- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Upgrade from R77.20 to R80.10,and failed to ve...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Upgrade from R77.20 to R80.10,and failed to verify policy.
Have you guys meet this situation?
The policy packages could install successfully.
But when I verify policies after upgrading to R80.10 ,I get a failure errors.
There are so many hide policy in R80.10.It could be about more than one thousands policies to be reported hide another policy.
Are there any methods to solve the problem?
Thanks&Regards,
Dawei Ye
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to update that sk120714 was created about the changes done in R77.30 and R80.10 regarding the "Rule Hiding Rule" logic that require a manual fix of of the rules mentioned in the verification error message.
This change will be documented also in the Behavior Change section of the CP_R80.10_ReleaseNotes.pdf document .
Thank you for your meaningful feedback and comments.
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do know the rule validation logic changed somewhat in R80.
Can you confirm this EXACT policy installed successfully with no errors prior to upgrading to R80.10?
Can you also confirm this policy installed successfully in R80.10 and did you see errors in this case?
It would be helpful if you could post the exact error messages you saw.
A screenshot of a couple of the rules in question might also be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Dameon,
this is the errors from two versions.It's from a same package.

I can't install policy in R80.10 due to the errors above.
and this is rules according to the first error.
the source and destination is the same.and only one service port hide.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To me, at least, this shouldn't trigger a verification failure.
It might be worth a TAC case.
That said, it looks like there is some opportunity for optimization, either using an inline layer and/or consolidating rules.
I also agree with https://community.checkpoint.com/people/jdanc6ca94357-c3d4-325b-9d5c-a8a71c5d2e9c that it's probably a good idea to look through the R80.x Upgrade Verification service to make sure there are no other issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For me it looks like, rule 119 hides rule 200 - because for the same ip-ranges (for source and target) the SAME port-range is again - even if the names are different.
tcp_31000-310100 in rule 119
and
tcp31001to31010 in rule 200
And with the same name of the port for the "Bionet-Setup".
Delete this port range in rule 200 rule (because this port-range seems to be a subset of the port-range in rule 119) and verifiy again. Let us know the result.
P.S.: Normally by defining a port-range (or single ports) it will be checked that the same range will not exists before, but it maybe that what was defined here was changed later (or because the range of rule 200 is a subset of the range in rule 119).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry I did a mistake .
the policy can only install in R77.20.And failed in R80.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dawei.
By chance did you use the R80 Upgrade Verification service to see if there would be any issues with porting your config into R80.x? If not, you might want to consider it because there are other hidden items that you might not know about.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Turns out rule matching logic isn't run as part of the Pre-Upgrade Verifier.
Further, I'm told the reason these rules validated in R77.20 at all is due to bugs that were fixed in R77.30 and R80.10.
In other words, this is working as designed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
oh……
I found it could be a bug yet.
even the exactly the same rule could install in R77.20.
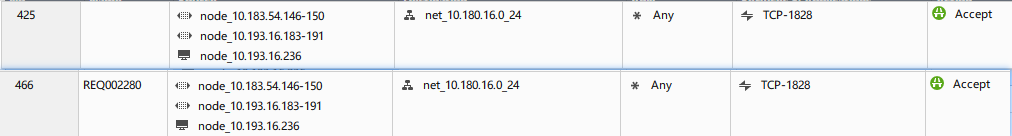
And Dameon, could you offer me some docs about the rule matching logic changing in R80.10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The actual logic should be the same, what's improved is the efficiency of validating that logic.
Two (or more) rules with the same source, destination, and service are not allowed and should cause a validation error.
The fact it did not do this in R77.20 was a defect corrected in R77.30 and R80.10.
Which explains why you are seeing those errors after upgrading to R80.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So there is no any way to correct the errors ?
I can just correct the validation error by hands?
anyway,Demeon, thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know there is no automated way to correct the issue.
They will need to be modified by hand.
Personally, I would take the opportunity to cleanup the policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which pretty much seems to support the idea of gettings things stable in R77.30 first before you considere migrating to higher versions.
You would have caught the issues in that stage.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Hugo,
woo……but for now ,if I upgrade to R77.30 first,I would still catch up with this issue.
I'd prefer to correct it in R80.10 directly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jason,
I ran some times in R77.20 with Pre-Upgrade Verifier(did R80 Upgrade Verification service means this? ).
It only some warning about non-English characters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From my prospective the upgrade verifier didn´t solve the issue. it is "just" a engine improvement of the rule verifier.
There is no automatic way to solve it as far as I know. Just correct manually and use the opportunity to clean-up.
This is the way we did it too.
Honestly this should been announced in the upgrade documents to be aware of and plan time for it.
Depends on the size of your Management area.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes.It should be announced in docs or some kind of SKs.
I have correct manually the packages for about 3 days .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Faced similar but this time MDM is running R77.30 Gaia. Is there any other possible way except manually fix the issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have this sort of issue (specifically "rule hiding" issues) the only way to fix them is manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Found out that R77.30 Gaia which does not include JHF faced issue with verifying the policy. Once jumbo hotfix installed, faced a lot of hiding rules even before moving to R80.10.
Sadly need to fix it manually which may takes days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dawei,
Have you considered that the amount of hidden rules might be an indication of making the policy too specific?
I tend to go to the situation where you need less rules and don't be go with rules like:
Src: Server-A, Dst: Server-B, Service: Port-C
Specifically with R80.10 I would considere to scratch such a polciy and rebuild your policy from the ground up.
Layered approach as a starting point. and try to keep away from micro management. Most certainly if you have to do it by hand.
Let IPS and such take care of part of the management.
I would like to see examples of how you can automate this with the API in a large network. It may still rresult in micro management but don't do this by hand.
Having worked with Telco solutions where no-one even actually configures every device by hand to define a Path from A to B for a service has shown me that we have a long way to go befor we see this in computer networks for most companies.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to update that sk120714 was created about the changes done in R77.30 and R80.10 regarding the "Rule Hiding Rule" logic that require a manual fix of of the rules mentioned in the verification error message.
This change will be documented also in the Behavior Change section of the CP_R80.10_ReleaseNotes.pdf document .
Thank you for your meaningful feedback and comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This behaviour also applicable to R77.30 without Jumbo hotfix.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


