- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- fetch changed policy from management to gateway
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fetch changed policy from management to gateway
Hello folks,
after a misconfigured NAT we lost the abillity to push policy from Management to gateway.
We could revert the misconfiguration but now we can't install policy to the gateway, because there packets are NATed the wrong way. Access to the gateway is possible via another line and I did "fw fetch .....", but without success.
Following sk119332 I learned you can't fetch changed policies. This is new to me, I thought fw fetch loads the newest policy from management. But it fetched only the last installed policy of the gateway.
Question, are there any possibilities to fetch the changed policy from the management ?
We can't do an fw unloadlocal, we lost connectivity if we do this. Gateway is located in a remote datacenter.
Too we have connectivity to the smartcenter, but packets originating from management to the gateway are send the wrong way because of the problematic NAT. A policy push from management to gateway is not possible.
Any ideas are very welcome,
Thanks, Wolfgang
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does backup include also policy ? If yes, just revert the last backup and all should be fine 🙂
I guess that you don't have a snapshot to be reverted.
You mentioned that you cannot do "fw unloadlocal" ? Why not ? Are you using cluster configuration with 2 members in Active - Standby mode ?
If this is the case, then simply put Standby member into a permanent down state (clusteXL_admin down -p), do "fw unloadlocal" on down member, push policy (do not forget to uncheck setting that policy can be pushed if 1 member is not reachable) and you have policy installed on Down member. Bring this Down node back to production by clusterXL_admin up, perform failover and repeat steps on the former active node. It might be that node which was down will not go into Standby state, but it is because the policy is not the same on both members. Failover should be possible anyway.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is also an interesting solution to solve it by backup.
Nice!
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was just an idea, as I never tested such a solution yet.
Can someone confirm that the backups include also last policy files and once a backup is restored, the policy from backup is installed?
It is not clearly stated within Best Practices - Backup on Gaia OS
EDIT:
According to the following articles, policy should be restored:
Policy is not restored after a restore from backup
Objects and policies are not restored from Gaia Backup, although the restore operation succeeded
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Description "fw ctl uninstall"
- Tells the operating system to stop passing packets to Firewall.
- Unloads the current Security Policy.
- Unloads the current Firewall Chain Modules.
- Unloads the current Firewall Connection Modules
1) Install seriel cabel to configure the appliance remote or ILO for open server.
2) Run the "fw ctl uninstall" command, the networks behind the Security Gateway become unprotected.
3) Configure routes via clish over the seriel console or KVM
4) Install new policy
5) Run "fw fetch" and fetch the new policy from management server.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For remote access via console or ILO I always use a laptop with serial console or network. You can access the laptop via WLAN or LTE and Teamviewer.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko,
serial console is a good idea, but not possible at the moment.
Datacenter is more then 500km far from us and a long way to drive to configure one cable 😞
Something learned again this week... check your changes twice or more before install.
And did backups/snapshots everytime of major changes.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your recommendations.
We don’t have usable backups or snapshots available. I can’t do fw unloadlocal because I‘m connected over a second interface via a site 2 site vpn tunnel with another gateway. If I unload policy I loose the VPN.
We found a way to restore via snapshot.
1. Export of the smartcenter to our lab environment
2. Installed similar gateway hardware from our lab environment (i‘m happy having the same type available)
3. installed policy from recovered smartcenter to the gateway in our lab
4. Create a snapshot of the lab gateway
5. Transfered snapshot to the failing gateway and revert back to this.
6. Gateways reboots and everything was fine.
I‘m happy to not travelling around the country to get onsite to the appliance.
Thanks for help guys,
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Wolfgang , please check the status of your licenses on the getaway recovered from the snapshot created on alternate hardware. It is likely that the MAC addresses of the target have changed to the same as the gateway you have used to create the snapshot.
This being said, I really like this as a last resort recovery method and, with minor modifications, will keep it in my toolbox.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the management server is not behind that firewall, then you can use "cprid_util" tool and connect to the gateway over SIC.
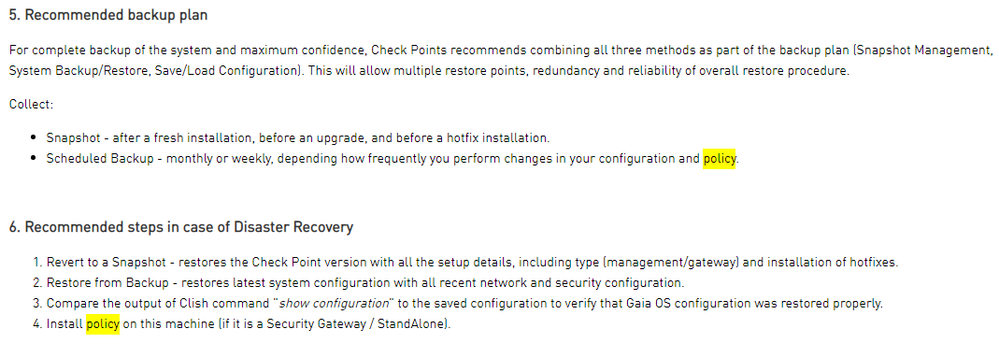
This is why disaster recovery solutions are MUST HAVE in place:
1. Working console connection (if console server is behind FW, NEVER put console server behind the firewall which you want to connect). The same applies to LOM.
2. Scheduled daily backup OUTSIDE of the box (Storage, NAS). In case of management - migrate export, mds_backup
3. Deploy cluster environments (2 cluster members minimum).
4. If possible, rack members in different rooms/racks/buildings/countries.
5. Management traffic should go via External interface, or dedicated interface (not via VPN).
6. Proper monitoring including syslog server in place (monitoring of RAID, PSUs, FANs, ...).
7. Create local users.
8. Do snapshot before a major change.
9. Test revert and restore periodically.
10. Document every change you did to the system and let the change be approved by someone else (more brains, fewer problems). Document also all passwords used (SIC, S2S secrets, local user passwords).
10. Reboot box every half a year.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter