- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Policy installation failed on gateway - (Error...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Policy installation failed on gateway - (Error code: 1-4000018)
Error Message on Policy Installation in Smartconsole: "Policy installation failed on gateway. If the problem persists contact Check Point support (Error code: 1-4000018)."
I never saw this error there is a solution?
In my research I did not find a solution.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly the same error appeared to me when I was installing the policy on R80.30 VPN gateway using the R80.40 management.
Analyzing all the policy changes from the time when policy installation was successful I realized that I edited the native application directly from SmartConsole instead of SmartDashboard. After deletion and recreation of the relevant (native application) object in the SmartDashboard, policy installation succeeded without any problems.
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Policy installation process likely needs to be debugged with TAC assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly the same error appeared to me when I was installing the policy on R80.30 VPN gateway using the R80.40 management.
Analyzing all the policy changes from the time when policy installation was successful I realized that I edited the native application directly from SmartConsole instead of SmartDashboard. After deletion and recreation of the relevant (native application) object in the SmartDashboard, policy installation succeeded without any problems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had the same issue. We edited a Native application in the Legacy dashboard. After we were seeing Policy installation failed on gateway - (Error code: 1-4000018). We created a new Native Application in Smart Console and updated the object in the Legacy Dashboard policy and was able to push. This was random though. We updated the Native application in Legacy dashboard a few times and wasn't seeing the policy actually update or getting the Policy installation fail. It wasn't until after 5 or 6 pushes we started seeing the Policy Installation fail. What we were seeing though is if you edit the object in Legacy dashboard it wasn't applying the new access to the gateway policy after a successful policy push to the gateway. Once we recreated the object in Smart Console and added the additional access everything worked as expected.
We are running R80.30 Gateway with Jumbo 214 with R80.40 Mgmt running jumbo 87
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm glad I found this post as there's nothing on SecureKnowledge. I've just had exactly the same issue too. R80.40 Mgmt and R80.30 gateways. I've been making loads of little tweaks to one native app today with no problems, and then boom, I get this error.
I deleted the native app and recreated it exactly the same again, and now policy installs again. Pheww.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had the same problem, but I did not delete and recreate the native application, what I did was the following:
1- I entered the smartDashboard
2- I opened the object/native application.
3- I changed anything or added anything.
4- Save
5- I published through the SmartConsole and installed policies in the SG
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree 100%...I did something very similar and it worked. Though one time, I just modified something trivial in policy and then it also worked. I thought this is stricvtly R81 issue, but I also saw it in R80.xx as well.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We just encountered this error for the first time today. The situation was similar, but not exactly the same.
A couple of weeks ago, an admin changed a native application using the smart dashboard. It was noticed some time afterwards that the native application was not working right. Over several days, other changes were made to the native application in an attempt to address the issue which culminated today in the 1-4000018 error. All these changes were made in Smart Dashboard.
After googling the error and reading this community article, the native application was examined in SmartConsole. The Allowed Locations Advanced settings were found to be blank, even though they looked fine in Smart Dashboard earlier.
The native application was updated in SmartConsole, the update was published, and the policy push was then successful. However, after that, other admins who were already in SmartConsole still found that native application's allowed locations to be blank. Each had to exit and re-start SmartConsole before the native application appeared correctly with the correct allowed locations.
We are using R80.40 HFA take 118 on both management and gateways
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yea, it seems to me like it could be random, as not everyone has this problem...maybe worth checking with TAC.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Has anyone "dealt" with this message when installing policies?
Policy installation failed on gateway - (Error code: 0-3-2000173-1)
I can't find the error code in the Check Point documentation.
Any idea how to solve it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey bro,
Never seen that exact error, but follow basic steps to check...SIC, routing, ping between gw and mgmt?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I opened a case with the TAC.
Apparently, it is an "incompatibility" error between a MGMT R81.20 and GW which are in version R81.10.
I will wait for them to confirm if this is something common or new that is happening.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What exactly do you mean "incompatibility"? Can you copy the response here?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was a comment made in a phone call.
I will have a remote session tomorrow.
I will update this post, so that it can be of help in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my opinion, such a statement is very broad and does not really explain as to what they were referring to. Anyway, keep us posted how remote goes bro.
Cheers,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Check Point Lovers 8)
Check Point, confirms that they have detected from several customers, an issue with R81.10.
The issue is about the installation of policies, and the error code that I exposed in this post.
Policy installation failed on gateway - (Error code: 0-3-2000173-1)
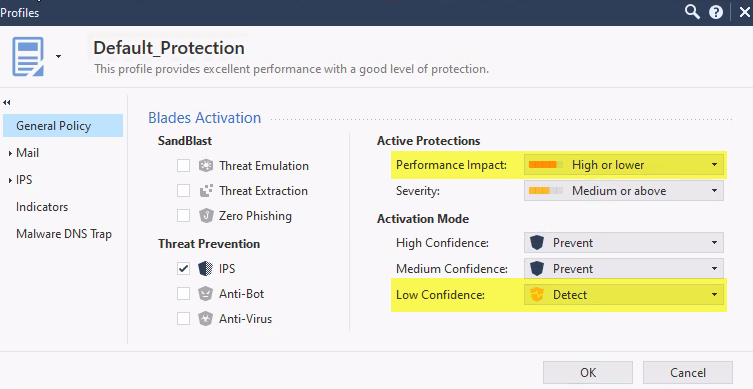
The temporary solution: Modify the IPS profiles you are working with in the GWs you have in production.
I leave the TAC instructions for this.:
1.fisrt of all we need to check if the gateway has a policy -
# fw stat
-check if it has the old policy/ Initial policy
If it has the old policy-
Change the IPS profile (on the profile section in TP policy) to -
Performance impact to :Medium and Lower and
Low confidence to : Inactive
After that please check you also change it in the custom policy.
Push the Policy.
If it don’t have policy-
1.Remove all the files from below directories on problematic gateway.
#rm -v $FWDIR/ips/update/0/*
#rm -v $FWDIR/ips/update/1/*
#rm -v $FWDIR/ips/update/2/*
2.Upload file "sd_updates.upf" under $FWDIR/ips/update/cur/ on problematic gateway from the case attachment ( sd_updates.udf)
3.Change IPS profile same as the first scenario.
4.Install access control policy and install TP policy.
Solution Description: 1.fisrt of all we need to check if the gateway has a policy -
# fw stat
-check if it has the old policy/ Initial policy
If it has the old policy-
Change the IPS profile (on the profile section in TP policy) to -
Performance impact to :Medium and Lower and
Low confidence to : Inactive
After that please check you also change it in the custom policy.
Check Point confirmed that its development area is working on a FIX to correct this problem.
At the moment, they have it "mapped" only in version R81.10.
I hope this will help you in the future.
Cheers 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats good to know bro! I will say that ever since R80 came out, I always keep telling customers to ONLY enable IPS blade in the ips profile they want to use, if they are not using any other features listed there.
Thanks for sharing the update...GRACIAS 🙌
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I met the issue with failed Access Control policy and Error code: 0-3-2000173-1 today on R81.10 VSX + MDS and based on your post I just changed these two options:
Performance impact to :Medium and Lower and
Low confidence to : Inactive
That way I was able to install the AC policy, but when I revert the IPS changes, installation fails again with the same error. So there is probably some broken IPS signature or something like that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yea, that would make sense.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter