- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.40 Early Availability Program @ Check Poin...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.40 Early Availability Program @ Check Point Update
|
R80.40 EA ProgramR80.40 features centralized management control across all networks, on premise or in the cloud, lowering the complexity of managing your security and increasing operational efficiency. As part of the Check Point Infinity architecture, R80.40 provides customers with the best security management, utilizing the Industry’s largest integration of technologies from more than 160 technology partners. With Check Point R80.40 Cyber Security for Gateways and Management, businesses everywhere can easily step up to Gen V. |
|
|
|
|
• We are looking for R80.X / R77.X Production environment to evaluate the new version. • Start date: Started
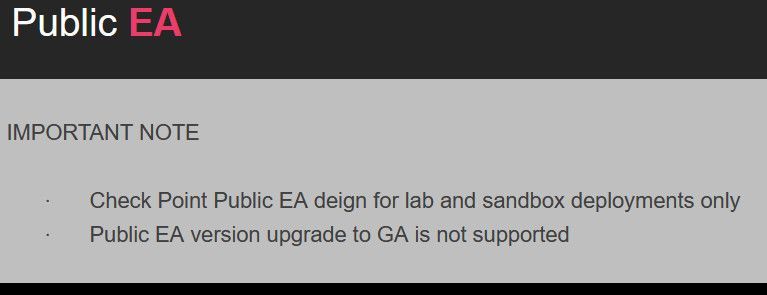
Public EA (for Lab/Sandbox use) is now also available!
|
|
|
Additional questions? contact us@ EA_SUPPORT@checkpoint.com |
|
What's New |
|
IoT SecurityA new IoT security controller to:
TLS InspectionHTTP/2
TLS Inspection Layer This was formerly called HTTPS Inspection. Provides these new capabilities:
Threat Prevention
Access ControlIdentity Awareness
IPsec VPN
URL Filtering
|
83 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a customer using MEP to provide load-sharing and resilience across two physical Internet links in two geographically separate data centres for end users (i.e not site-to-site). It works really well, and you can clearly see the load balanced almost equally (within single-digits) with 2,000 users per site/cluster. When one site fails (or is taken down for maintenance) all users just connect seamlessly to the remaining site with MEP. This has been working for years on R77 and now R80.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPsec VPN
- Configure different VPN encryption domains on a Security Gateway that is a member of multiple VPN communities. This Option was much needed, looking forward to it. Thanks for including this change in R80.40. Alos, just wanted to confirm if SHA-512 is added for Hashing method inside S2S VPN configuration or not. Nowadays many of the Clients asking to use the SHA-512 for Integrity but its not available with Checkpoint yet (Till R80.30).
Thanks,
CSR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since yesterday it is public EA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the R80.40 release notes:
Application Control
- Improved performance, diagnostics and monitoring tools.
- Enchantment to Server Name Indicators (SNI) classifications.
Always thought SNI seemed like magic and finally we have confirmation!
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization
Check Point Firewall Performance Optimization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hoho @Timothy_Hall . you a funny man!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
In order to release R80.40 we are looking for production sites that are willing to install this week!
we have release candidate and we are on the verge of final version.
Contact us directly at: EA_SUPPORT@checkpoint.com
or enroll: https://www.surveymonkey.com/r/cp-ea-r8040-enrollment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone tested the backup and restore of an individual CMA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Can a R80.30 or R80.20 manager manage an 80.40 EA gateway? I'd like to bring up a production 5800 appliance but keep my main manager on a GA version. I'm guessing the R80.40 manager will be under GA sooner than the gateway, but it seems like R80.40 EA, includes manager and gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello -- what you describe (production devices) is necessarily the private EA accessed via your local CP field engineers and onsite TLC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
future planning question. RE: gateway Should R80.40 be stable with ext3 or is xfs required/strongly recommended?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Stability should be about the same. Considering how little the gateway normally hits its hard drive, I doubt it will make much of a performance difference. XFS might be able to recover itself slightly better in the event of a power loss or crash, but that is about it.
A SMS/MDS on the other hand is a completely different story, and you most definitely want XFS due to heavy hard drive utilization.
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization
Check Point Firewall Performance Optimization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
Currently only R80.40 Management server can manage R80.40 GW.
Once R80.40 is GA it will be supported by next JHF for R80.20 & R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, once the jumbo support is added to R80.30 management, would an R80.30 manager be able to manage a new pair of R80.40 gateways deployed in Active-Active cluster mode (eg. L3 clustering)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Unfortunately Active-Active cluster requires R80.40 management server, so at this stage you will not be able to use it unless upgrading the management server to R80.40.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
RE: upgrade from R80.30 2.6.18 kernel to R80.40 3.10 kernel question for future planning
If you have a 5800 appliance (gateway only) that was recently formatted with ext3 (R80.30 running 2.6.18), and you plan to upgrade to R80.40 GA (once its out in March/April?) will you need to plan to re-format or can you simply count on a normal CPUSE upgrade the gateway to R80.40 GA? And the kernel should change to 3.10 correct, no re-format necessary y/n?
From what I can tell an upgrade will get me to R80.40 and 3.10, but if I want xfs, I'd need to re-format.
[Expert@fwl-box-03:0]# cat /etc/fstab
/dev/mapper/vg_splat-lv_current / ext3 defaults 1 1
LABEL=/boot /boot ext3 defaults 1 2
devpts /dev/pts devpts gid=5,mode=620 0 0
tmpfs /dev/shm tmpfs defaults 0 0
proc /proc proc defaults 0 0
sysfs /sys sysfs defaults 0 0
/dev/mapper/vg_splat-lv_log /var/log ext3 defaults 1 2
LABEL=SWAP-sda2 swap swap defaults 0 0
[Expert@fwl-box-04:0]# cat /etc/fstab
/dev/mapper/vg_splat-lv_current / ext3 defaults 1 1
LABEL=/boot /boot ext3 defaults 1 2
devpts /dev/pts devpts gid=5,mode=620 0 0
tmpfs /dev/shm tmpfs defaults 0 0
proc /proc proc defaults 0 0
sysfs /sys sysfs defaults 0 0
/dev/mapper/vg_splat-lv_log /var/log ext3 defaults 1 2
LABEL=SWAP-sda2 swap swap defaults 0 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
will be possibile moves from a SMS 80.20 an let become it ad Domanin Management Server (CMA) in 80.40?
Regards
Mattia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Mattia_Varone generally speaking, yes, you can migrate SMS to MDSM as a security domain server. Mind R80.40 public EA is for lab purposes though. If you want to move your production environment, you will have to wait till the release is out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val,
thanks for your reply. So the issue described in the sk122700, will be solved in 80.40?
Thanks
Mattia
thanks for your reply. So the issue described in the sk122700, will be solved in 80.40?
Thanks
Mattia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh, I see... let me check with R&D, it might be my answer was not correct, as it is not applicable to R80.30 and below, apparently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I'm waiting your update.
I hope will be possible move from a Security Management Server 80.40 to become a Domain Management Server on a Multi-Domain Server 80.40
Regards
Mattia Varone
I hope will be possible move from a Security Management Server 80.40 to become a Domain Management Server on a Multi-Domain Server 80.40
Regards
Mattia Varone
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Mattia_Varone, my name is Eran and I'm the R&D manager in Check Point responsible for the core of the Management server. In R80.40 we implemented the ability to do the following:
- Backup and restore an individual Domain.
- Migrate Domain to another Multi Domain Server.
- Migrate a SmartCenter machine to a Domain on a Multi Domain Server (and vice versa).
All those abilities are included and available as part of the public EA of R80.40, more info could be found on the EA version of the Management API reference for R80.40, but note some of the SKs which appear as reference are still internal and will be released once R80.40 is out.
We plan to make those abilities available as part of the JHF of R80.20 and R80.30 soon and we're actually looking for customers who would like to take part in testing the Domain migration feature as part of JHF. Please contact me directly if it's relevant for you - would be great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Eran_Habad thanks for your answer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Eran for your answer
- « Previous
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 11 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter