- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- "show package tool" script fails with "Script stop...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
"show package tool" script fails with "Script stopped running due to severe error!" on R81
Hey mates,
I ran into a problem when trying to run the web_api_show_package.sh script. The same problem ist already discussed in sk164433, sk170414 and here. It worked several month ago. Usually i didn't give any flags. After reading the linked thread I ran the command for each layer individually and was able to narrow it down, but didnt solve the issue
According to sk170414 the problem was fixed in R81, but it seems to be the same or a similar issue. We are on:
Product version Check Point Gaia R81
OS build 392
OS kernel version 3.10.0-957.21.3cpx86_64
OS edition 64-bit
show_package.elg looks like this:
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: The parameters that were received: userRequestPackage:(-k)=fw_production
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Limit number of object per page: 10
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Local Ips: [192.168.x.x, 127.0.0.1]
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login As root: true
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login with 'read-only' flag.
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: Management API running version: 1.7.1
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: show_package v2.0.6
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: Chosen port: 443
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Chosen server IP: 127.0.0.1
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login response: {"api-server-version":"1.7.1","last-login-was-at":{"iso-8601":"2022-08-16T23:31+0200","posix":1660685491},"standby":false,"read-only":true,"url":"https:\/\/127.0.0.1:443\/web_api","sid":"iLPrOX35-yobq0bkcFB1c-fNgfOvYWQ2bNzHRYmqY1k"}
[8/17/22 8:55 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-gateways-and-servers' with details level 'full'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 26 gateways from 'show-gateways-and-servers'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.collectGatewaysInUseAndInstalledPolicies()INFO]: Found 25 gateways that have a policy installed on them
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-vpn-communities-star' with details level 'full'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-vpn-communities-meshed' with details level 'full'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 24 vpn communities
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.showPackages()INFO]: Show only a specific package (the one that was entered as an argument): 'fw_production'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Starting to process layers of package 'fw_production'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-package' fw_production' with details level 'full'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 2 access layer(s) in package: 'fw_production'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.buildLayers()INFO]: Access layer(s) that were found in package 'fw_production' are: fw_production Security, fw_production Application,
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 2 threat layer(s) in package: 'fw_production'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.buildLayers()INFO]: Threat layer(s) that were found in package 'fw_production' are: IPS, fw_production Threat Prevention,
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found nat layer in package: 'fw_production'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Handle access layers
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.showAccessRulebase()INFO]: Starting handling access layer: 'fw_production Security'
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-access-rulebase' with payload: {"uid":"b55bbe39-13fb-45d1-8a22-a4563c0c03e5","use-object-dictionary":true,"details-level":"full"}
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-access-rulebase] uid b55bbe39-13fb-45d1-8a22-a4563c0c03e5 : Starting execution of 39 tasks (with 2 executor(s))
[8/17/22 8:56 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-access-rulebase] uid b55bbe39-13fb-45d1-8a22-a4563c0c03e5 limit 10 offset 10 SUCCESSFUL
[8/17/22 8:57 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-access-rulebase] uid b55bbe39-13fb-45d1-8a22-a4563c0c03e5 limit 10 offset 380 SUCCESSFUL
[8/17/22 8:57 AM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-access-rulebase] uid b55bbe39-13fb-45d1-8a22-a4563c0c03e5 : Finished execution of 39 tasks
[8/17/22 8:57 AM com.checkpoint.mgmt_api.examples.MyLogger.severe()SEVERE]: Error: failed while creating policy package: 'fw_production'. Exception: null. Error message: null
[8/17/22 8:57 AM com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: Script stopped running due to severe error!
We are currently in a network redesign and there have been a lot of changes and i can certainly see the possibility that we have a monstergroup that breaks the script. However, I was unable to figure out, where exactly the script fails.
Hope you guys can give me some input.
Cheers,
D
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally got it working!! Culprit was a bad/wrong object being used in a NAT rule, which made the script fail.
Thanks for the insight.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you opened a TAC case?
I expect this will be required to get to the bottom of this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
I gave it to our support partner, who gave it to CP
Just had a call with tech support. There was no quick fix so far.
CP is going to check out the issue in the lab.
If there is a solution, i'll post
Cheers
D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I have the same issue. Script fails at some point when reading NAT policies.
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-nat-rulebase] uid null limit 10 offset 430 SUCCESSFUL
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-nat-rulebase] uid null limit 10 offset 440 SUCCESSFUL
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Command [show-nat-rulebase] uid null : Finished execution of 45 tasks
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.MyLogger.severe()SEVERE]: Error: failed while creating policy package: 'FW-INT'. Exception: null. Error message: null
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: Script stopped running due to severe error!
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: dirPath: /home/admin/21bbe9cd-44cf-4df5-8f8f-571f93fe6bfe
[9/29/22 5:25 PM com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: tarGzPath: show_package-2022-09-29_17-22-32.tar.gz
Did you get a fix from CP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I got feedback from CP but we havent been able to confirm that it solves the issue as we are not on T69 yet
This is the info we got:
I got a confirmation from Checkpoint that they replicated and solved the issue in their lab.First, please install the latest Jumbo Hotfix Take 69 in General Availability.
After that, please run "$MDS_FWDIR/scripts/override_server_setting.sh -e BYPASS_UNSUPPORTED_SMB_GW_CHECK true" command.
After this, cpstop;cpstart will be required. Then you can run the "$MDS_FWDIR/scripts/web_api_show_package.sh -k <policy_package_name>" and it will run successfully.
Good Luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the tip... I think there is something wrong with my NAT Policy, it keeps failing. If I leave it out, the script works.
This is a little frustrating... I really need to export for cleaning purposes. I miss the old webview utility!!! 😢
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally got it working!! Culprit was a bad/wrong object being used in a NAT rule, which made the script fail.
Thanks for the insight.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great to hear, but can you please elaborate what was wrong with that object in the NAT rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello _Val_,
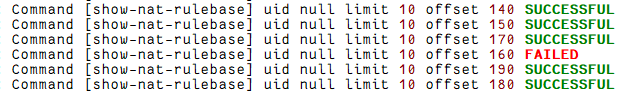
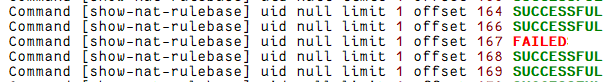
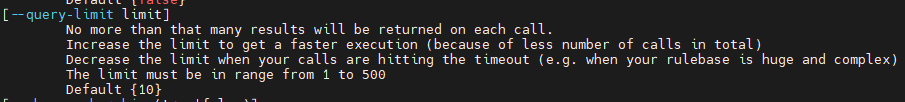
I suppose my case was an easy one to solve. After inspecting the resulting ELG file I noticed where the error was, at least the range as the script defaults to 10 results per call.
After running the script with a limit of 1 result per call, I was able to identify the exact rule number causing the error. Turns out, it had an interoperable device on the dst cell.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ZolocofxpHow did you run 1 by 1?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gman1229 ,
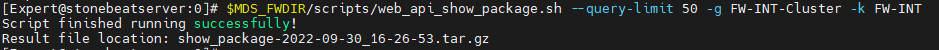
I did it using the --query-limit optional switch.
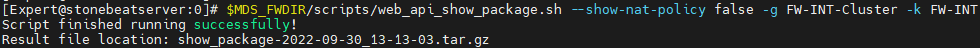
If you know which Policy(access, threat ot nat) the error resides in, you can set the --show-xx-policy switch to false so the script doesn't proccess them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ZolocofxpThank you for the follow up!
Additionally, was the Offset+1 the same as the rule number itself?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gman1229, yes, it matches the corresponding rule number, making it easier to spot the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ZolocofxpSorry for the quick follow up, so offset 112 = rule 112 or rule 113?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gman1229
Yes, it is offset value + 1. offset 112 would be rule No. 113 in Smart Console.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter