- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- How to configure VPN Remote Access on non-default ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to configure VPN Remote Access on non-default Internet Link
Security Engineering Brazil
April, 2020
Version 02
Author:
Thiago Mourao, SE and Cyber Security Evangelist
Revision:
Henrique Moises, SE
Contents
How to configure VPN Remote Access on non-default Internet Link
Know Limitation and Requirements
Configure Remote Access to respond for non-default Internet Link.
As default configuration, when the first packet arrives from the non-default internet link, gateway will check its routing table and will reply those packets using the default route and after that the packets will be sent to the interface where the default route is configured. In many cases, those packets will be blocked by the next hop due to Out of State (SYN-ACK without SYN) or due to ingress routing filter that will check that the source do not belong to that route/network.
PS: In a specific scenario this configuration might work with no further actions needed. In this scenario, the primary ISP link do not check Stateful Inspection or dot have Ingress Routing Filter to block spoofing/DDoS attacks, so in that case the security level is going to be lower, hence not recommended.
Know Limitation and Requirements
- I have used static-route on this example instead of PBR that would be a more granular way to be done
- I have used a wrapper for cprid_util created by @HeikoAnkenbrand (HeikoAnkenbrand) on his article on Check Mates called “GAIA - Easy execute CLI commands from management on gateways” (https://community.checkpoint.com/t5/Enterprise-Appliances-and-Gaia/GAIA-Easy-execute-CLI-commands-fr...) to execute command on gateway from the SMS
- For this PoC we assume that you already have configured a gateway with 2 (two) internet links where the first one is the default route and the second one is a backup link
- For this PoC we assume that you already configured Remote Access VPN (IPsec or Mobile Access) to respond with the IP of the secondary internet link
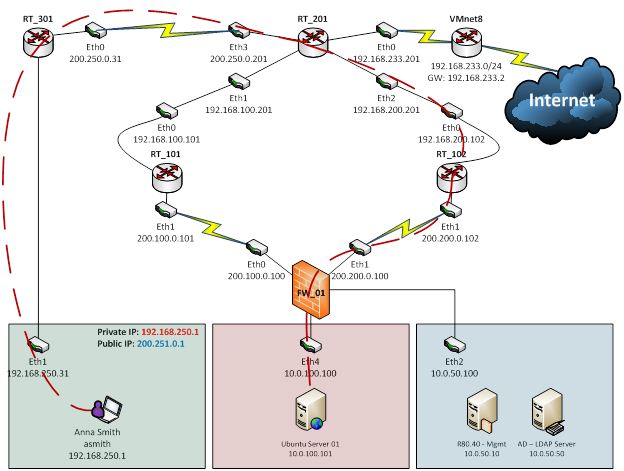
Topology
In this lab we are using R80.40 on both Security Gateway and Manager, and they were virtualized on VMware Workstation 12.
Virtual Environment:
- 1 x Check Point Gateway R80.40
- 1 x Check Point Manager R80.40
- 1 x Microsoft Windows Server 2012 R2
- 1 x Windows 7 Ultimate
- 4 x Virtual Routers (VyOS)
Host Environment:
- 1 x Notebook (Windows Professional) with VMWare Workstation 12
NAT:
- In this topology, Router RT_301 is doing source NAT FROM: 192.168.250.1 TO: 200.251.0.1
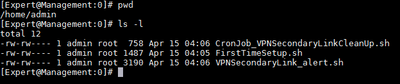
FirstTimeSetup.sh
This script will prepare the environment to be run for the first time.
|
#!/bin/bash -f echo "First time setup" echo "Creating Directories"
echo "Creating Symbolic Links" echo "Copying Scripts to $EXECDIR" echo "Changing Owner and Group" echo " Changing Permission" echo "Lock Database Override" |
VPNSecondaryLink_alert.sh
This Script will be called by the Track field of the rule created in the SmartConsole, then the output is being parsed, creating the static route based on the source IP of the packet that hit the rule
|
#!/bin/bash -f #Jump to Script Directory #Global Variable echo "#### Executing VPNSecondaryLink_alert at $(date -u) ####" echo "Reading input from rule" |
CronJob_VPNSecondaryLinkCleanUp.sh
This script will be executed by the Job called VPNSecondaryLinkCleanUp on Crontab to backup current VPNSecondaryLinkCleanUp.sh to save for historical purpose and run the current VPNSecondaryLinkCleanUp.sh to Clean Up the routing table every day.
|
#!/bin/bash -f #Jump to Script Directory |
- Copy the 3 (three) scripts to the Manager Server (SMS)
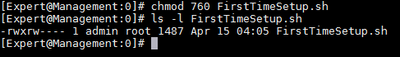
- Change permission of “FirstTimeSetup.sh”
[Expert@Management:0]# chmod 760 FirstTimeSetup.sh
[Expert@Management:0]# ls –l FirstTimeSetup.sh
- Execute the “FirstTimeSetup.sh”
[Expert@Management:0]# ./FirstTimeSetup.sh
- Check if CRON JOB was created
[Expert@Management:0]# more /var/spool/cron/admin
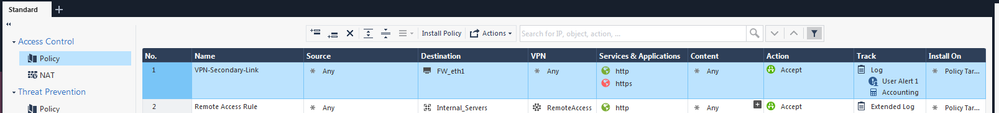
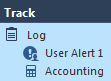
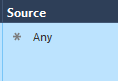
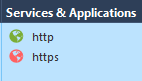
- Create an Access Control Rule with the following pattern:
From: ANY
To: IP_of_the_Backup_Interface (My Example: 200.200.0.100)
Services: HTTP and HTTPS
Action: Permit
Track: Log / Alert:User Alert 1

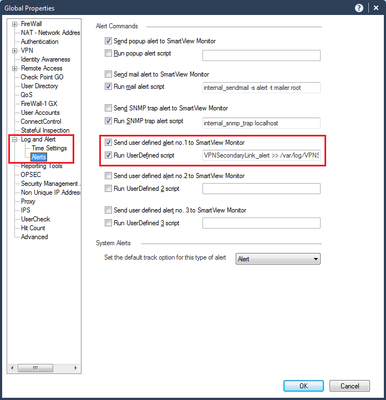
- Check the Alert Commands Parameters on Global Properties → Log and Alert → Alerts:
- “Send user Defined alert no. 1 to SmartView Monitor”
- “Run UserDefined script”
- VPNSecondaryLink_alert >> /var/log/VPNSecondaryLink_alert.log 2>&1
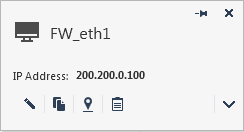
- Creating a VPN on Remote Client using IP from the non-default interface (Ex.: Eth1 – 200.200.0.100)
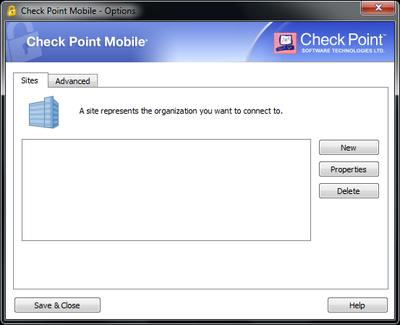
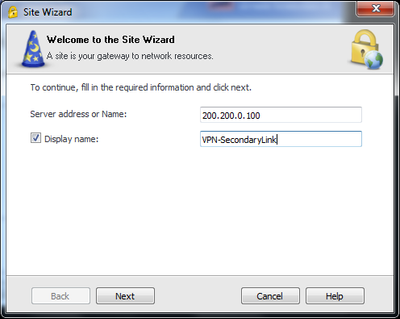
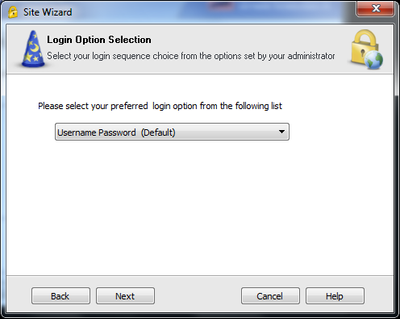
- Connecting to the VPN

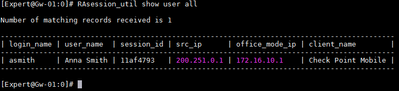
- Checking if Remote Client connected successfully and got Office Mode IP from the Pool
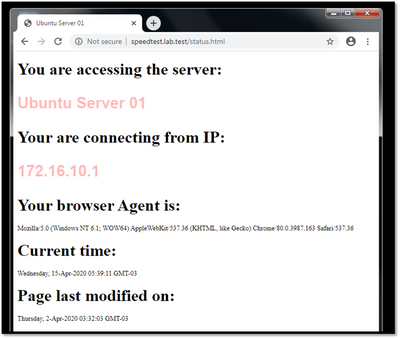
- Checking access to internal resource (Ex.: Ubuntu Server 01)
PS: This page was created to check de IP address from Client
PPS: This is the server called Ubuntu Server 01 and its private IP is 10.100.0.101
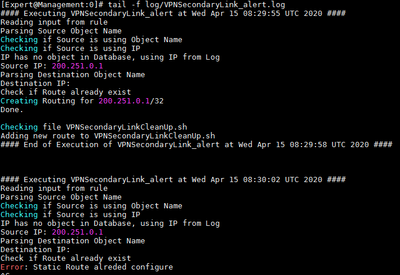
- Checking on the VPNSecondaryLink_alert.log file to see if the scripts are running
[Expert@Management:0]# tail –f log/VPNSecondaryLink_Alert.log
PS: There is a symbolic link on $EXECDIR/log/ VPNSecondaryLink_alert.log. The original file was created on /var/log/VPNSecondaryLink_alert.log
- Checking the Behavior
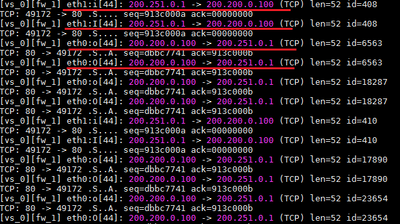
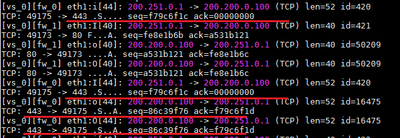
You can see on fw monitor output that VPN Client started to send packets to 200.200.0.100 that arrived on interface Eth1 and the gateway Gw-01 responded those packets through interface Eth0. Due to Stateful Inspection on route RT_101, packets were drop and never reach the VPN Client.
When the script run a static route is inserted and then packets from gateway Gw-01 to the IP 200.250.0.1 started to be routed through interface Eth1.
After responding to TCP 80 (HTTP), visitor mode could be reached creating the site on the VPN Client.
- Checking the new routing table on gateway
Gw-01> show configuration static-route
- Running the Clean Up Script (CronJob_VPNSecondaryLinkCleanUp.sh)
[Expert@Management:0]# ./CronJob_VPNSecondaryLinkCleanUp.sh
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great stuff, @Thiago_Mourao ! Well done!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Loukine!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could Policy-Based Routing be used to accomplish the same goal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is limitation between PBR and Remote Access VPN/S2S VPN...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this nice set of scripts + documentation!
I found some flaws:
a) all provided scripts are not FW version independent: use /opt/CPshared/5.0/tmp/.CPprofile.sh to source the environment variables
b) FirstTimeSetup.sh : in this script you create a symbolic link to $FWDIR/bin/VPNSecondaryLink_alert
but later on you refer to $FWDIR/bin/VPNSecondaryLink_alert.sh ( see lines with "chown" and "chmod")
c) /usr/local/bin/g_cli (from Wolfgang) does not find all gateway IPs (line range too narrow with grep, Fix: use "grep -A 25" )
d) there is no hint about ISP redundancy feature - typically customers are using this feature, too - when having two ISP links.
An additional objective for this subject is ,that users have only 1 VPN RA site created, but if the primary IP/link goes down, it should use the second link ( failover to the secondary link automatically) - like MEP is working, (when having more than 1 GW )
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter