- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Inbound HTTPS Inspection - Importing Certifica...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Inbound HTTPS Inspection - Importing Certificate
Hello Experts.
I am trying to perform inbound HTTPS inspection; I do not have any private key password assigned to the certificate (wildcard certificate). While trying to import the internal server certificate for the inbound rules, I cannot import the certificate without providing the password.
Is there a way to skip/bypass the private key password section? It shows an error when I try to skip the password section.
*Note: When I provide the export password of the certificate in the private key password section, it accepts and imports the certificate.
Thanks in advance!!
Regards,
Digo.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Digo11 ,
Not sure if you were kidding when you asked for "a way to skip/bypass the private key " 🙂.
From CKP HTTPS Inspection documentation, we have the below paragraph explaining what is need:
| When a client from outside the organization initiates an HTTPS connection to an internal server, the Security Gateway intercepts the traffic. The Security Gateway inspects the inbound traffic and creates a new HTTPS connection from the gateway to the internal server. To allow HTTPS Inspection, the Security Gateway must use the original server certificate and private key. The Security Gateway uses this certificate and the private key for SSL connections to the internal servers. |
Inbound HTTPS ConnectionsInbound connections are HTTPS connections that arrive from an external client and connect to a server in the DMZ or the internal network. Inbound connection flow
|
Now on your problem, you can't, because when we do INBOUND HTTP Inspection , meaning we decrypt traffic that comes from outside to our DMZ servers, the CKP HAS TO Present itself as the "original server", therefore, in order to do that, the server SSL certificate and the private key, needs to be installed to he can substitute itself into the communication.
As example:
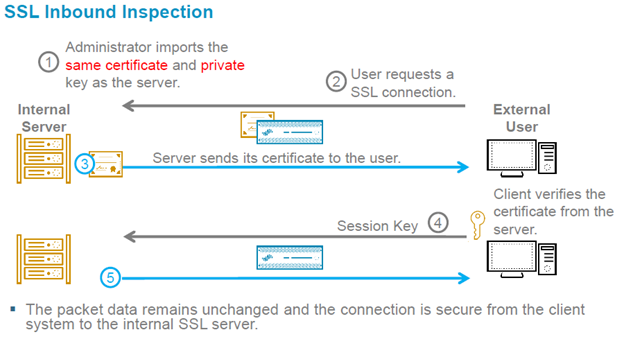 |
Hopefully is clearer for you now.
Ty,
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Digo11 ,
Not sure if you were kidding when you asked for "a way to skip/bypass the private key " 🙂.
From CKP HTTPS Inspection documentation, we have the below paragraph explaining what is need:
| When a client from outside the organization initiates an HTTPS connection to an internal server, the Security Gateway intercepts the traffic. The Security Gateway inspects the inbound traffic and creates a new HTTPS connection from the gateway to the internal server. To allow HTTPS Inspection, the Security Gateway must use the original server certificate and private key. The Security Gateway uses this certificate and the private key for SSL connections to the internal servers. |
Inbound HTTPS ConnectionsInbound connections are HTTPS connections that arrive from an external client and connect to a server in the DMZ or the internal network. Inbound connection flow
|
Now on your problem, you can't, because when we do INBOUND HTTP Inspection , meaning we decrypt traffic that comes from outside to our DMZ servers, the CKP HAS TO Present itself as the "original server", therefore, in order to do that, the server SSL certificate and the private key, needs to be installed to he can substitute itself into the communication.
As example:
 |
Hopefully is clearer for you now.
Ty,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sorin_Gogean,
Good day!!
Thanks a lot for explaining the connection flow. Somehow, I was able to import the certificate by entering the "export" password that I had created at the time of exporting the certificate. I had to convert the certificate to .P12 format as it was originally in .PEM format.
I used the certificate for inbound inspection and the traffic is getting inspected as seen in the logs. I will check further and post here if assistance is required.
Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good job! 👍
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad it helped @Digo11 😊
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What @Sorin_Gogean gave pretty much explains it all. Sadly, there is NO way to skip private key portion, thats the whole point actually of this process, otherwise, it would not be secure.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 12 | |
| 9 | |
| 8 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


