- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: One way traffic is dropping in Site to Site VP...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
One way traffic is dropping in Site to Site VPN with DAIP gateway
I have configured site to site VPN between Checkpoint(R81.20 JHF T41) and Strongswan in Ubuntu(DAIP gateway).
Assume Host-A is behind Checkpoint and Host-B is behind Strongswan in Ubuntu.
One way traffic is dropping in Site to Site VPN with DAIP gateway
I have configured site to site VPN between Checkpoint(R81.20 JHF T41) and Strongswan in Ubuntu(DAIP gateway).
Assume Host-A is behind Checkpoint and Host-B is behind Strongswan in Ubuntu.
VPN tunnel is up and traffic initiated from Host-B to Host-A is working, But traffic initiated from Host-A to Host-B is not working.
Smartlog shows traffic is accepted and encrypted in community, But when checked on zdebug it is getting dropped with below error.
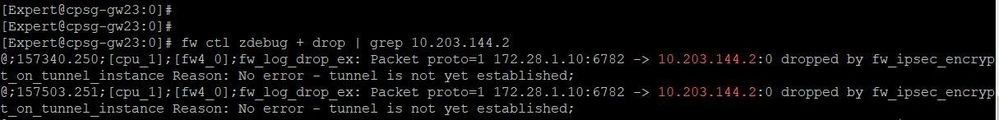
zdebug when pinging from Host-A to Host-B:
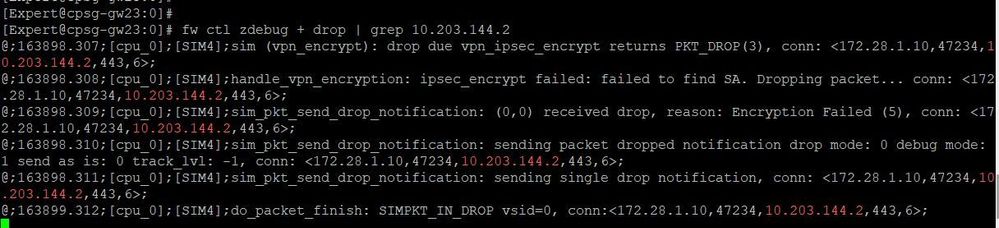
zdebug when initiating telnet from Host-A to Host-B on port 443:
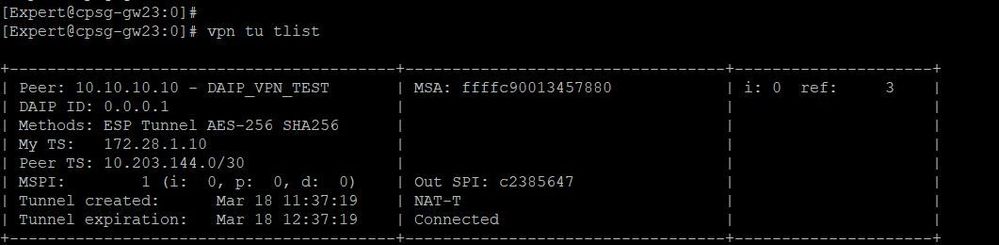
CP VPN status:
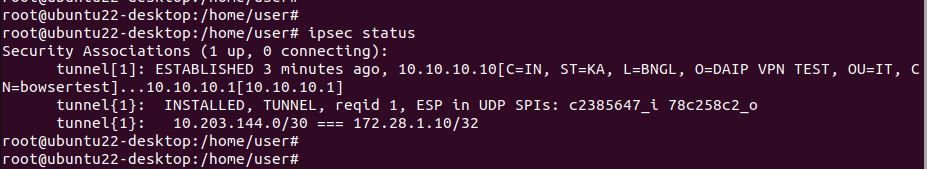
Strongswan VPN status:
My understating as per the logs, Checkpoint instead of sending traffic on existing tunnel, It is trying to create new tunnel for the encryption domain and failing in process as the peer is dynamic in interoperable object.
Please help me to fix this issue.
regards,
PK
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi.. The issue is resolved. Sharing my findings and fix, thought it might help community members.
In my configuration, local encryption domain is 172.28.1.10/32(Specific vpn domain for the community) and remote encryption domain is 10.203.144.0/30.
As my local encryption domain is single host, I created a group and added Host Object 172.28.1.10/32, and called the group on specific vpn domain for the community
As per vpn debug, when host behind the checkpoint initiates traffic it is not considering the Host Object used on specific vpn domain on the community, Instead checkpoint is considering Network Object(which the IP 172.28.1.10 belongs) from the default vpn domain, and trying to negotiate new phase-2(local 172.28.1.0/24 in my case and remote 10.203.144.0/30). As the peer end phase-2 configured with only /32, the new phase-2 negotiation is failing. Due to this traffic initiated from host behind checkpoint is not working.
Assuming checkpoint doesn't consider host object on encryption domain, I created Network Object 172.28.1.10/32 and replaced it with host object on the group. Post that issue resolved.
regards,
PK
3 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would contact CP TAC to get this resolved asap!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
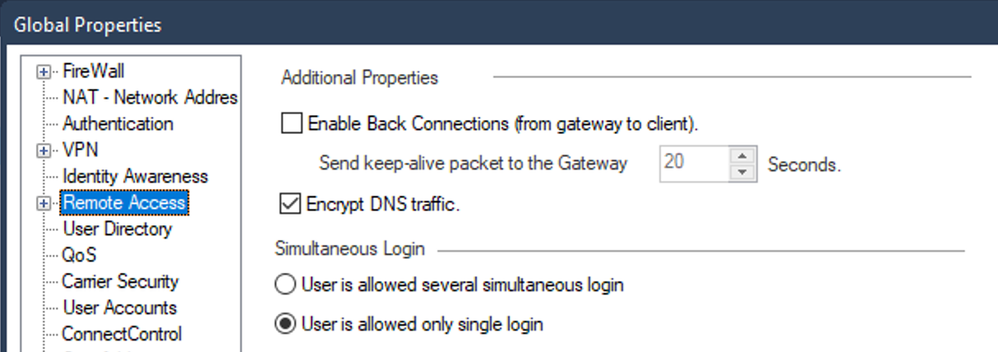
StrongSWAN is treated as a Remote Access Client, to the best of my knowledge.
Which means: make sure this is enabled:
Otherwise, I suggest a TAC case: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi.. The issue is resolved. Sharing my findings and fix, thought it might help community members.
In my configuration, local encryption domain is 172.28.1.10/32(Specific vpn domain for the community) and remote encryption domain is 10.203.144.0/30.
As my local encryption domain is single host, I created a group and added Host Object 172.28.1.10/32, and called the group on specific vpn domain for the community
As per vpn debug, when host behind the checkpoint initiates traffic it is not considering the Host Object used on specific vpn domain on the community, Instead checkpoint is considering Network Object(which the IP 172.28.1.10 belongs) from the default vpn domain, and trying to negotiate new phase-2(local 172.28.1.0/24 in my case and remote 10.203.144.0/30). As the peer end phase-2 configured with only /32, the new phase-2 negotiation is failing. Due to this traffic initiated from host behind checkpoint is not working.
Assuming checkpoint doesn't consider host object on encryption domain, I created Network Object 172.28.1.10/32 and replaced it with host object on the group. Post that issue resolved.
regards,
PK
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 10 | |
| 10 | |
| 10 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter