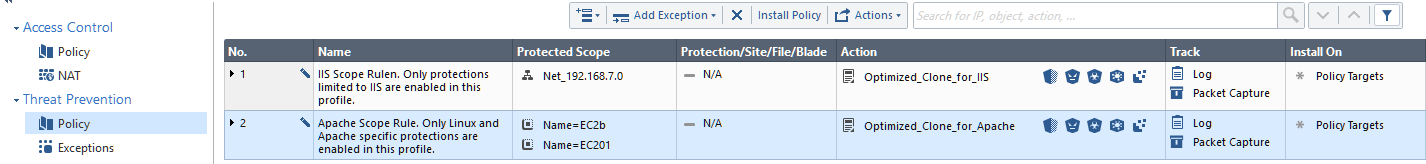
I've had a couple of gigs lately where I help clients migrate from R77.30 to R80.10 and I've taken interest in how to help them optimize the IPS while we're at it. Most installations I've encountered have the Recommended profile with a couple of exceptions for 2-3 services. Those already running R80+ have the Optimized profile with the same. Other than that it's all left the way it was out of the box. The optimized profile really does help improve performance! But, that's not why you have the IPS blade enabled.
I don't have much experience tuning the IPS since before, but now I really want to do something about all these out-of-the-box configurations left running.
When I look at an organizations IPS config I ask them what OS/Applications etc. they are running. I ask them how frequently they patch every individual OS/Application, and if there are any applications they cannot upgrade (read java) somewhere. Then I uncheck all the services that aren't present and all definitions/CVE that are older than 3 years for the present services.
This is something I just thought up myself. This approach could be crap for all I know, I just did something that felt feasible. If you patch your stuff, 3 year old bugs should not be a problem as long as you don't use software that is no longer supported. Right? Maybe 3 years is too short or too long, you tell me. Maybe that's only applicable to some software. Once again, what do you think?
That is the time-saving quick shave approach. But what should I do if I want to go more granular? Where do you guys look to stay updated? I mean, if you have 10 applications and OS's, no problem. But with large organizations it's a pain. Hence the quick shave.
Couldn't find a post like this so here I am. Hopefully others have this question as well.
/ Ilmo