- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: cpsho_user config pushed from Check Point?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
cpsho_user config pushed from Check Point?
Hey everyone,
I noticed the following changes occurred the previous weekend. Some config changes got I assume pushed from Check Point.
I cannot find anything regarding this. I suspect there is a relation with HCP update from 19-7.
Anyone else has noticed this? Below the GAIA config, they are from 2 different customers.
add cron job wsc_cpm_monitoring command "sh /opt/CPsuite-R81.10/fw1/webconsole/wsc_cpm_monitoring.sh" recurrence daily time *:*
add user cpsho_user uid 1000 homedir /home/cpsho_user
set user cpsho_user gid 100 shell /etc/cli.sh
set user cpsho_user realname "Cpsho_user"
set user cpsho_user password-hash <HASH>
add cron job wsc_cpm_monitoring command "sh /opt/CPsuite-R81/fw1/webconsole/wsc_cpm_monitoring.sh" recurrence daily time *:*
add user cpsho_user uid 1000 homedir /home/cpsho_user
set user cpsho_user gid 100 shell /etc/cli.sh
set user cpsho_user realname "Cpsho_user"
set user cpsho_user password-hash <HASH>
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'd like to address several questions that have been raised in regars to cpsho_user.
What permissions and credentials cpsho_user has?
The password is randomly generated and it is 108 characters long, it is not stored anywhere, hence this user is never used to login. Gaia has the definition of the user, it has Non-root permission ( groupid 100 ).
When is cpsho_user created?
Installation of WebSmartConsole package will trigger the creation of the user. WebSmartConsole can be installed manually, by automatic update, and as part of the JHF.
Why is cpsho_user created?
cpsho_user is being created for internal system purposes. Several dockers on the MGMT server are using this low privileged user in order to read input files and write to log files. For example Infinity Services and WebSmartConsole.
Can cpsho_user be deleted?
Deleting this user is not recommended and might have impact on several Management features - Infinity Services, WebSmartConsole and SmartConsole (as some views and pages are of SmartConsole are based on WebSmartConsole as infrastructure)
More information available at sk181305 .
Best Regards,
Itai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The password is randomly generated per machine, it is very long and not kept after it is generated.
Therefore it is not a static password that anyone can use to log in.
Essentially, we defined this user in a way that no one will be able to use it to log in, under any circumstances. The random password is generated simply because that is needed to create the user.
It was created as a security precaution since it has lower privileges and it allows us to run some processes without full system permissions.
It retrospect, we understand that this was not clear to the field and we need to better communicate such underlying changes. We appreciate the feedback and will try to document this much better.
I want to emphasize though, that this does not introduce security concerns, to the contrary, it was done to tighten security.
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a system user account related to the web console, and some other management features, with R81.10 and above. Should only appear on management servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply Val. I am wondering how this config got there without interaction. It came a bit out of the blue.
Indeed I see the user only on mgmt systems.
Any idea how this config got pushed? And why does it need to run a task to monitor CPM?
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably via autopudatercli as the last release of the Web Smart Console is dated from July 18th, and makes mention of the tool for offline updates. Interestingly, the web Smart Console is not listed in the components of the autoupdatercli SK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'd like to address several questions that have been raised in regars to cpsho_user.
What permissions and credentials cpsho_user has?
The password is randomly generated and it is 108 characters long, it is not stored anywhere, hence this user is never used to login. Gaia has the definition of the user, it has Non-root permission ( groupid 100 ).
When is cpsho_user created?
Installation of WebSmartConsole package will trigger the creation of the user. WebSmartConsole can be installed manually, by automatic update, and as part of the JHF.
Why is cpsho_user created?
cpsho_user is being created for internal system purposes. Several dockers on the MGMT server are using this low privileged user in order to read input files and write to log files. For example Infinity Services and WebSmartConsole.
Can cpsho_user be deleted?
Deleting this user is not recommended and might have impact on several Management features - Infinity Services, WebSmartConsole and SmartConsole (as some views and pages are of SmartConsole are based on WebSmartConsole as infrastructure)
More information available at sk181305 .
Best Regards,
Itai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just discovered this new user on my management servers, to say I was surprised would be quite the understatement. Having an automated process that can randomly create new users on my management servers (no matter what permissions are set) is completely unacceptable and irresponsible on Check Point's part. We are heavily regulated and our management server configurations are audited. We must have justification for each and every user account on our management servers, how am I to explain this to an auditor? Check Point decided, for no reason that is well documented, to create this user? What's to stop Check Point from creating a different user account with different permissions?
We have automatic updates enabled on our management servers for IPS downloads, AppCtrl, etc. It would have been inconceivable to me that this would enable Check Point to create user accounts on my devices. I'm at a loss as to why Check Point would think this is acceptable.
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I couldn't agree more.
We're in the same situation like Dave, and having such user and cron job pushed by an auto-update process is unacceptable. It is still not clear to me from which update it came in; I first thought it was from JHF109 which we recently deployed, but 1st) I am not seeing it on our "offline" managers and 2nd) users were created before JHF109 deployment, so it must be any of cpuse, IPS, ... online update services.
This situation literally means we have lost control over granting access to our devices as the vendor can (and does!) push in any user required.
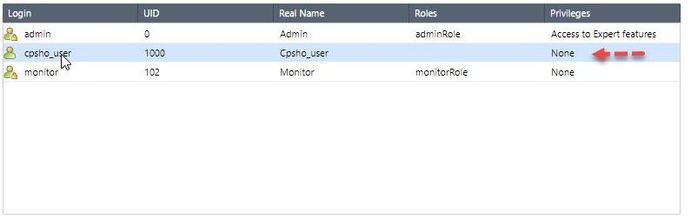
The explanation in the SK about what this user exactly does is vague ("used for internal processes"); also it does not list the exact permissions and "files read". According the SK it has "Non-root permission (groupid 100)", but when checking existing users for audits reports with "show users" command, it will show "Access to Expert features" on the Privilege tab, same as "admin".
Additionally, the SK was published three days _after_ users were pushed to our servers by "admin", so to me it looks as if Check Point had to quickly explain themselves.
For the cron job, it produces error messages when it runs (we get notified about failures on cron jobs); is there any QA on this before pushing out?
/opt/CPsuite-R81.10/fw1/webconsole/mwc.sh: line 153: service: command not found
/opt/CPsuite-R81.10/fw1/webconsole/mwc.sh: line 155: service: command not found
tail: cannot open '/opt/CPsuite-R81.10/fw1/log/wsc_cpm_monitoring.elg' for reading: No such file or directory
I'm quoting for truth:
@David_C1 wrote:[..]We have automatic updates enabled on our management servers for IPS downloads, AppCtrl, etc. It would have been inconceivable to me that this would enable Check Point to create user accounts on my devices. I'm at a loss as to why Check Point would think this is acceptable.
Dave
adding:
"and even more concerned they are even doing it".
I am really disappointed!
Mario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am guessing there is much more to this story than Check Point is telling us. This happened for a reason and the explanation is vague for a reason.
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Itai_Minuhin wrote:
Hello,
I'd like to address several questions that have been raised in regars to cpsho_user.
What permissions and credentials cpsho_user has?
The password is randomly generated and it is 108 characters long, it is not stored anywhere, hence this user is never used to login. Gaia has the definition of the user, it has Non-root permission ( groupid 100 ).
Not exactly true - the password is obviously stored on the local management server. Can the password be changed without causing "impact on several Management features"?
When is cpsho_user created?
Installation of WebSmartConsole package will trigger the creation of the user. WebSmartConsole can be installed manually, by automatic update, and as part of the JHF.
This account showed up on my management servers on a Sunday. WebSmartConsole was not manually installed on this day, nor was a JHF installed. What "automatic update" would trigger this?
Why is cpsho_user created?
cpsho_user is being created for internal system purposes. Several dockers on the MGMT server are using this low privileged user in order to read input files and write to log files. For example Infinity Services and WebSmartConsole.
How were these "internal system purposes" handled prior to the creation of this account? Why suddenly the need for this new account to handle these processes which presumably were working before this account showed up?
Can cpsho_user be deleted?
Deleting this user is not recommended and might have impact on several Management features - Infinity Services, WebSmartConsole and SmartConsole (as some views and pages are of SmartConsole are based on WebSmartConsole as infrastructure)
Again, these features were working prior to this account showing up. Could you provide more details about this potential impact?
More information available at sk181305 .
Best Regards,
Itai
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
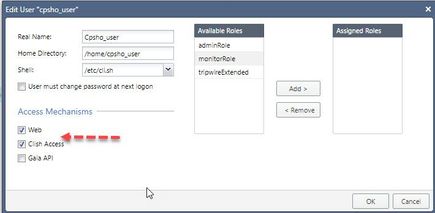
It appears that the only thing currently preventing a remote login (SSH/web UI) is the lack of an assigned role. If you change the password and try to login via SSH you get the following in /var/log/messages:
Aug 10 15:33:34 2023 fwmgr clish[23032]: User not logged in. He has no configured role.
Aug 10 15:33:34 2023 fwmgr clish[23032]: User cpsho_user logged out due to an error from CLI shell
Web UI gives "Permission denied"
If you assign an rba role it will happily log you in.
Either way, a vendor known static password (however long) deployed on a customer system without their consent is called a backdoor and is a security accident waiting to happen. Not what you expect from a security company.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re-reading this:
"The password is randomly generated and it is 108 characters long, it is not stored anywhere, hence this user is never used to login."
Randomly generate per-install, or once by Check Point? If it is not stored anywhere how can it be used, and why is a password needed at all?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The password is randomly generated per machine, it is very long and not kept after it is generated.
Therefore it is not a static password that anyone can use to log in.
Essentially, we defined this user in a way that no one will be able to use it to log in, under any circumstances. The random password is generated simply because that is needed to create the user.
It was created as a security precaution since it has lower privileges and it allows us to run some processes without full system permissions.
It retrospect, we understand that this was not clear to the field and we need to better communicate such underlying changes. We appreciate the feedback and will try to document this much better.
I want to emphasize though, that this does not introduce security concerns, to the contrary, it was done to tighten security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tomer_Noy wrote:
Hi,
The password is randomly generated per machine, it is very long and not kept after it is generated.
Therefore it is not a static password that anyone can use to log in.
True, but if this is the case, why was the user created with Web and Clish Access enabled?
Essentially, we defined this user in a way that no one will be able to use it to log in, under any circumstances. The random password is generated simply because that is needed to create the user.
It was created as a security precaution since it has lower privileges and it allows us to run some processes without full system permissions.
Details, please. What was previously running with full system permissions that had to be fixed with a named user? UID 1000 already existed, why the need for a named user? What bug was found (and not disclosed)?
It retrospect, we understand that this was not clear to the field and we need to better communicate such underlying changes. We appreciate the feedback and will try to document this much better.
Umm...yeah. Would this had ever been brought to light if a few of us didn't notice this additional user?
I want to emphasize though, that this does not introduce security concerns, to the contrary, it was done to tighten security.
Again, details would help restore some trust.
Also, an explanation between this discrepancy:
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have now seen 3 times at 3 different customers after upgrading from R81.10 to R81.20 we get Segmentation fault in clish when trying to back up, or after show configuration.
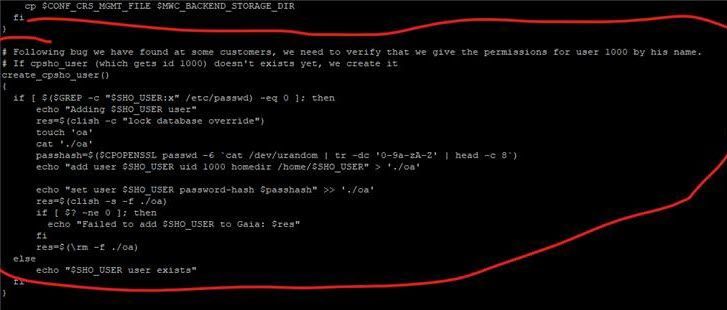
After some debug I pinpointed the problem. During the the upgrade process the user "Cpsho_user" is automatically created, but this user is created without a home dir:
[Expert@s-manage03:0]# grep "passwd:cpsho_user" /config/active
passwd:cpsho_user t
passwd:cpsho_user:realname Cpsho_user
passwd:cpsho_user:gid 100
passwd:cpsho_user:uid 1000
passwd:cpsho_user:lastchg 1694536445
passwd:cpsho_user:shell /sbin/nologin
passwd:cpsho_user:passwd *
In one installation I exported the configuration, reinstalled on R81.20 and imported config and the Cpsho_user was gone, and everything worked
On the other I deleted Cpsho_user, and everything worked
And on the 3rd I added the homedir: set user cpsho_user homedir /home/cpsho_user
why is Cpsho_user not created on a fresh installed R81.20?
/gsa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anyone else that hits this thread:
In our instance:
Message logs filled with:
kernel:clish[xxxxx]: segfault at 0 ip 00000000f5078a5f sp 00000000ffeeb3b0 error 4 in libcli_passwd.so
cpsho_user was missing both homedir & realname
Gaia administrator "cpsho_user" is added on Management Servers
https://support.checkpoint.com/results/sk/sk181305
"show configuration user" command fails with "Segmentation fault" on the Security Management Server
https://support.checkpoint.com/results/sk/sk181626
CCSME, CCTE, CCME, CCVS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@StackCap43382 wrote:Anyone else that hits this thread:
In our instance:
Message logs filled with:
kernel:clish[xxxxx]: segfault at 0 ip 00000000f5078a5f sp 00000000ffeeb3b0 error 4 in libcli_passwd.socpsho_user was missing both homedir & realname
Gaia administrator "cpsho_user" is added on Management Servers
https://support.checkpoint.com/results/sk/sk181305"show configuration user" command fails with "Segmentation fault" on the Security Management Server
https://support.checkpoint.com/results/sk/sk181626
Yes, we had the same issue exactly. It appeared on R81.10 after installing JHF130 over JHF95. Adding home directory helped.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Upgraded to R82 JHFA10.
HealthCheck Point (HCP) now send WARNING!
Test name Status Runtime (sec)
==========================================================================
Users in Gaia Database............................[WARNING] 0.00108
+------------------------------------------------------------------------------------------------------------------------------------+
| Results |
+====================================================================================================================================+
| Gaia OS/General/Users in Gaia Database |
+------------------------------------------------------------------------------------------------------------------------------------+
| Result: WARNING |
| |
| Description: This test checks if all users in the Gaia Database have the required settings (bindings) |
| |
| Summary:1 user is missing the required bindings: |
| User 'cpsho_user' is missing these required bindings: homedir |
| |
| Finding: |
| User 'cpsho_user' is missing these required bindings: homedir |
| |
| Finding: |
| Suggested steps in Gaia Clish for each user with missing bindings: |
| (1) Delete the problematic user: |
| delete user <Username> |
| (2) Save the changes in the Gaia Database: |
| save config |
| (3) Create the required user: |
| add user <Username> uid <UID> homedir <Path> |
| (4) Configure the new user: |
| set user <Username> <Parameters> |
| (5) Save the changes in the Gaia Database: |
| save config
We prefer it should not trigger security WARNING in included health check system to suggest to remove or recreate the user.
How should the homedir issue be fixed? Do I need to create it or will it be fixed in coming JHFA or in the HCP check?
/Johan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct homedir = add user cpsho_user uid 1000 homedir /home/cpsho_user
I would try this to see if the error is then gone.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, It look like you want to add cpsho_user homedir with normal clish configuration, that does not look correct for me since I do not have anything else in clish for the cpsho_user. Different compared to some other user earlier in this thread that look like they do have it in clish. I will add it directly in the db to update passwd file instead.
That look like this if anyone else want to do the same and also do not see the cpsho_user when running in clish show configuration
dbset passwd:cpsho_user:homedir /home/cpsho_user
dbset :save
/Johan
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 11 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter