- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R77.30 Take 286: New Jumbo Hotfix GA Release
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R77.30 Take 286: New Jumbo Hotfix GA Release
A new General Availability Jumbo Hotfix Accumulator take for R77.30 (take_286) is available.
It includes important stability and Security software updates:
- Support for TLS 1.2 - sk107166.
- support for Smart-1 405 and 410 appliances - sk117578.
- Support for Online Certificate Status Protocol (OCSP).
- Improved MTA.
- Support for Capsule Workspace App Wrapping - sk111558.
- Support for Mobile Access Reverse Proxy -sk110348.
Take_286 is the latest General Availability release that can be directly downloaded from Check Point Cloud using CPUSE and from sk106162
Take | Date | CPUSE Identifier | CPUSE offline package |
Take_286 | 13 Sep 2017 | Check_Point_R77_30_JUMBO_HF_1_Bundle_T286_FULL.tgz | (TGZ) |
Note: Effective Sep 25th 2017, the General Availability Take_286 is available for CPUSE online installation in Gaia Portal and Gaia Clish (it replaces Take_216).
Notes:
- For Threat Emulation customers that do not allow automatic updates from the cloud, and following the integration of TLS1.2 support,
it is important to update the Threat Emulation Engine according to the next SK: sk92509 - Offline updates for Threat Emulation images and engine.
28 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I installed this Take_286 last Thursday, my SmartCenter CA broke. Neither sk33224 nor sk101833 solved the issue. So I reverted back to the previous Take_226 which solved it but broke my Gaia WebUI that worked previously.
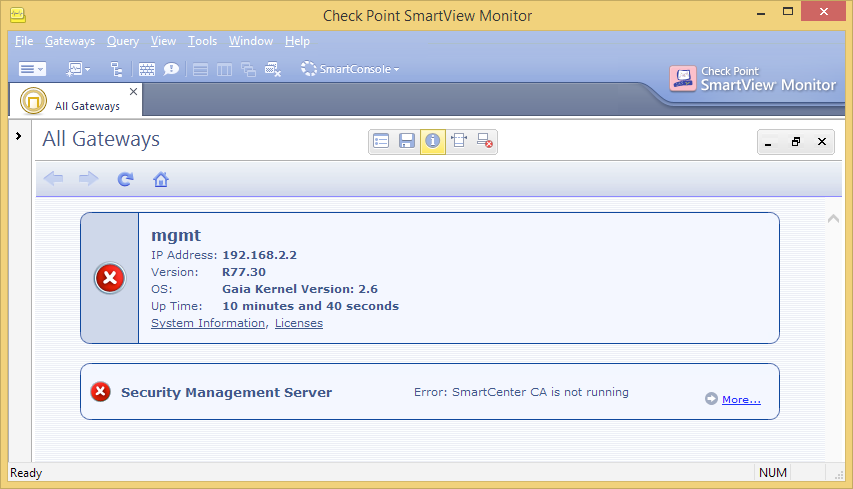
I opened a Service Request last Friday and I'm still waiting for a Remote Session. Support wanted cpinfo -z -o cpinfo.gz, cpinfo -y all, migrate export and screen shot of the issue that I had already attached and then delayed this ever since. Hopefully they'll do a remote session tomorrow to look into it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We have applied Take_282 to one of our customer, based on inputs from TAC last week. It seems to be very stable.
No issue till now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Danny,
I had the same problem installing the first take with TLS 1.2 Support (HFA 266).
After a rollback to my original HFA 225, and verify the symptoms of sk115732 and sk91380, none of them applied for me.
I did some research and to solve first I had to verify the parameter name was SSLMutex on file "/web/templates/httpd-ssl.conf.templ", this because on the new HFA the instruction SSLMutex is replaced by Mutex (this because of apache update):
[Expert@hostname:0]# cat /web/templates/httpd-ssl.conf.templ | grep SSLMutex
SSLMutex file:/usr/local/apache2/logs/ssl_mutex
Then, I tried to start manually the httpd2 process:
[Expert@hostname:0]# /opt/CPshrd-R77/web/Apache/2.2.0/bin/httpd2 -k start -f /web/conf/httpd2.conf -D FOREGROUND
After executing this I got an error of corrupted library (and the path). I replace the library from another gateway with same version and HFA as original (R77.30 HFA 225) and after this the Gaia WebUI was accesible again.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your response. The Gaia WebUI issue was fixed in JHF Take 286 (see Release Notes). My issue is that it introduced another issue with the SmartCenter CA. I'm still waiting for Check Point R&D to provide a Remote Session in order to fix it.
I also upgraded another Customer to JHF Take 286 today without any issues. Fingers crossed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great to hear that! Please let us know the news about your CA issues. Also had customers with old GA HFA because of this.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I missed the OCSP part in the updated SK.
Good to hear it is now part of the mainstream JHF.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Dameon Welch Abernathy's post also missing for all ThreatEmulation E-Mail users is the following addition to his Notes:
Check your custom postfix modifications after the upgrade.
This JHF GA also includes a known issue with emulation of links in email - sk118280:
It is therefore important to disable “Emulation of links in email” until the TE engine 6.9 (currently EA) is deployed when installing this JHF GA build:
1.vi $FWDIR/conf/mail_security_config
2.add “te_mta_emulate_links_inside_emails=0” under "[mta]" section
3.Save and install policy
4. When TE engine 6.9 is deployed revert the above setting, Save and install policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for including that important detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I learned it the hard way today. Had to have the virtual.db recreated and everything.
Btw, I like Badges ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You deserve one ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw this issue on the MTA of one of my customers and as written in the SK there is also a fix available!
So why not head for the custom fix? Why disable emulation of links-inside-mails instead?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because adding one line to $FWDIR/conf/mail_security_config is so much quicker to solve the issue when the customer is already suffering instead of contacting Check Point Support to wait for getting a custom built and JHF specific Hotfix for this issue that needs to be requested of each single JHF take and customer environment again. Also you have no dependencies regarding custom Hotfixes installed on top of a JHF takes and therefore much more control about what is actually configured and running on your highly critical firewall system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so I think your solution is a workaround for customers, who don't want to install the hotfix or have to wait for it to be ported for their environment.
Another workaround would be to disable ".com" extension for profile of MTA to be emulated (That's what we did in this case).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, i have the same issue.
the threat emulation policy was completely wiped clean, and had to recreate everything.
After creation mails got blocked when passing through threat emulation and MTA.
when an emulation error occurred, valid mails got blocked !
I can concur that "te_mta_emulate_links_inside_emails=0" helped me to disable the option "links inside mails".
Because the option can't be modified from the point where it used to be -> in the TE policy.
Also, smartlog stopped logging after the upgrade and i had to reboot or even do a sic reset for some gateways...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Danny - Has your management CA issue been resolved?
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not yet. Check Point Support couldn't troubleshoot it on the production system so they are now trying to recreate the issue in their lab which can take a while. I'm currently providing more and more backup / debug files.
Also we encountered a new issue with R77.30 JHF (Take 286) today. If you are using the Giraffe_V2 GA Hotfix for Identity Awareness Agents (pdpd daemon issue), you can't upgrade to Take 286 yet as Giraffe_V2 wasn't integrated into it and can't be installed on top of it and Giraffe_V3 is not available yet nor has an ETA. Only other option is to go straight to R80.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you working with TAC on the incompatibility with the Identity Collector hotfix?
For those wondering what we're talking about: Identity Collector - Technical Overview
In general, it's always a good idea to engage with the TAC in a situation where you are using hotfixes that conflict with the current Jumbo Hotfix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Danny,
we have just released giraffe_v3 which is compatible with JHF 286.
Thanks,
Royi.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please provide a link to this.. I have a customer intent on using identity collector for cisco ISE; my recommendations have been that one cannot update to T286 because it's unsupported (according to the documentation):
Release notes:
TAGS ARE REQUIRED --> Check Point Software Technologies: Download Center
"This Hotfix is validated only for R77.30 with Jumbo Hotfix Take 95. If you want to change this environment, you must first consult with your Check Point partner or vendor. This release is built for the specific environment. Upgrades or other changes can overwrite Hotfix functionality and environment customizations."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I received a copy of Giraffe_V3 from opening a ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we installed JBHF286 to 3 clusters 2 gateways and 3 management appliances about a week ago, so far no issues to report.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you seen any improvements with HTTPS inspection post JBHF286?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Installed JHF 286 a couple of weeks ago. We had to uninstall Hotfix_sk111292_FULL. After that, we cannot manage 1100 appliances any more. Ticket still open with no progress the last days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding my SmartCenter CA issue, TAC/RnD couldn't recreate the issue in its lab and finally advised to do a fresh install of the entire SmartCenter server. This solved the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Conflicts with SK109713 vSEC central license patches, this is not documented in the release notes.
If you are using vSEC central licenses for AWS/Azure and have the SK109713 patch installed, this patch cannot be installed. If you attempt to install T286 first.. then install the vSEC patch, it will still conflict.
I am yet to find a solution to this.
//
A fix conflict was detected during pre-install validation.
To prevent system instability, installation will not continue.
Please contact Check Point support with the following information:
HF 'Check R77_30_JUMBO_HF
Conflicts with hotfix VSEC_CENTRAL_LIC_001 - details:
01966961
Checking for conflicts between new file: /var/log/tmp/bundle_tmpdir_CheckPoint#CPUpdates#All#6.0#4#0#BUNDLE_R77_30_JUMBO_HF#286_CBmzEy/fw1/crs.xml
And existing inventory log: /opt/CPsuite-R77/conf/crs.xml
A fix conflict was detected during pre-install validation.
To prevent system instability, installation will not continue.
Please contact Check Point support with the following information:
HF 'Check R77_30_JUMBO_HF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I have found a workaround for this just FYI
First install the Take 286 Jumbo HFA.
Then install the Management Add-On T204.
Then Install the VSEC license patch.
This succeeds.
Iain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have some trouble upon installing hot fix take 286. i cannot access my web gui upon installation. How i can resolved this problem? My previous hot fix before i installed is take 216. How i can revert this using CLI. Thank you.
Please see below screenshot for cpinfo.
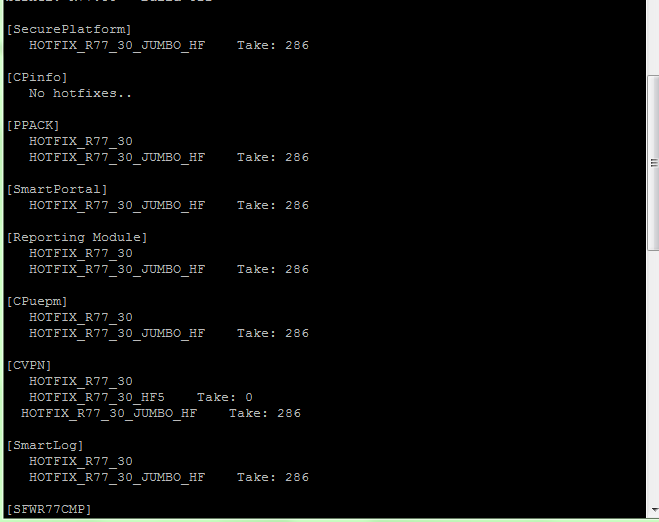
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To uninstall a package from the CLI:
- List the names and the sequence numbers of the installed packages: type
installer uninstalland press the TAB key. - Uninstall a package:
installer uninstall {<num> | <package>} [not-interactive]You can run the command with either the sequence number or the name of the package, and either in interactive (default) or non-interactive mode.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 12 | |
| 10 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 |
Upcoming Events
Tue 07 Oct 2025 @ 10:00 AM (CEST)
Cloud Architect Series: AI-Powered API Security with CloudGuard WAFThu 09 Oct 2025 @ 10:00 AM (CEST)
CheckMates Live BeLux: Discover How to Stop Data Leaks in GenAI Tools: Live Demo You Can’t Miss!Thu 09 Oct 2025 @ 10:00 AM (CEST)
CheckMates Live BeLux: Discover How to Stop Data Leaks in GenAI Tools: Live Demo You Can’t Miss!Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


