- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Problem with HTTPS Inspection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Problem with HTTPS Inspection
Hi all,
I am new to Checkpoint, and I am having a hard time with the configuration of HTTPS Inspection.
Here my simple setup: I have a Security Gateway (R81) and Security Management Server installed on a VM with 2 interfaces (internal with hide NAT, and external). I have created the outbound certificate, and deployed it to the client, and enabled HTTPS Inspection.
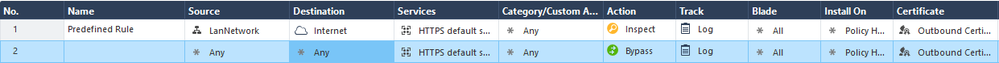
Here are the HTTPS Inspection policies I use:
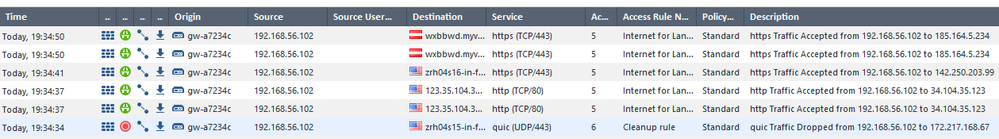
Browsing from the client works as expected, but browser still show the original certificate, not the one replaced from the gateway. Also the logs don't show anything:
In another post having the same problem, someone says "to enable https interception in the protocol tab", but I cannot find this option in any GUI. Is this what I am missing?
Anything else what I have possibly missed? Any help is highly appreciated.
Thank you, Iko
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just an update for this post...we did remote sesison and determined that wstlsd process was running, so no issues with firewall or https inspection and what was missing was simply a rule in policy to block a test site category, so we simply blocked gambling as a test from LAN and were able to see blocked page with the right cert.
Best,
Andy
Andy
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
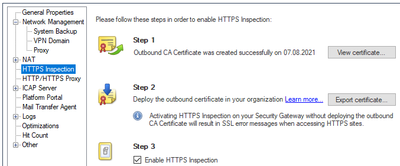
I assume you have enabled HTTPS Inspection on the gateway/cluster object itself under HTTPS Inspection...Step 3. Make sure that box is checked as you may have accidentally canceled out of that screen.
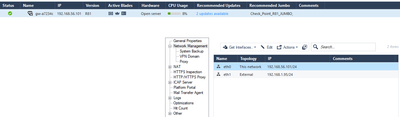
For object "Internet" to be applied properly in your HTTPS Inspection policy, you need to ensure that your network topology is completely and correctly defined under Network Management on your gateway/cluster object, specifically that the external interface is properly defined.
You may need to enable URLF to ensure the SNI category can be properly determined, but that may not matter here since you have "Any" set.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your time and help.
You assume right, HTTPS Inspection is enabled:
My topology looks all right I think:
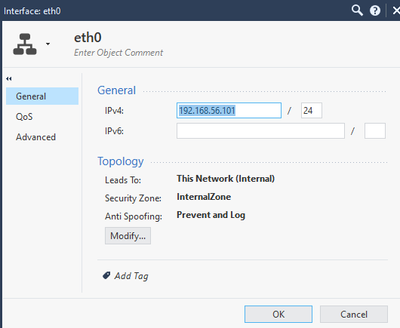
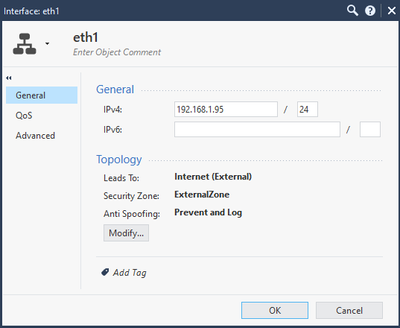
I also replaced the "Internet" object with "any" in my inspection policy, but doesn't change anything.
And I enabled URLF on the gateway and added URLF in category (in inspection rule).
Still no inspection happens.
Any other ideas left?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you run ps -ef | grep wstlsd are there any wstlsd processes running? If they are, please provide the log card for an accepted HTTPS connection that should have been inspected. Either your Internet traffic is not traversing the firewall the way you think, or possibly the web traffic is using QUIC instead of HTTPS. If there are no wstlsd process you have something still wrong in your config.
What code level and JHFA are you running, and have you tried other browser types to initiate traffic?
Edit: Corrected daemon name from wstld to wstlsd.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No there are no wstld processes running.
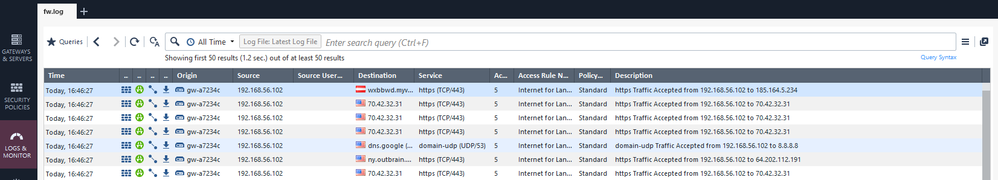
Internet traffic is definitely passing the firewall. Behind the firewall is another VM using host only adapter, which is directly connected to the internal interface. here some logs:
From these logs I would say it is using HTTPS (not QUIC). btw, the client is internet explorer which is afaik not using QUIC at all.
does the output below answer your question regarding code level and JHFA?
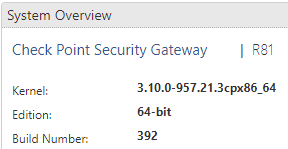
Thanks, Iko
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i installed now chrome, to doublecheck, the problem is not the used protocol
my rulebase doesnt even allow QUIC, but HTTPS works like a charm. just not intercepted 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like you are in a virtual environment, if the firewall itself is a VM how many cores are allocated? It needs to be at least 2 cores and 4GB of RAM (R81 minimum requirements), and it wouldn't surprise me if HTTPS Inspection would fail to operate unless there were at least 4 total cores (1/3 CoreXL split with dedicated functions per core so that 3 wstlsd process could be started in that case, as opposed to a 2-core setup with a 2/2 split and overlapping core functions).
While HTTPS Inspection is not itself a licensed feature, I assume you have a valid license installed otherwise? cplic print
Try disabling HTTPS Inspection on the gateway object, publish and reinstall, then enable it again, publish and reinstall. If it still doesn't work it will probably be time for a TAC case so they can run a debug and figure out why your firewall is essentially refusing to perform HTTPS Inspection.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2 Cores with 4 GB RAM is what i am using at the moment. Changed it to 4 cores now.
I am using a trial license:
gw-a7234c> cplic print
Host Expiration Features
=====================================================================
Check Point product trial period will expire in 13 days.
Until then, you will be able to use the complete Check Point Product Suite.
Please obtain a permanent license from Check Point User Center at:
https://usercenter.checkpoint.com/pub/usercenter/get_started.html
======================================================================
I disabled HTTP Inspection, published, reinstalled and re-enabled, published, reinstalled, but still no HTTPS inspection ongoing.
Am I allowed to open a TAC case with my trial license?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't see a way to open a TAC request with my trial license.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry can't help you with opening a TAC case, try hitting up your Check Point SE.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For a standalone VM, I recommend at least 16GB.
8GB is the absolute minimum.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If that process is not running, something is definitely wrong. I remember once I had similar issue with the customer and it turned out to be a setting that was inadvertently changed in GUidbedit tool itself. Do you remember changing anything there at all? I will try to see if I can find what setting it was...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
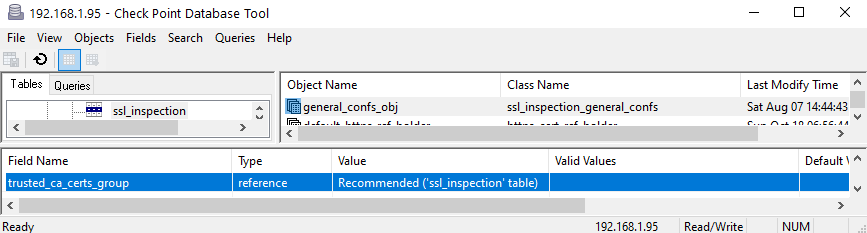
Got it...here is what I found in my notes (if you can check on this)
Make sure all SmartConsole connections are completely closed.
GuiDBedit > Other > ssl_inspection > general_confs_obj
The 'trusted_ca_certs_group' should refer to 'Recommended' from the same ssl_inspection table, so this must have been deleted on accident.
Simply right-click on the parameter > Edit, then in the Table drop-down select ssl_inspection and in the Object drop-down select Recommended
Save, close and then open SmartConsole and install policy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi the_rock, thanks for your advice. But I never changed anything with GuiDBedit.
The system I use is a fresh installation, and I just tried to setup HTTPS inspection in SmartConsole.
Anyway I verified it, the entry still exists
Any other advice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in the meantime I will try my luck with a new installation ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
new installation has the exact same problem -> no wstld processes -> no https inspection 😭
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That sucks...did you use same management server? Message me privately, I want to help you...we can do remote session when convenient.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a standalone gw and mgmt server on one virtual host. so I reinstalled everything from scratch today.
pm sent 😉 thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just an update for this post...we did remote sesison and determined that wstlsd process was running, so no issues with firewall or https inspection and what was missing was simply a rule in policy to block a test site category, so we simply blocked gambling as a test from LAN and were able to see blocked page with the right cert.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just a note to point it out: there was a typo 🙂
the process is called wstlsd
and that was running 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I corrected it in my prior post. I had a bit of a panic attack wondering if I had made the same mistake when mentioning that daemon in my book, but it was spelled correctly there. 😀
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No points taken for spelling mistakes...I never met any IT person who was good speller, no offense : ))
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 13 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter