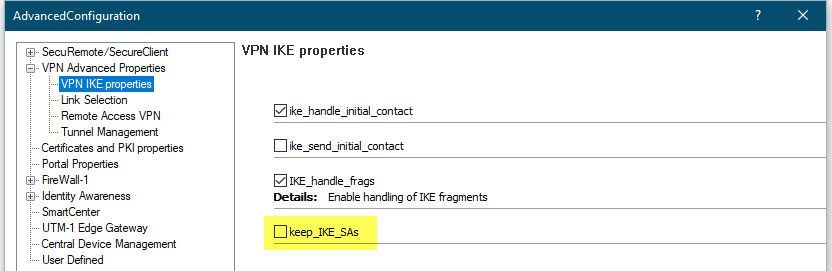
2) Do you have option "keep ike sas" enabled in global properties?
3) When did the issue happen?
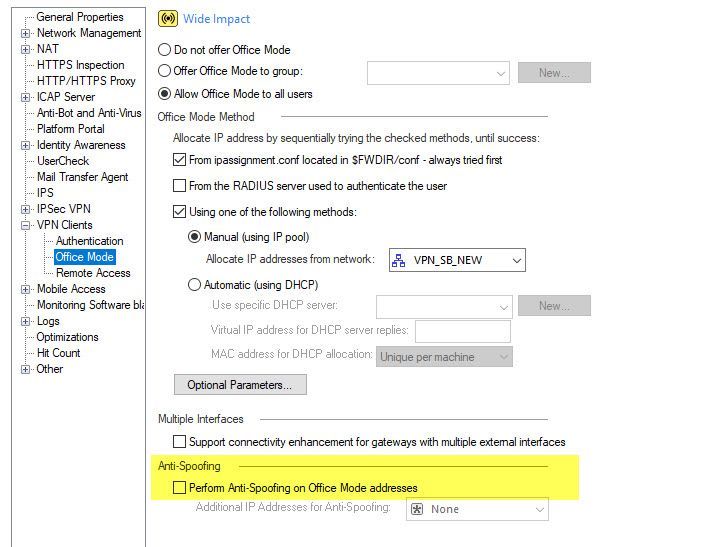
4) Do you have option enabled for anti spoofing on remote access tab under vpn in gateway properties?
5) When issue happens, can you run following command and see if you get anything -> fw monitor -e "accept port(18234);"
Cheers!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Buddy
Regarding your inquiries.
I detail the following.
1) No. The experience of users regarding the "Intermittence" is normally in a range of hours, approx. between 12:00 pm to 16:00 pm, almost every day.
2) I do not find this option. Can you give me the route to get to this option? I am working with a Standalone R80.30 architecture.
3) The problem has been occurring for days. In the time range that I detail as "approx" in the point # 1
4) I can't find this option. Can you give me the route to get to this option? I'm working with a Standalone R80.30 architecture.
5) I have not yet tested this command when the users intermittency problem occurs.
I will try it, and I will share my evidence.
I hope you can support me with the answers.
Thanks for your support.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, bear with me, Im on my personal macbook air, so as stupid as this sounds, since I have no clue how to take screenshot on it (haha), will just send you the answers how to get to those options...
to get to keep ike SAs -> from dashboard upper left side menu -> global properties -> advanced -> configure -> vpn advanced properties -> vpn ike properties -> "keep ike sas" at the bottom
for other option -> double click gateway object in dashboard -> vpn clients -> office mode -> perform anti-spoofing (at the bottom)
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, my friend.
I found both options, according to the detail you gave me.
I have both options disabled.
Having these options disabled, can it cause "INTERMITTANCE" problems?
If you activate these options, this can affect in something, the part of CPU, memory, etc?
My users, when they connect with AD user accounts, through the ENDPOINT SECURITY VPN.
Once connected to the VPN, they access their machine that is inside our network, by RDP.
It is at this point that, from one moment to another, they start experiencing problems with the VPN connections.
On "some" occasions the AGENT disconnects due to these problems, but this is not always the case.
To perform an UPGRADE from a STANDOALONE R80.30 to R81.10 environment, should we take into account the Hardware part of the Open Server?
Greetings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, as a matter of fact, having them disabled CAN cause intermittent issues, I had seen it few times. All you have to do is enable them and push policy. In R80+ code, all changes are saved, so you can always go back to previous policy revision if needed.
Also, I would upgrade to R81.10 and make sure to test newest E86.71 windows client or E86.70 if any user uses MAC. R81.10 has lots of vpn improvements, so it can only help you, plus, as phoneboy indicated, R80.30 is end of support, so getting any assistance from TAC would be very limited.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, The_Rock
I am going to apply your recommendations, but I have a curiosity.
The Endpoint Security VPN agents, I understand to this day, that these agents by default work with the IPsec protocol, is that correct?
If I'm not mistaken, the IPsec version they use is the IKEv1 version.
Unlike other vendors, I have noticed that for all users it is "transparent" the fact that their agents are working with IPsec, because they only enter "User and Password". I guess this is Checkpoint's way of working.
A curiosity,
Can the practice of changing the IKE version be "valid" for the problem of intermittency?
That is to say, to work with IKEv2?
Do you think it is a valid option?
Greetings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
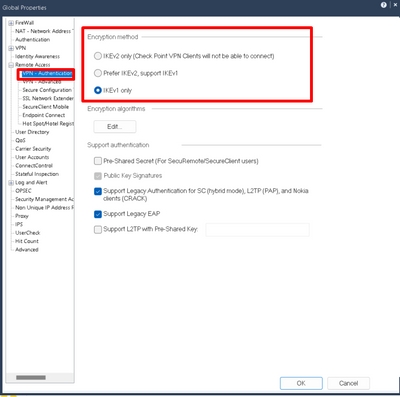
The Check Point VPN client does not use IKEv2 currently, so this is a non-issue.
Having Keep IKE SAs disabled could cause an issue if you make policy changes regularly during when users are connected.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
As far as I understand, according to theory, the ENDPOINT SECURITY VPN Client, works by default with IKEv1 (This is transparent to all users), so far, so good.
My question is, is it possible to tell the Endpoints, from the Smartconsole, to work the clients installed in the PCs of the users, with IKEv2, to make a test, and validate if the problem of the "intermittence" in all the users, improves?
Thanks for your comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As phoneboy said, ikev2 would not work with endpoint...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand.
The first 2 options, I did not "interpret" well.
The first option, I understand that even if we select it, the clients will not be able to connect.
It was a misinterpretation I think. haha
I am going to run anyway, as a test, your recommendations.
The VPN intermittency problem is a headache. 😥😔
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apple + Shift + 3 or 4 8)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I googled it after lol
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30 is End of Support.
E85 Endpoint client is fairly old as well.
Probably a good idea to upgrade to a supported release on both ends.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
phoneboy brings up a good point...definitely test newest VPN client, E86.71, worth a shot, just to rule it out.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter