- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Identity Awareness and AD
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Awareness and AD
Hi
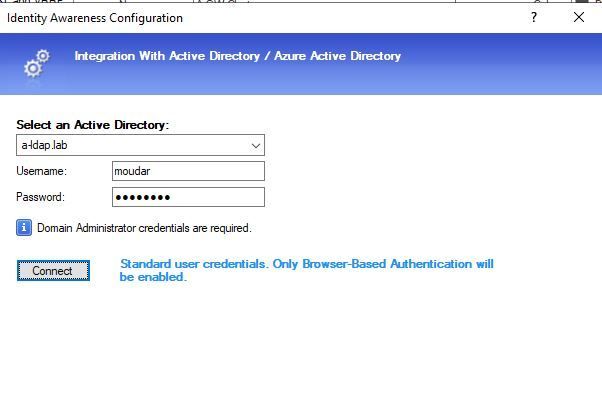
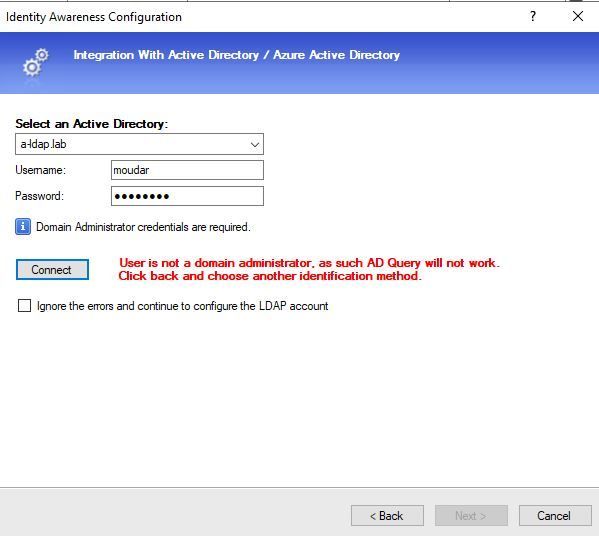
I am trying the Identity Awareness blade in my lab. when activating the Identity Awareness blade it says "Domain administrator credentials are required"
The AD account I am using to do that is a domain administrator, but even though i get this: "Standard user cerdentials"!
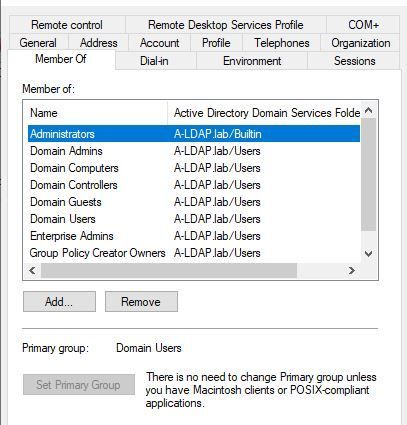
These are the groups that the AD account is member of:
What do I miss here?
Labels
- Labels:
-
SmartConsole
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I wonder why no one is looking at my problem!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Moudar
Maybe you can check this page.
"Important - For AD Query you must enter domain administrator credentials. For Browser-Based Authentication standard credentials are sufficient."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which Version/Jumbo & SmartConsole build is used in this environment?
Have you already performed troubleshooting such as sk91040?
Note Identity Collector (rather than ADquery) is the current recommended method for integrating AD with Identity Awareness.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am using this version:
show version all
Product version Check Point Gaia R81.20
OS build 631
OS kernel version 3.10.0-1160.15.2cpx86_64
OS edition 64-bitwhen I run: "adlog a dc" I get this:
[Expert@A-GW-01:0]# adlog a dc
Domain controllers:
Domain Name IP Address Events (last hour) Connection state
============================================================================================================
a-ldap.a-ldap.lab 192.168.11.101 0 connection had internal error [ntstatus = 0x80010111]
Ignored domain controllers on this gateway:
No ignored domain controllers found.I am 100% sure that the user is domain admin and the password is right!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
Is that recommended (or Best Practice maybe) documented anywhere, so that you can share a link or SK?
I agree with you but want to see if R&D have documented it anywhere.
Don
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure this is expected behavior in modern environments.
See: https://support.checkpoint.com/results/sk/sk91462
Specifically, if NTMLv2 is enabled (which is the default) this wizard will fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
adlogconfig a
- No configuration exists
[ ] Override configuration
[ ] Enable Adlog
[ ] Enable log for login or logoff
[ ] Use log original creation time
Association timeout : 0
Full Name Query Interval (days, 0=disabled) : 0
Full Name Fetch Hour : 0
Multi-user host Detection Threshold: 7
Revoked user timeout interval : 14400
[X] Enable Multi-User Host persistence DB
Multi-User Host persistence machine timeout (minutes): 2592000
Service Account Detection Threshold: 10
[ ] Automatically Exclude Service Accounts
[ ] Override default communication parameters
Query Within count : 0
Query Max returned objects in each iteration: 0
[X] Disable password expiration check
[ ] Authentication mode
[ ] Use NTLMv1
[X] Use NTLMv2
[ ] Single User Assumption
[ ] Don't report machines
[X] LDAP groups update notifications
Notifications accumulation time : 10 (sec)
[X] Notify only user-related LDAP changes
[ ] Prefer IPv6 DC addresses
[1] WMI query TypeAs you can see NTLMv2 is enabled.
I will follow sk91462 and come back with results
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
adlogconfig a
[ ] Override configuration
[ ] Enable Adlog
[ ] Enable log for login or logoff
[ ] Use log original creation time
Association timeout : 0
Full Name Query Interval (days, 0=disabled) : 0
Full Name Fetch Hour : 0
-------------------
Domain name : A-LDAP.lab
Username : moudar
Domain Controllers : A-LDAP.A-LDAP.lab
-------------------
Multi-user host Detection Threshold: 7
Revoked user timeout interval : 14400
[X] Enable Multi-User Host persistence DB
Multi-User Host persistence machine timeout (minutes): 2592000
Service Account Detection Threshold: 10
[ ] Automatically Exclude Service Accounts
[ ] Override default communication parameters
Query Within count : 0
Query Max returned objects in each iteration: 0
[X] Disable password expiration check
[ ] Authentication mode
[X] Use NTLMv1
[ ] Use NTLMv2
[ ] Single User Assumption
[ ] Don't report machines
[X] LDAP groups update notifications
Notifications accumulation time : 10 (sec)
[X] Notify only user-related LDAP changes
[ ] Prefer IPv6 DC addresses
[1] WMI query Type adlogconfig a -test A-LDAP.lab
Testing A-LDAP.A-LDAP.lab: Internal ErrorNow I am using NTLMv1 but still have problem with Identity Awareness Configuration wizard:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don’t believe the wizard supports LDAPS either, which I assume modern AD servers require.
However the wizard is not required to configure Identity Awareness.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I became sick of trying to use AD query.
Now I am using Identity collector and it is running well. But I needed to follow sk113021 to make it connect to the VIP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Did you try to use command test_ad_ connectivity from gateway?
I suggest to review or create the domain object directly.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter