Security Engineering Brazil
April, 2020
Version 02
Author:
Thiago Mourao, SE and Cyber Security Evangelist
Revision:
Henrique Moises, SE
Contents
How to configure VPN Remote Access on non-default Internet Link
Objective
Know Limitation and Requirements
Topology
Scripts
Step by Step
Objective
Configure Remote Access to respond for non-default Internet Link.
As default configuration, when the first packet arrives from the non-default internet link, gateway will check its routing table and will reply those packets using the default route and after that the packets will be sent to the interface where the default route is configured. In many cases, those packets will be blocked by the next hop due to Out of State (SYN-ACK without SYN) or due to ingress routing filter that will check that the source do not belong to that route/network.
PS: In a specific scenario this configuration might work with no further actions needed. In this scenario, the primary ISP link do not check Stateful Inspection or dot have Ingress Routing Filter to block spoofing/DDoS attacks, so in that case the security level is going to be lower, hence not recommended.
Know Limitation and Requirements
- I have used static-route on this example instead of PBR that would be a more granular way to be done
- I have used a wrapper for cprid_util created by @HeikoAnkenbrand (HeikoAnkenbrand) on his article on Check Mates called “GAIA - Easy execute CLI commands from management on gateways” (https://community.checkpoint.com/t5/Enterprise-Appliances-and-Gaia/GAIA-Easy-execute-CLI-commands-fr...) to execute command on gateway from the SMS
- For this PoC we assume that you already have configured a gateway with 2 (two) internet links where the first one is the default route and the second one is a backup link
- For this PoC we assume that you already configured Remote Access VPN (IPsec or Mobile Access) to respond with the IP of the secondary internet link
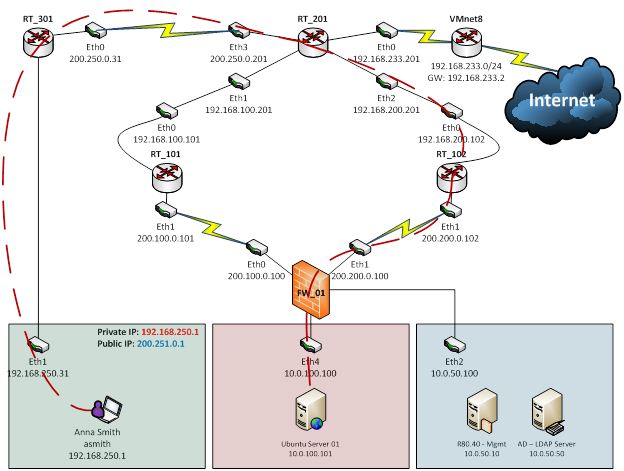
Topology
In this lab we are using R80.40 on both Security Gateway and Manager, and they were virtualized on VMware Workstation 12.
Virtual Environment:
- 1 x Check Point Gateway R80.40
- 1 x Check Point Manager R80.40
- 1 x Microsoft Windows Server 2012 R2
- 1 x Windows 7 Ultimate
- 4 x Virtual Routers (VyOS)
Host Environment:
- 1 x Notebook (Windows Professional) with VMWare Workstation 12
NAT:
- In this topology, Router RT_301 is doing source NAT FROM: 192.168.250.1 TO: 200.251.0.1
Scripts
FirstTimeSetup.sh
This script will prepare the environment to be run for the first time.
|
#!/bin/bash -f
source /opt/CPshrd-R80.40/tmp/.CPprofile.sh
#Script Directory
EXECDIR="/home/admin/VPNSecondaryLink"
#User that will Execute the Scripts and Cron Job
EXECUSER="admin"
echo "First time setup"
echo "Creating all files and Gaia configuration"
echo "Creating Directories"
mkdir $EXECDIR
mkdir $EXECDIR/log
mkdir $EXECDIR/tmp
echo "Creating Files"
touch $EXECDIR/CronJob_VPNSecondaryLinkCleanUp.sh
touch $EXECDIR/VPNSecondaryLinkCleanUp.sh
touch $EXECDIR/VPNSecondaryLink_alert.sh
touch $EXECDIR/log/CronJob_VPNSecondaryLinkCleanUp.sh.log
touch /var/log/VPNSecondaryLink_alert.log
echo "Creating Symbolic Links"
ln -s /var/log/VPNSecondaryLink_alert.log $EXECDIR/log/VPNSecondaryLink_alert.log
ln -s $EXECDIR/VPNSecondaryLink_alert.sh $FWDIR/bin/VPNSecondaryLink_alert
echo "Copying Scripts to $EXECDIR"
cp ./CronJob_VPNSecondaryLinkCleanUp.sh $EXECDIR/CronJob_VPNSecondaryLinkCleanUp.sh
cp ./VPNSecondaryLink_alert.sh $EXECDIR/VPNSecondaryLink_alert.sh
echo "Changing Owner and Group"
chown $EXECUSER:bin $EXECDIR/CronJob_VPNSecondaryLinkCleanUp.sh
chown $EXECUSER:bin $EXECDIR/VPNSecondaryLink_alert.sh
chown $EXECUSER:bin $FWDIR/bin/VPNSecondaryLink_alert.sh
echo " Changing Permission"
chmod 760 $EXECDIR/CronJob_VPNSecondaryLinkCleanUp.sh
chmod 760 $EXECDIR/VPNSecondaryLink_alert.sh
chmod 760 $FWDIR/bin/VPNSecondaryLink_alert.sh
echo "Lock Database Override"
clish -c "lock database override"
echo "Adding Daily Based Recurrence for CronJob_VPNSecondaryLinkCleanUp at Cron Job to 2:00am"
clish -c 'add cron job VPNSecondaryLinkCleanUp command "/home/admin/VPNSecondaryLink/CronJob_VPNSecondaryLinkCleanUp.sh >> /home/admin/VPNSecondaryLink/log/CronJob_VPNSecondaryLinkCleanUp.sh.log 2>&1" recurrence daily time 2:00'
echo "Saving clish configuration"
clish -c "save config"
|
VPNSecondaryLink_alert.sh
This Script will be called by the Track field of the rule created in the SmartConsole, then the output is being parsed, creating the static route based on the source IP of the packet that hit the rule
|
#!/bin/bash -f
source /opt/CPshrd-R80.40/tmp/.CPprofile.sh
#Script Directory
DIR="/home/admin/VPNSecondaryLink"
#User that will Execute the Scripts and Cron Job
EXECUSER="admin"
#Jump to Script Directory
cd $FWDIR/bin
#Global Variable
gateway_ip="10.0.50.100"
secondary_gw="200.200.0.102"
raw_pbr_error=0
error_msg1="Error: Object Name pattern founded on multiple Host Objects"
error_msg2="Error: Static Route alreded configure"
error_msg3="Error: Rule Name do not match"
error_msg4="Error: Object not found on management Database"
error_msg5="Error: Route Already Inserted on CleanUp Script"
echo "#### Executing VPNSecondaryLink_alert at $(date -u) ####"
[ $raw_pbr_error -gt 0 ] || {
echo "Reading input from rule"
read input
#echo "Troubleshooting enabled"
#echo $input > $DIR/tmp/VPNSecondaryLink_alert_tr.log
echo "Parsing Source Object Name"
echo "Checking if Source is using Object Name"
raw_src_name=$(echo $input | sed -n 's/.* src: \(.*\); dst: .*/\1/p')
#echo "variavel raw_src_name=$raw_src_name"
echo "Checking if Source is using IP"
raw_src_ip=$(echo "$input" | grep -o -P '.{0,5}(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)' | grep src | sed -n 's/^src: \(.*\)/\1/p' )
#echo "variavel raw_src_ip=$raw_src_ip"
firstocteto=$(echo "$raw_src_ip" | sed -n 's/\(^[[:digit:]]*\)\..*\..*\..*/\1/p')
#echo "variavel firstocteto=$firstocteto"
if [ -z $firstocteto ] || [ $firstocteto -gt 223 ]; then
echo "Cannot match with IP parsing... Trying to find IP on Management Object Database"
raw_src_ip=$(mgmt_cli -r true show objects limit 2 offset 0 order.1.ASC "name" in.1 "name" in.2 "$raw_src_name" order.2.DESC "objId" type "host" --format json | jq '.objects[]."ipv4-address"')
if [ -z $raw_src_ip ] ; then
echo $error_msg4;
raw_pbr_error=1;
exit 1;
elif [ $(echo "$raw_src_ip" | wc -l) -gt 1 ] ; then
echo $error_msg1;
raw_pbr_error=1;
exit 1;
else
echo "IP Founded"
raw_src_ip=$(echo "$raw_src_ip"| tr -d \");
echo "Source IP: $raw_src_ip"
fi
else
echo "IP has no object in Database, using IP from Log"
echo "Source IP: $raw_src_ip"
fi
echo "Parsing Destination Object Name"
raw_dst_ip=$eth1
echo "Destination IP: $raw_dst_ip"
echo "Check if Route already exist"
if [ $(/usr/local/bin/g_cli 10.0.50.100 show configuration static-route | grep "$raw_src_ip" | wc -l) -gt 0 ] ; then
echo $error_msg2;
raw_pbr_error=1;
exit 0;
else
touch $DIR/VPNSecondaryLinkCleanUp.sh
chmod +x $DIR/VPNSecondaryLinkCleanUp.sh
echo "Creating Routing for $raw_src_ip/32"
/usr/local/bin/g_cli $gateway_ip "set static-route $raw_src_ip/32 nexthop gateway address $secondary_gw on"
echo "Checking file VPNSecondaryLinkCleanUp.sh"
if [ $(cat /tmp/VPNSecondaryLinkCleanUp.sh | grep $raw_src_ip | wc -l ) -gt 0 ] ; then
echo $error_msg5;
raw_pbr_error=1;
exit 1;
else
echo "Adding new route to VPNSecondaryLinkCleanUp.sh"
echo "/usr/local/bin/g_cli $gateway_ip set static-route $raw_src_ip/32 off" >> $DIR/VPNSecondaryLinkCleanUp.sh
fi
fi
echo "#### End of Execution of VPNSecondaryLink_alert at $(date -u) ####"
echo -e '\n\n'
exit 1;
}
|
CronJob_VPNSecondaryLinkCleanUp.sh
This script will be executed by the Job called VPNSecondaryLinkCleanUp on Crontab to backup current VPNSecondaryLinkCleanUp.sh to save for historical purpose and run the current VPNSecondaryLinkCleanUp.sh to Clean Up the routing table every day.
|
#!/bin/bash -f
source /opt/CPshrd-R80.40/tmp/.CPprofile.sh
#Script Directory
DIR="/home/admin/VPNSecondaryLink"
#User that will Execute the Scripts and Cron Job
EXECUSER="admin"
#Jump to Script Directory
cd $DIR
touch $DIR/VPNSecondaryLinkCleanUp.sh
if [ $(cat $DIR/VPNSecondaryLinkCleanUp.sh | wc -l ) -gt 0 ] ; then
echo "Coping old VPNSecondaryLinkCleanUp to TMP Diretory for historical purpose"
cp $DIR/VPNSecondaryLinkCleanUp.sh $DIR/tmp/VPNSecondaryLinkCleanUp-$(date +%s).txt
echo "Executing VPNSecondaryLinkCleanUp.sh to CleanUp Routes"
$DIR/VPNSecondaryLinkCleanUp.sh
echo "Erasing Old VPNSecondaryLinkCleanUp.sh"
> $DIR/VPNSecondaryLinkCleanUp.sh
else
echo "Current VPNSecondaryLinkCleanUp.sh is already empty. No routes to be cleaned"
fi
|
Step by Step
- Copy the 3 (three) scripts to the Manager Server (SMS)
- Change permission of “FirstTimeSetup.sh”
[Expert@Management:0]# chmod 760 FirstTimeSetup.sh
[Expert@Management:0]# ls –l FirstTimeSetup.sh
- Execute the “FirstTimeSetup.sh”

[Expert@Management:0]# ./FirstTimeSetup.sh
- Check if CRON JOB was created

[Expert@Management:0]# more /var/spool/cron/admin
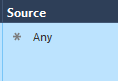
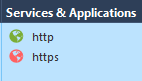
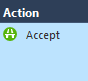
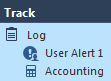
- Create an Access Control Rule with the following pattern:
From: ANY
To: IP_of_the_Backup_Interface (My Example: 200.200.0.100)
Services: HTTP and HTTPS
Action: Permit
Track: Log / Alert:User Alert 1
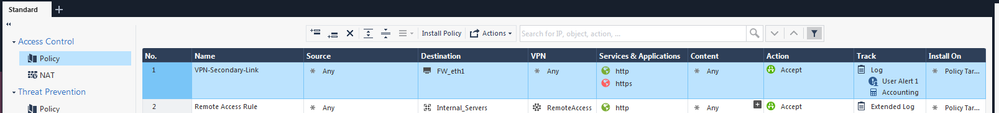


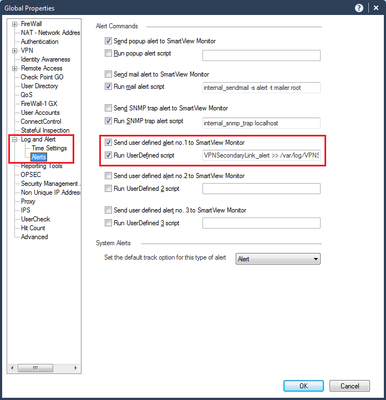
- Check the Alert Commands Parameters on Global Properties → Log and Alert → Alerts:
- “Send user Defined alert no. 1 to SmartView Monitor”
- “Run UserDefined script”
- VPNSecondaryLink_alert >> /var/log/VPNSecondaryLink_alert.log 2>&1
- Creating a VPN on Remote Client using IP from the non-default interface (Ex.: Eth1 – 200.200.0.100)
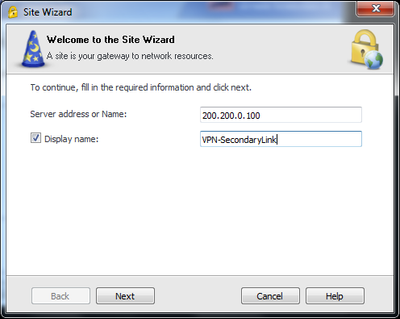
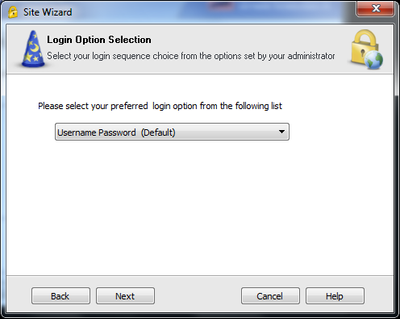



- Checking if Remote Client connected successfully and got Office Mode IP from the Pool
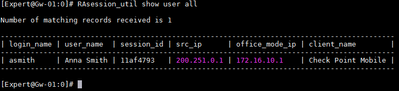
- Checking access to internal resource (Ex.: Ubuntu Server 01)
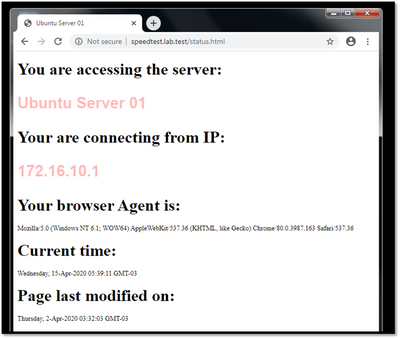
PS: This page was created to check de IP address from Client
PPS: This is the server called Ubuntu Server 01 and its private IP is 10.100.0.101
- Checking on the VPNSecondaryLink_alert.log file to see if the scripts are running
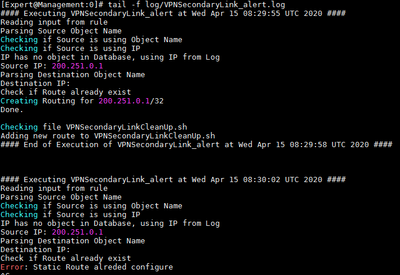
[Expert@Management:0]# tail –f log/VPNSecondaryLink_Alert.log
PS: There is a symbolic link on $EXECDIR/log/ VPNSecondaryLink_alert.log. The original file was created on /var/log/VPNSecondaryLink_alert.log
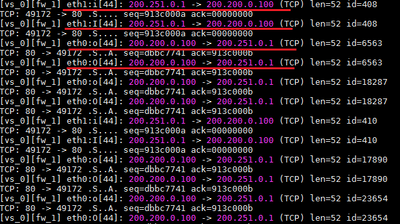
You can see on fw monitor output that VPN Client started to send packets to 200.200.0.100 that arrived on interface Eth1 and the gateway Gw-01 responded those packets through interface Eth0. Due to Stateful Inspection on route RT_101, packets were drop and never reach the VPN Client.
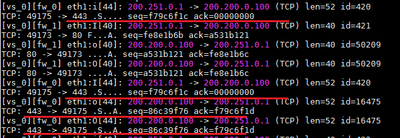
When the script run a static route is inserted and then packets from gateway Gw-01 to the IP 200.250.0.1 started to be routed through interface Eth1.

After responding to TCP 80 (HTTP), visitor mode could be reached creating the site on the VPN Client.
- Checking the new routing table on gateway

Gw-01> show configuration static-route
- Running the Clean Up Script (CronJob_VPNSecondaryLinkCleanUp.sh)

[Expert@Management:0]# ./CronJob_VPNSecondaryLinkCleanUp.sh
































