- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: What happens to asynchronous fragments on a fi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
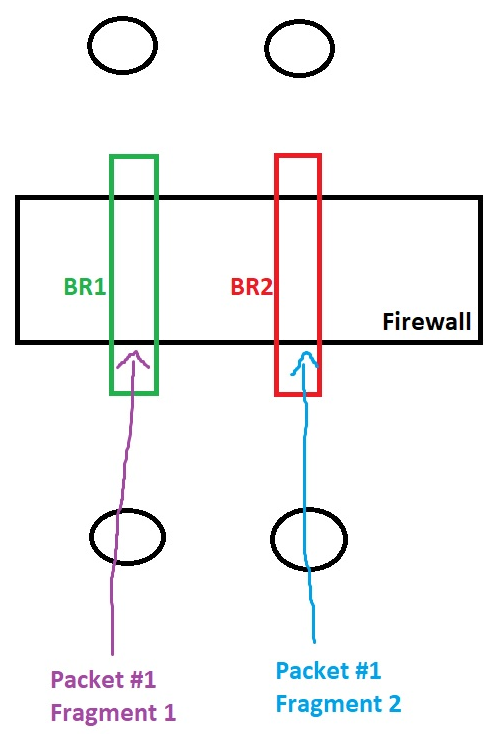
What happens to asynchronous fragments on a firewall in bridge mode?
I have a firewall that has two bridges, BR1 and BR2. These bridges handle traffic for two equal cost links. Packets can route asynchronously without issue all day long (with SXL disabled), but I'm curious about fragments. What happens when packet #1 is fragmented into 2 parts before it reaches the firewall where packet #1 frag #1 arrives at BR1 and packet #1 frag #2 arrives at BR2?
This works:
What happens here? Does the firewall reassemble them or discard them?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Message "fwchain_frag Reason: wait for more fragments" does not necessarily indicate any sort of a problem. By itself, a drop for this reason simply means the Security Gateway is handling a fragmented packet.
Whenever a fragment arrives to the Security Gateway, it buffers (holds) the packet in its memory. After the fragment has been held in memory, Security Gateway drops the fragment being processed by the kernel with reason: "fwchain_frag Reason: wait for more fragments".
It does this for each fragment until the last piece (fragment) of the packet is received.
Once Security Gateway has all fragments of the packet, it re-assembles the full packet, then sends it back through the kernel inspection engine as a whole, reassembled packet to be inspected, then routed, etc.
If, for some reason, all the fragments of the packet were not received in time (1 second by default @Timothy_Hall has already mentioned that.), then you will see another drop log: "held chain expired". At this point, the fragments that were previously held in memory are discarded.
If you do not ever see drops for "held chain expired", but only see "fwchain_frag Reason: wait for more fragments", then nothing is being dropped/blocked by the Security Gateway. It simply performs virtual fragmentation reassembly.
If you see "fwchain_frag Reason: wait for more fragments" followed by "held chain expired", then most likely, you are not receiving all the required fragments. This traffic is failing.
The Security Gateway is functioning as designed. "dropped by fwfrag_expires Reason: timeout has expired for fragment" is also an indicator that the timeout has expired and the fragmented packet has been dropped.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Doesn't matter which bridge group the packet traverses, it still has to go through the INSPECT driver either way. If the second part of a fragmented packet arrives first out of order, the firewall will hold it for up to 1000ms waiting for all other fragments to arrive (based on default Inspection Settings), virtually reassemble them for inspection, then forward the original frags assuming they pass inspection. So the asymmetry of firewall interfaces isn't really a problem here, but can run afoul of antispoofing enforcement.
Asymmetry becomes a problem when one of the two packet streams (forward or return) associated with a single connection is not traversing the firewall at all.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, Tim. That's what I'd assume to be the behavior, as well. However, when looking at fw ctl psatat, I see a large number of expired packets (over 50%):
Fragments:
65604306 fragments, 12766422 packets, 39920270 expired, 0 short,
When I capture packets on all 4 physical interfaces, I see the frags come in, but never leave. Frag #1 arrives at (subseconds) HH:MM:SS.624739 and frag #2 arrives at HH:MM:SS.624763, which seems within the firewall's hold time.
A debug shows:
fw ctl zdebug -m fw + drop
;[cpu_29];[fw4_4];fwfrag_expires: IP fragment expiration reached, freeing cookies;
;[cpu_29];[fw4_4];fw_log_drop_ex: Packet proto=-1 ?:0 -> ?:0 dropped by fwfrag_expires Reason: timeout has expired for fragment;
;[cpu_29];[fw4_4];fwfrag_expires: IP fragment expiration reached, freeing cookies;
;[cpu_29];[fw4_4];fw_log_drop_ex: Packet proto=-1 ?:0 -> ?:0 dropped by fwfrag_expires Reason: timeout has expired for fragment;
If frags #1 and #2 arrive on the same bridge, life is good and the frags leave the firewall. So it would seem to be that the frags MUST come in the same interface, but I'm looking for confirmation that this is the case. Thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Previously this sort of processing (fragmented packets) was done F2F, now (in R80.20+) it's done in the F2V path. Suspect this might be a bug and it's probably worth a TAC case if you haven't opened one up yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know for a fact it doesn't matter when the firewall is in routed mode, but in bridged mode perhaps packets from each bridge group are "stuck" to a different Firewall Worker core instance. All packets (and fragments) of a connection must be handled on the same worker core. Sounds like you already have SecureXL disabled, but that doesn't mean quite the same thing it did in R80.10 and earlier.
In your fw ctl zdebug output do you see different references for the worker instance number (fw4_X) for fragments of the same connection?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The _X value changes, but since this log doesn't show IPs, I'm not sure if it's for the same connection or not...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Message "fwchain_frag Reason: wait for more fragments" does not necessarily indicate any sort of a problem. By itself, a drop for this reason simply means the Security Gateway is handling a fragmented packet.
Whenever a fragment arrives to the Security Gateway, it buffers (holds) the packet in its memory. After the fragment has been held in memory, Security Gateway drops the fragment being processed by the kernel with reason: "fwchain_frag Reason: wait for more fragments".
It does this for each fragment until the last piece (fragment) of the packet is received.
Once Security Gateway has all fragments of the packet, it re-assembles the full packet, then sends it back through the kernel inspection engine as a whole, reassembled packet to be inspected, then routed, etc.
If, for some reason, all the fragments of the packet were not received in time (1 second by default @Timothy_Hall has already mentioned that.), then you will see another drop log: "held chain expired". At this point, the fragments that were previously held in memory are discarded.
If you do not ever see drops for "held chain expired", but only see "fwchain_frag Reason: wait for more fragments", then nothing is being dropped/blocked by the Security Gateway. It simply performs virtual fragmentation reassembly.
If you see "fwchain_frag Reason: wait for more fragments" followed by "held chain expired", then most likely, you are not receiving all the required fragments. This traffic is failing.
The Security Gateway is functioning as designed. "dropped by fwfrag_expires Reason: timeout has expired for fragment" is also an indicator that the timeout has expired and the fragmented packet has been dropped.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, Heiko. Based on what you shared, I'm thinking the gateway must not know how to assemble fragments arriving on different bridges, event if they are for the same connection, resulting in the "dropped by fwfrag_expires Reason: timeout has expired for fragment;" and "fwfrag_expires: IP fragment expiration reached, freeing cookies;" messages. Agreed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That’s how I interpret it anyway.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 10 | |
| 10 | |
| 10 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter