- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: The 'CheckPoint Services' updatable object inc...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
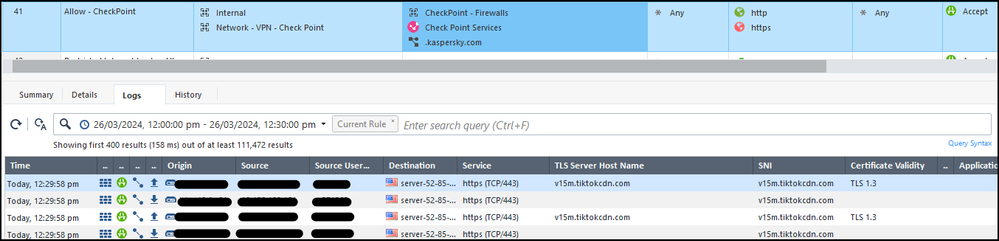
The 'CheckPoint Services' updatable object includes Tiktok?!
A client is attempting to restrict public internet access for critical systems and is in the process of whitelisting various services ahead of a drop rule.
It appears CheckPoint include a Cloud Front reverse proxy in the allowed list of sites, which subsequently allows traffic to a variety of destinations, which is quite simply unexpected.
Detail:
PS: Would be great if CheckPoint could also include the Kaspersky / Kasperski virus pattern update destinations in this object, as they currently require separate allowances to be made.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wait, what do you mean it includes tik tok?? Thats definitely not accurate...if you look at below link, thats what comes up when you edit update object in smart console
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
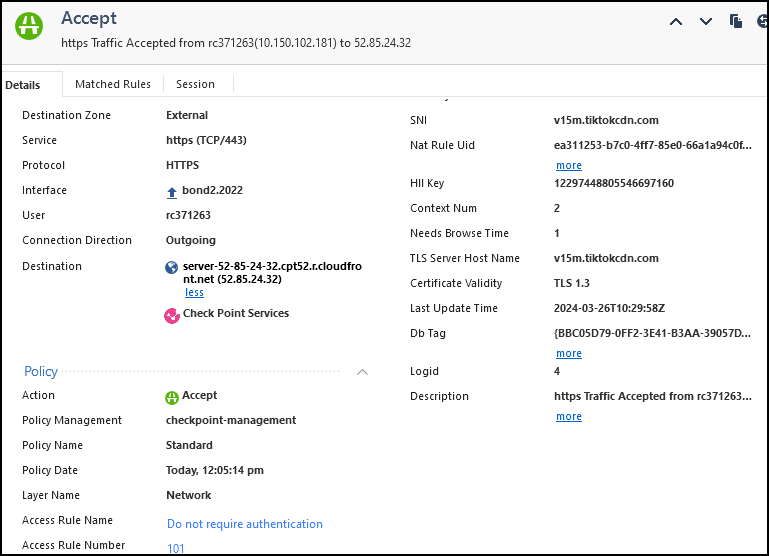
As per sk83520: See sk179105. These domains are part of the "Check Point Services" Updatable object.
v15m.tiktokcdn.com points at AWS's CloudFront, by the dynamic object resolving FQDNs it essentially then includes anything fronted by AWS.
[root@linux-test ~]# host v15m.tiktokcdn.com
v15m.tiktokcdn.com is an alias for d1urvv9m2chg9l.cloudfront.net.
d1urvv9m2chg9l.cloudfront.net has address 52.85.24.38
d1urvv9m2chg9l.cloudfront.net has address 52.85.24.105
d1urvv9m2chg9l.cloudfront.net has address 52.85.24.32
d1urvv9m2chg9l.cloudfront.net has address 52.85.24.45
If I iterate through the FQDNs in sk83520:
[root@linux-test ~]# for f in `cat links`; do echo -e "\n$f:"; host $f | grep -C 5 52.85.24; done
cws.checkpoint.com:
updates.checkpoint.com:
crl.godaddy.com:
crl.globalsign.com:
dl3.checkpoint.com:
usercenter.checkpoint.com:
usercenter.checkpoint.com is an alias for d2a5kmmlbqc9tw.cloudfront.net.
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.118
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.56
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.59
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.92
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:7600:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:6400:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:4a00:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:e000:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:b800:e:90fc:b100:93a1
usercenter.checkpoint.com:
usercenter.checkpoint.com is an alias for d2a5kmmlbqc9tw.cloudfront.net.
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.56
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.59
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.92
d2a5kmmlbqc9tw.cloudfront.net has address 52.85.24.118
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:6400:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:4a00:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:e000:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:b800:e:90fc:b100:93a1
d2a5kmmlbqc9tw.cloudfront.net has IPv6 address 2600:9000:20d9:8000:e:90fc:b100:93a1
resolver1.chkp.ctmail.com:
resolver2.chkp.ctmail.com:
resolver3.chkp.ctmail.com:
resolver4.chkp.ctmail.com:
resolver5.chkp.ctmail.com:
download.ctmail.com:
te.checkpoint.com:
teadv.checkpoint.com:
threat-emulation.checkpoint.com:
ptcs.checkpoint.com:
ptcd.checkpoint.com:
kav8.zonealarm.com:
kav8.checkpoint.com:
avupdates.checkpoint.com:
sigcheck.checkpoint.com:
smbmgmtservice.checkpoint.com:
zerotouch.checkpoint.com:
secureupdates.checkpoint.com:
productcoverage.checkpoint.com:
productcoverage.checkpoint.com is an alias for d3t9kb8u7d9ero.cloudfront.net.
d3t9kb8u7d9ero.cloudfront.net has address 52.85.24.73
d3t9kb8u7d9ero.cloudfront.net has address 52.85.24.118
d3t9kb8u7d9ero.cloudfront.net has address 52.85.24.13
d3t9kb8u7d9ero.cloudfront.net has address 52.85.24.38
d3t9kb8u7d9ero.cloudfront.net has IPv6 address 2600:9000:20d9:8e00:11:93cf:100:93a1
d3t9kb8u7d9ero.cloudfront.net has IPv6 address 2600:9000:20d9:4e00:11:93cf:100:93a1
d3t9kb8u7d9ero.cloudfront.net has IPv6 address 2600:9000:20d9:1600:11:93cf:100:93a1
d3t9kb8u7d9ero.cloudfront.net has IPv6 address 2600:9000:20d9:6400:11:93cf:100:93a1
d3t9kb8u7d9ero.cloudfront.net has IPv6 address 2600:9000:20d9:9000:11:93cf:100:93a1
sc1.checkpoint.com:
sc2.checkpoint.com:
sc3.checkpoint.com:
sc4.checkpoint.com:
sc5.checkpoint.com:
push.checkpoint.com:
downloads.checkpoint.com:
downloads.checkpoint.com is an alias for d236p925k8h5yp.cloudfront.net.
d236p925k8h5yp.cloudfront.net has address 52.85.24.18
d236p925k8h5yp.cloudfront.net has address 52.85.24.116
d236p925k8h5yp.cloudfront.net has address 52.85.24.92
d236p925k8h5yp.cloudfront.net has address 52.85.24.64
productservices.checkpoint.com:
productservices.checkpoint.com is an alias for dgwyyuqm5td5l.cloudfront.net.
dgwyyuqm5td5l.cloudfront.net has address 52.85.24.119
dgwyyuqm5td5l.cloudfront.net has address 52.85.24.79
dgwyyuqm5td5l.cloudfront.net has address 52.85.24.60
dgwyyuqm5td5l.cloudfront.net has address 52.85.24.22
dgwyyuqm5td5l.cloudfront.net has IPv6 address 2600:9000:20d9:5200:9:af11:3640:93a1
dgwyyuqm5td5l.cloudfront.net has IPv6 address 2600:9000:20d9:bc00:9:af11:3640:93a1
dgwyyuqm5td5l.cloudfront.net has IPv6 address 2600:9000:20d9:e200:9:af11:3640:93a1
dgwyyuqm5td5l.cloudfront.net has IPv6 address 2600:9000:20d9:e000:9:af11:3640:93a1
dgwyyuqm5td5l.cloudfront.net has IPv6 address 2600:9000:20d9:6400:9:af11:3640:93a1
diag-services.checkpoint.com:
rep.checkpoint.com:
api-cpx.dome9.com:
api-cpx.dome9.com is an alias for dxed5q2t5jfr3.cloudfront.net.
dxed5q2t5jfr3.cloudfront.net has address 52.85.24.115
dxed5q2t5jfr3.cloudfront.net has address 52.85.24.42
dxed5q2t5jfr3.cloudfront.net has address 52.85.24.96
dxed5q2t5jfr3.cloudfront.net has address 52.85.24.66
api.dome9.com:
api-cpx.eu1.dome9.com:
api-cpx.eu1.dome9.com is an alias for d15w44dkxlq92m.cloudfront.net.
d15w44dkxlq92m.cloudfront.net has address 52.85.24.106
d15w44dkxlq92m.cloudfront.net has address 52.85.24.32
d15w44dkxlq92m.cloudfront.net has address 52.85.24.98
d15w44dkxlq92m.cloudfront.net has address 52.85.24.50
api.eu1.dome9.com:
api-cpx.ap2.dome9.com:
api-cpx.ap2.dome9.com is an alias for d35w8g8v0r08yu.cloudfront.net.
d35w8g8v0r08yu.cloudfront.net has address 52.85.24.52
d35w8g8v0r08yu.cloudfront.net has address 52.85.24.107
d35w8g8v0r08yu.cloudfront.net has address 52.85.24.110
d35w8g8v0r08yu.cloudfront.net has address 52.85.24.18
api.ap2.dome9.com:
api-cpx.cace1.dome9.com:
api-cpx.cace1.dome9.com is an alias for d15lm3hlanr25t.cloudfront.net.
d15lm3hlanr25t.cloudfront.net has address 52.85.24.17
d15lm3hlanr25t.cloudfront.net has address 52.85.24.106
d15lm3hlanr25t.cloudfront.net has address 52.85.24.117
d15lm3hlanr25t.cloudfront.net has address 52.85.24.28
api.cace1.dome9.com:
api-cpx.ap3.dome9.com:
api-cpx.ap3.dome9.com is an alias for ddn8wnsxko53c.cloudfront.net.
ddn8wnsxko53c.cloudfront.net has address 52.85.24.30
ddn8wnsxko53c.cloudfront.net has address 52.85.24.13
ddn8wnsxko53c.cloudfront.net has address 52.85.24.78
ddn8wnsxko53c.cloudfront.net has address 52.85.24.87
api.ap3.dome9.com:
api-cpx.ap1.dome9.com:
api-cpx.ap1.dome9.com is an alias for dm99h5bbwe39n.cloudfront.net.
dm99h5bbwe39n.cloudfront.net has address 52.85.24.90
dm99h5bbwe39n.cloudfront.net has address 52.85.24.125
dm99h5bbwe39n.cloudfront.net has address 52.85.24.129
dm99h5bbwe39n.cloudfront.net has address 52.85.24.66
api.ap1.dome9.com:
shiftleft.portal.checkpoint.com:
shiftleft-prod-bucket.sg.iaas.checkpoint.com:
shiftleft-prod-bucket.sg.iaas.checkpoint.com is an alias for d2kkj1tidestha.cloudfront.net.
d2kkj1tidestha.cloudfront.net has address 52.85.24.104
d2kkj1tidestha.cloudfront.net has address 52.85.24.90
d2kkj1tidestha.cloudfront.net has address 52.85.24.70
d2kkj1tidestha.cloudfront.net has address 52.85.24.20
d2kkj1tidestha.cloudfront.net has IPv6 address 2600:9000:20d9:8000:7:7c1:8f80:93a1
d2kkj1tidestha.cloudfront.net has IPv6 address 2600:9000:20d9:1a00:7:7c1:8f80:93a1
d2kkj1tidestha.cloudfront.net has IPv6 address 2600:9000:20d9:9e00:7:7c1:8f80:93a1
d2kkj1tidestha.cloudfront.net has IPv6 address 2600:9000:20d9:8800:7:7c1:8f80:93a1
d2kkj1tidestha.cloudfront.net has IPv6 address 2600:9000:20d9:c000:7:7c1:8f80:93a1
us-gw.sg.iaas.checkpoint.com:
eu-gw.sg.iaas.checkpoint.com:
au-gw.sg.iaas.checkpoint.com:
ca-gw.sg.iaas.checkpoint.com:
in-gw.sg.iaas.checkpoint.com:
sg-gw.sg.iaas.checkpoint.com:
Edit: I understand that the destinations are allowed, due to the updateable object resolving things as destination IPs whereby then allowing http/https would allow access to virtually any service fronted by AWS. Perhaps some attention could be put in to creating a managed Services and Application object, to provide a pre-canned secure way in which admins can poke holes in restrictive policies?
We see the above regularly, when clients self administer restrictions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did see that sk, but I dont see mention of tiktok anywhere. Maybe TAC can confirm for sure, but to me logically, it would not sound right that would be the case.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's an issue of how Updatable Objects intersect with CDNs. The updatable object says Check Point services are behind these 300 IP addresses, so traffic is allowed to them. If some other client of the CDN (TikTok) happens to hand out domain names which the CDN resolves to the same IPs, that traffic would be allowed too.
To fully prevent this, you need to use URL Filtering with HTTPS Inspection as well as simple firewall rules.
This kind of nonsense is why I can't stand "cloud" hosting. It lets any rando with a stolen credit card number run arbitrary code on the same hosts running your VMs, or distribute malware from the same hosts distributing your vendors' critical patches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see the point you are making.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you do 'light https inspection' so only iit checks the SNI. (The rest is encrypted)
Maybe then a drop rule would help and create it above this allow rule. To block specifically TikTok.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd rather CheckPoint avoid potentially insure rules in the first place, by removing the 'CheckPoint updates' dynamic object and replacing it with a 'CheckPoint Services' application awareness object. This object could then be maintained by them to include the necessary TLS SNIs as necessary.
We unfortunately often see reverse proxy services being included as allowed destinations which weakens the security posture of the organisation; the current design/structure IMHO leads to a false sense of security in essentially allowing anything HTTP/HTTPS connection to AWS's CloudFront, which may inadvertently then whitelist anything behind that proxy service.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter