- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Changing the Certificate presented during End...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Changing the Certificate presented during Endpoint Security Client
Good day Mates
We are currently using the Check Point Endpoint Security, and during the Site creation, we are presented with a self-signed certificate. We wish to change that to a certificate signed by a CA.
Any idea on how that could be accomplished? we are using R80.20.
Thanks in advance
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure it can be changed and it is often necessary, if you have external partners connecting using a client VPN solution.
You have to first add the CAs, then create a CSR in the IPSEC VPN of the gateway.
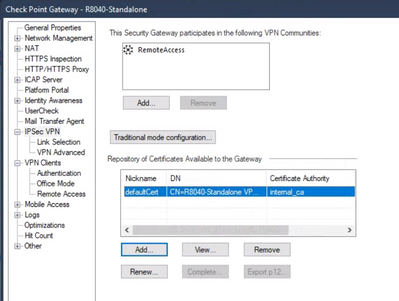
Here an example from my lab:
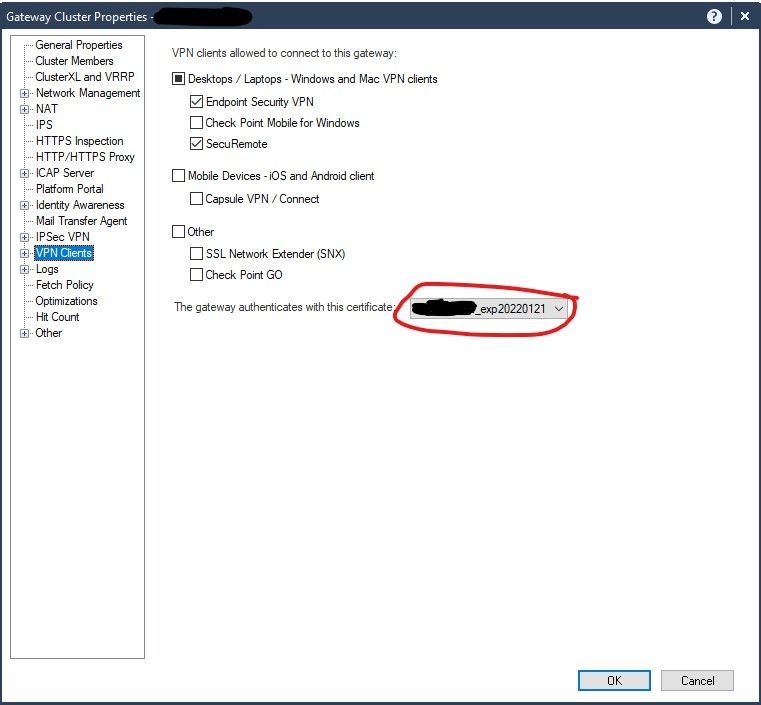
After completing the CSR, you can choose the certificate under "VPN Client":
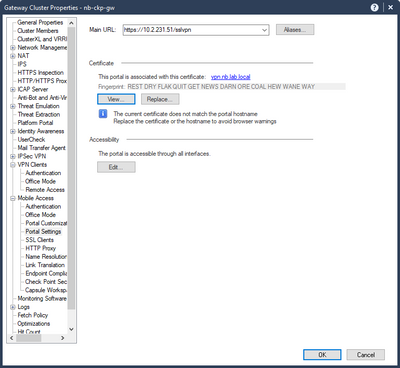
But if you have Mobile Access active and you change the certificate there on the MP daemon, you don't need this and it is also changed for VPN clients:
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why do you wish to change the CA used here exactly?
The key presented is signed by a Certificate Authority: the internal Check Point one.
As it is used for a lot of things (including VPN), the internal CA cannot be removed.
You also cannot replace the internal CA with an external one.
I know for site-to-site VPNs for third parties, you can specify which Certificate Authorities can be used for VPN.
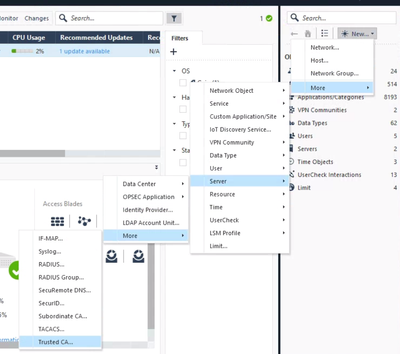
That's done here:
To add a different trusted CA, you need to create an object for it:
Whether that works for Remote Access VPN is a separate question.
Even if you could, I don't believe it changes the end user experience at all (i.e. they'll still get prompted to validate the site certificate when they first connect).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure it can be changed and it is often necessary, if you have external partners connecting using a client VPN solution.
You have to first add the CAs, then create a CSR in the IPSEC VPN of the gateway.
Here an example from my lab:
After completing the CSR, you can choose the certificate under "VPN Client":
But if you have Mobile Access active and you change the certificate there on the MP daemon, you don't need this and it is also changed for VPN clients:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
Thanks for your help.
Could you kindly tel me how to generate a CSR in the IPSEC of the gateway?
Thanks once again
Thanks for your help.
Could you kindly tel me how to generate a CSR in the IPSEC of the gateway?
Thanks once again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You click add, choose the right CA (has to be imported before), then enter details like DN and SAN.
After clicking ok, you can select the line with the new certificate and click view. Then you see the CSR.
You let your CA sign the CSR and then go back to this menu and click complete and paste the cert.
After clicking ok, you can select the line with the new certificate and click view. Then you see the CSR.
You let your CA sign the CSR and then go back to this menu and click complete and paste the cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbet
This is something I have not done before, so please where can I get the CA to be imported? and where is it imported from?
Thanks
This is something I have not done before, so please where can I get the CA to be imported? and where is it imported from?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This was already by Phoneboy above.
Just add an object called "Trusted CA" (and Intermediate if you have Sub CAs) and import the certificate of the CA.
Just add an object called "Trusted CA" (and Intermediate if you have Sub CAs) and import the certificate of the CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbet
I saw it thanks.
One final question, once the certificate is signed by CA, users will no longer get that Certificate Error Message when configuring VPN site right?
I saw it thanks.
One final question, once the certificate is signed by CA, users will no longer get that Certificate Error Message when configuring VPN site right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Users who are trusting the relevant CA will not receive a warning...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert,
Thank you for the above information, this is all very helpful. Silly question time, for the users trusting the relevant subordinate CA and CA, I assume this trust is validated using the respective CA certificates stored in the local machines Trusted Root Certification Authorities and Intermediate Certification Authorities certificate repository?
Then the remote client validates the certificate presented by the Gateway using this chain without prompting the user to trust the new/updated certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's correct to the best of my knowledge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Nobert!
I came to this forum last year and based on this discussion, I was able to gen a CSR and use a valid third-party certificate in my RA-VPN. Now I need renew my cert and form some reason, I'm getting an erro message that a similar cert is in use. I've tried different methods, but nothing seems to work.
I'm dropping a screenshot with the error for reference. Is there a way to gen a CSR without deleting the actual certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to delete it.
Just don’t push policy until you complete the procedure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok. Got it. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Phoneboy
Thanks for your feedback.
Just for knowledge purposes, I would like to know which other things uses this certificate.
Thanks for your feedback.
Just for knowledge purposes, I would like to know which other things uses this certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you only import for IPSEC VPN, it can only be used for VPN and Remote Access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
Thank you very much.
It worked...
Thank you very much.
It worked...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you have "mobile access" blade disabled, this setting is ignored, and it always uses the defaultCert from the internal CA...
no way to change the certificate for me... 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It might be that some other cert is used from another https portal.
Enabling one portal, changing certificate there and disabling it, might help.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter