- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: In which cases would you use VSX?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In which cases would you use VSX?
Hello everyone.
I would like to hear your opinion and thoughts on the following topic.
Under which conditions the use of VSX on a cluster would really improve things? When would you prefer to use VSX over a usual setup? In other words, where is the line after which you decide "ok, this must be a VSX setup"?
The reason why I am thinking about this is that I cannot really see a lot of options for myself to use a VSX. I believe that in many usual cases adding VSX would just complicate things. VSX has some limitations, there are some additional things to be taken care of during operations like upgrades or migration, it should require additional hardware resources, as well as additional training of administrators.
Of course, VSX can bring several positive effects, which could weight out everything else (cost saving, flexibility, ease of adding new firewalls). But in my opinion this would work for only very few specific cases.
I can see two options when most probably I would use VSX:
1. One of the cases when VSX could be preferable is when your company is a service provider and needs to support similar services for many customers. It would mean the you need to have many similar firewalls in the same data center, but they also must be separated from each other - own policies and objects, administrators, logs, etc.
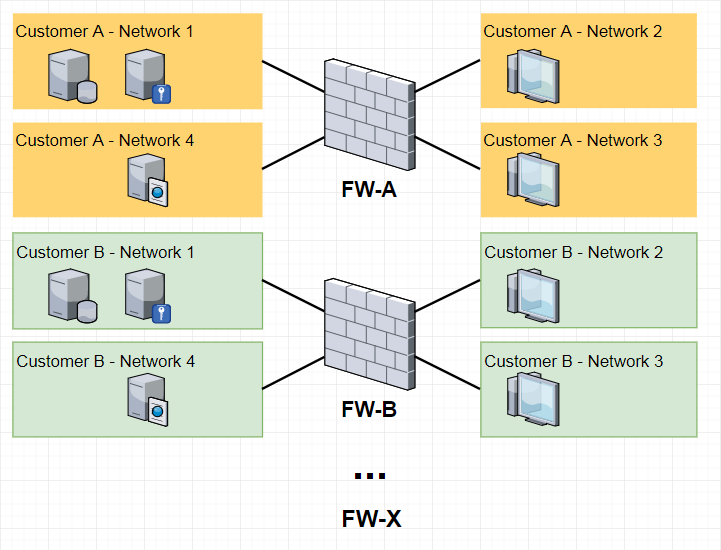
So, many similar firewalls for different customers, separated from each other. It will help to minimize cost and time for adding a new customer to the environment.
2. The second case is when you are working in a quite big company which has multiple appliances for different purposes - external/perimeter firewall, VPN and mobile access appliance, internal firewall, separate firewall for server networks, etc.
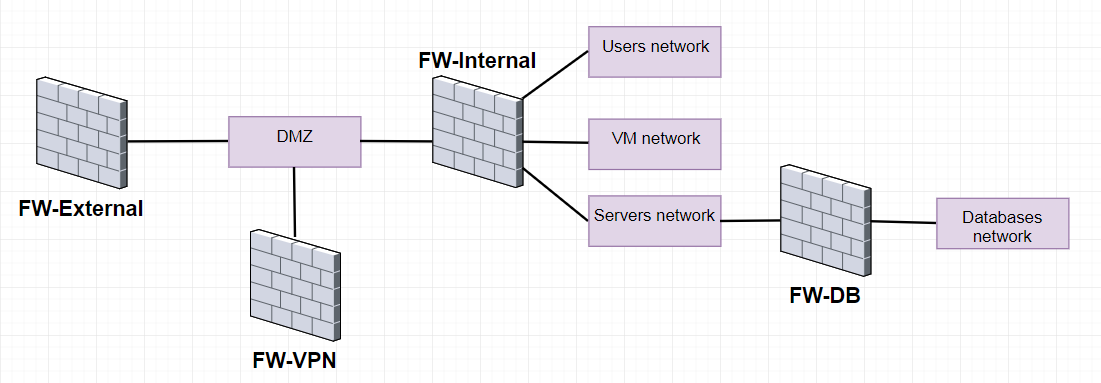
One company with multiple firewalls for different purposes. It most probably would save quite a lot of money on appliances and their support contracts and would add possibilities to create VS for new purposes without big changes.
But would it be better to use VSX for a new VPN-only gateway for example? Or when you have only external and internal firewalls in your network? What about when you replace your old almost end-of-life internal firewall to a new cluster and besides of that there is only a separate VPN gateway?
39 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand, but isn't same can be accomplished with sub-interfaces?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You cannot have different policies for different sub/interfaces of single gateway or cluster. Only one policy package could be enforced on non-VSX appliance or cluster.
This policy package will have same administrators and thus is not suitable for multi tenant implementation or segregation by security domains.
Vladimir Yakovlev
973.558.2738
vlad@eversecgroup.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even if you define each sub-interface as zone? With its own spoofing, rules, etc..?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Zones are not necessary in Check Point policies. You have different spoofing group for each interface without VSX. But you cannot install two policy packages on one logical gateway. You cannot connect one logical gateway to several domain management servers to have totally separate management databases (rules, objects, admins) for each customers/zones. You cannot have different blades enabled/disabled for different customers/zones. You cannot have different routing tables.
This is why we need VSX - we can have several logical systems on one physical device. So, you could have one VS in bridge mode with firewall doing some Geo Policies and checking traffic by IPS. You could have another VS with very strict firewall rules for one part of network, with enabled Anti-Virus, Anti-Bot, Application control blades. You can have another VS for Mobile Access blade. One VS for Customer-1 and one VS for Customer-2 separated from each other.
VSX is needed not for segmentation of just network, but for segmentation of bigger entities - functions, customers, zones (as in production traffic zone, test traffic zone, etc.).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aleksei,
in your experience, did you use VSXs in clustered configurations like HA or LS? Did you use dynamic routing per VSX or per VS in either configuration? or everything was static? Did you use subinterfaces per VS or physical interfaces of the hardware? What hardware did you use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The thing is that I don't use VSX at work anywhere, so don't have experience with it in production. There were some plans to implement VSX gateways, but we decided not to use it in our case. This is where my initial question came from.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oliver,
reading this blog again, very interesting stuff. Can you provide visual map like Aleksei did at the beginning of this post of such microsegmentation, you had to deal with. It will be cool?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would use VSX on R77.30 to use more VPN cores. Used this often on 23K or 61K systems. With R80.10 this doesn't matter any more, because it is MultiCore capable.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's an intresting idea to use more VPN cores of our R77.30. I hadn't thought about it!
Nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After my last 5 years’ experience, I must say that I'm fan of VSX. Of course as you read most probably in this thread already, it is important to find suitable and reasonable setup. In our company we decided to segment customers logically based on the industry are. In case there are no special needs like extra security, much customized configuration or large setup, then customers have opportunity to use our "shared" VSX clusters for their virtual firewalls. It could give you nice and cost effective product.
BUT there are negative factors as well:
- Software upgrades are complicated to prepare and manage. It is always much more time consuming against physical gateway (but you upgrades many customers/services together). It could be difficult to find suitable change window, but it is process topic.
- We are using external BGP quite often and I must say that the dynamic routing and routing daemon on Check Point is still painful stuff. Since R77.30 it is more stable and synchronization works perfectly.
- You should also plan your environment carefully as well. For example, during implementation nobody knows how many VSYSes and how big we'll want to use on on 12400 cluster. Therefore, we decided for maximum VSYS configuration and configure internal network suitable to it. After some time there we had there VSYS for one customer who wanted to add more interfaces than internal subnet allowed (it was 64 interfaces per virtual system for us). I must say that the changing of internal subnet size is always with quite long break unless you have spare devices where you can transfer configuration.
- VSLS or simple HA. VSLS is nice, you should just observe load there a little bit. In some factors, it could be limiting especially when you need to use some non-standard features as source based routing. This is possible on HA setup only.
- Virtual switches and virtual routers - here I think switches are perfectly fine. Virtual routers? From my experience, it is better to avoid them in case it is possible. Rather prefer physical router. It is hard to do some troubleshooting on it in case you need and dynamic routing could be painful on it (even 3 different TAC engineers were so confused with investigation one issue there so much that we rather implement different solution).
- Performance tuning when you have bigger load on particular virtual systems. This is something with which you must count and tune it if needed (connection table limits, assigned cores, core distribution, multiques...)
In conclusion, when you will invest time to collecting of requirements, make suitable design and implementation then VSX is nice and dynamic solution.
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 11 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


