- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Checkpoint to Fortinet VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checkpoint to Fortinet VPN
Kind of in a jam and need to get a tunnel up and running in short order. To make it worse its a non Checkpoint firewall with a dynamic outside interface. Now in the Juniper SRX world we accomplished this using aggressive mode.
One side is a large Checkpoint cluster running R80.10 . Obviously the outside interface has a static ip.
On the other side is a small Fortinet 60E-POE that will be in someones house. The WAN interface plugs into a Frontier DSL Modem ( ARRIS ) . The WAN interface will get a 192.168 address and be NAT'ed when it goes to the Internet.
I need a route based VPN setup between these two. Anyone do anything similar ? Have any guidance? Thanks.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe it'll require a certificate-based setup between peers:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to get the tunnel up . Had to create a certificate in the Checkpoint PKI export it and import it into Fortinet device. Also had to run the below solution to change what the CP presents when as the peer id when it connections.
(PS I didn't have to reboot as it says, just had to run the below)
Command will be “source $CPDIR/tmp/.CPprofile.sh”
I had to import the Checkpoint CA Cert into the Fortinet and add the Subject as CN = MyFirewallCertificate Name
Anyway, not P1 and P2 is up but I'm having a routing issue. I have a route that points the 192.168.0.0/16 network inside but the external VPN network is 192.168.51.0/24 . Since this is a more specific route it should take precedence but traffic is ping-ponging. Hitting the firewall and then being sent back in. I didn't create a specific static route as I assumed the connected VPN would create a dynamic one.
Any pointers on how to troubleshoot ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe that even if /24 is a more specific route, it is not necessarily a preferred one over "Connected" route.
Try modifying the topology of your gateway by creating a Network Group with Exclusions, (create two simple groups in advance, one containing 192.168.0.0/16 network and the other one containing 192.168.51.0/24):

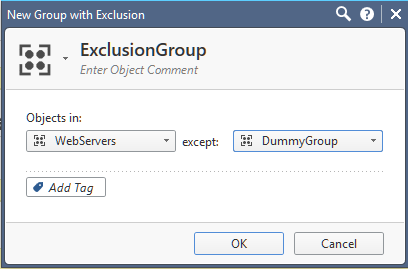
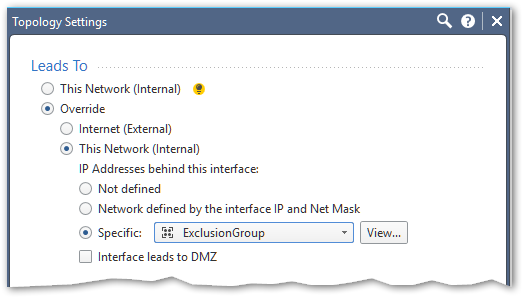
And see if this'll do the trick.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much, that actually worked in resolving the routing issue. The tunnel was actually up for a while and traffic was working in one direction. I believe it was probably some policy problem that wasn't getting it to work in the other direction. Now for some reason I don't understand the tunnel is failing to authenticate again. It's during the certificate authentication phase on the Fortinet side.
Validating X.509 certificate
peer cert, subject='CP-PROD VPN Certificate', issuer='-G-V'
peer ID does not match cert
certificate validation failed
We did the steps where you edit the .CPProfile.sh and instruct the firewall to send the FQDN as the peer id. Not sure if that helped or not.
Any other assistance is greatly appreciated. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Copper,
Can you guide me how did you configured the VPN between SRX and checkpoint? Our SRX routers we did configured aggressive mode with preshared keys but not sure which object in Checkpoint will go with this. We have tried interoperable device but if we select dynamic address it only accepts certificate based vpn. We are kinda stuck in this stage..
Thanks..
Adnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We do not support the use of pre-shared keys with a dynamic IP site-to-site VPN Endpoint, certificate Authentication must be used in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please direct me to a document describing configuration for certificate based site-to-site VPN with 3rd party vendor (Fortigate in our case) because it seems I'm not able to find related documentation..
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 14 | |
| 9 | |
| 6 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


