- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Same interface for inbound and outbound internal t...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same interface for inbound and outbound internal traffic
Hello,
I want to perform Access Control and Threat Prevention between the local networks.
Description:
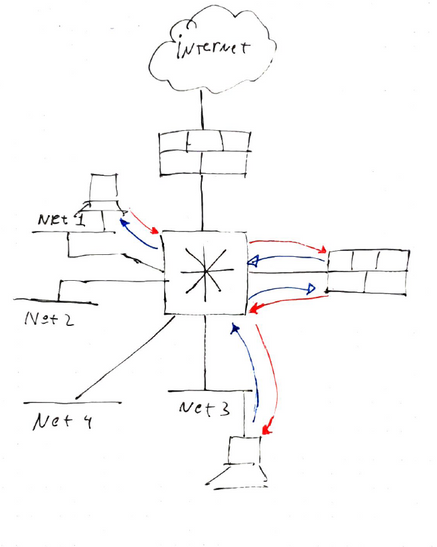
All networks are connected to a Router, which will detour all traffic to the Security Gateway, even when the destination is direct attached. For the Security Gateway, the inbound and outbound interface is the same in all packets but there is no assymetrical routing.
Questions:
Will the Threat Prevention and Firewall Blades work without issues on this scenario/layout?
Will the SG send to the router a ICMP Redirect Message?
Thanks
Lanello
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not a good idea. Use Bridge mode instead or IP forwarding in a normal mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
For the Bridge Mode can get a little bit complicated.
The Checkpoint would be at a side instead Man-In-The-Middle (Check the drawing).
It is a ClusterXL with 6 VSX. Two of them are Perimeter Firewalls, but I want to perform IPS between the local networks.
I know I can connect the networks direct to the Checkpoint and get rid of the router, but I still want to have it arround.
Thanks for your help.
Lanello
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, as stated before.. not a good idea. 🙂
Its like a firewall-on-a-stick setup, and I would guess that you will need to spend some time to get the routing set up and working. But yeah - sure I can't see that it wont work.
I have had setups where you had a main vrf with several 'child' vrf's, connecting the firewall to the main vrf and providing access between the 'childs' on the SG. This can be comapred to what you are asking.
Regaring the question on 'icmp redirects' vs. 'all networks connected to a router' gives me a confused picture on how you are planning to actually set this up.. is there to be several networks/subnets ? If you have ex. 2 client subnets and a subnet where the SG is to be placed, the packet flow will be pretty regular, just entering and leaving on same.
But all in all. not a good idea.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your example with the VRF is exaclty the same I want to do.
The routing part is already solved with a forced unconditional next-hop leading the packets to the firewall and the default route for the SG is the Core Router again (that's the plan).
Yes, there is a separated subnet for the comm between the SG and the Router.
If the VRF scenario is working for you, I can see the light at the end of the tunnel.
But you still say it is not a good idea...
Have you inter-VRF traffic that pass through the SG?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, ok - well. It depends on your design. For me the main thing was to have seperation between the vrf's, but do to 'stuff' I had to allow some traffic to pass between them, and thus getting the setup I was refering to. Worked fine..
It pretty much comes down to the network design. For me it added a bit of extra management, just to get people to understand the design. And troubleshooting got a bit more tedious.. NAT would probably be a bit 'interesting'.. Voice, qos, as an example, I have no idea. You have to take into consideration how you build policy set..working with zones etc..
But in general, "basic firewall functionality was fine.
It pretty much comes down to the network design. For me it added a bit of extra management, just to get people to understand the design. And troubleshooting got a bit more tedious.. NAT would probably be a bit 'interesting'.. Voice, qos, as an example, I have no idea. You have to take into consideration how you build policy set..working with zones etc..
But in general, "basic firewall functionality was fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In your configuration all traffic between VLANs can be easily routed trhough the FW's when you use the FWs as their default gateways.
Traffic between device in the same LAN will never work as both devices will always directly address the other device in the same LAN. Redirecting this to the FW is not only a bad idea but also very hard to do.
Traffic between device in the same LAN will never work as both devices will always directly address the other device in the same LAN. Redirecting this to the FW is not only a bad idea but also very hard to do.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for you comment @Maarten_Sjouw !
I will desist. The common sentence in teh comments of all of you is "This is a bad idead".
Anyways I will test the scenario in a lab and let you know.
Thanks guys!
PS:
Redirecting the traffic is very easy.
A Policy based route overrides the general routing table, setting the "default-nexthop" the firewall.
I have tested this step already without issues.
Lanello
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry for that typo..
Are all systems in that VLAn capable of setting that policy route?
Only other method I can think of is by setting the IP to a /32 and set the default gateway, but normally those types of config are not accepted by most OS's.
Are all systems in that VLAn capable of setting that policy route?
Only other method I can think of is by setting the IP to a /32 and set the default gateway, but normally those types of config are not accepted by most OS's.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't need to inspect traffic between the hosts on the same network.
Only the inter-subnet traffic.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 11 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter