- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: How to deal with SYN Attack or Syn Retransmiss...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to deal with SYN Attack or Syn Retransmission Attack ?
Hello Experts,
How to deal with SYN Attack or SYN Retransmission Attack ? Looking for some tips and best practices!!
Thanks,
Ven
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Val responded with the appropriate SKs to check out, the only best practice I would add is make sure you are using R80.20+ on your gateway. The Inspection Settings "SYN Attack" signature should not be enabled in R80.10 and earlier unless you are truly desperate, as it will disable acceleration for practically all traffic traversing the gateway by forcing it F2F. The performance impact of enabling it on R80.10 and earlier may end up being worse than the actual SYN flood itself. Here is the relevant page from my Max Power 2020 book mentioning this:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
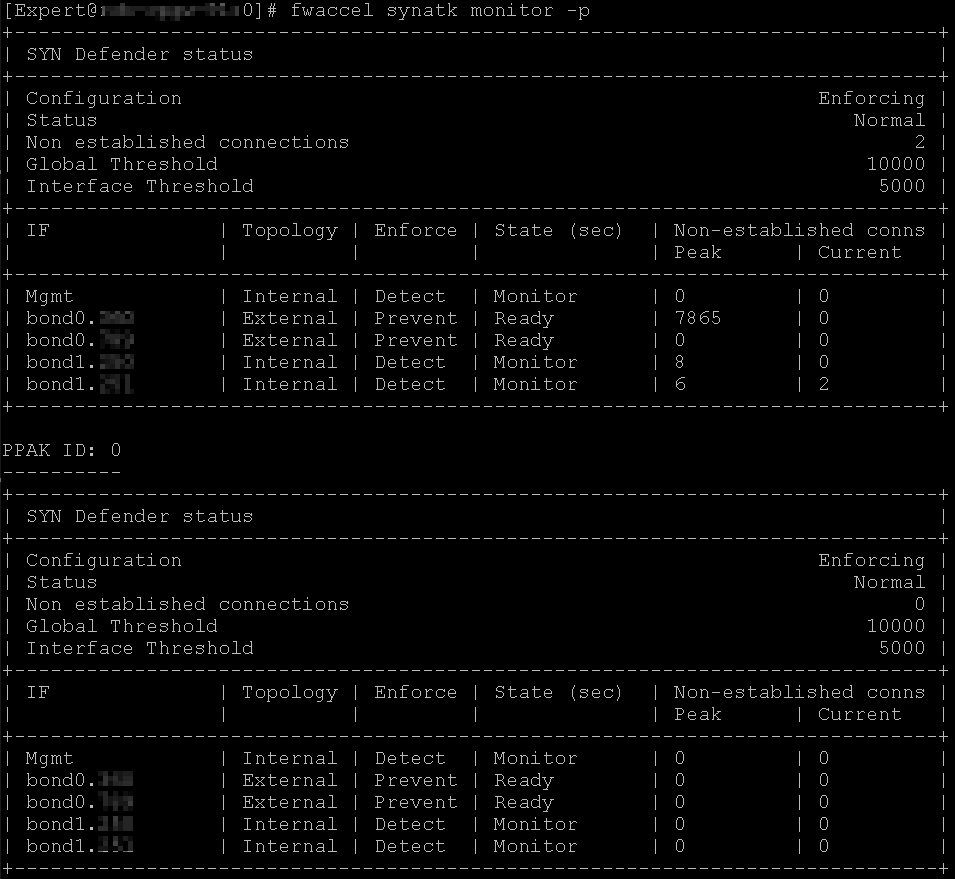
This is a screenshot from a blocked attack. I'm wondering about the lower part "PPAK ID: 0"
PPAK mean PerfomancePack or not ?
Was the attack blocked via SecureXL or not ?
Can someone explain the difference between the upper and lower part.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unless you have a Falcon accelerator card, there should always be only one instance of SecureXL (#0) irrespective of the number of SND/IRQ cores in your CoreXL split. Performance Pack (PPAK) and SecureXL more or less mean the same thing these days.
The upper part is the SYN Defender implementation in the Firewall Worker/Instance cores, and the lower part is in SecureXL/sim. Remember that the first packet of every new connection (TCP SYN) always goes to a Firewall Worker/Instance in R80.20+ (unlike R80.10 and earlier where SecureXL itself could match a new connection on a template), so it would make sense that most blocks are occurring on the Firewall Worker/Instance in the upper part. But SecureXL can enforce SYN Defender as well in R80.20+; it couldn't do that in earlier releases which led to all traffic subject to the SYN Defender protection going F2F in R80.10 and prior.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall you‘re right. The shown screenshot is from a R80.40 gateway attacked from a external system sending only syn packets with different source IPs, nothing else. These packets are handled by the firewall workers as you described.
„fwaccel synatk“ works, attackers are detected and blocked immediately. Not much overhead for this for all CPUs. Without „fwaccell synatk“ the same attack will be blocked by stateful inspection or cleanup rule, but with 95% CPU utilization on all cores.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's possibly worth noting a "SYN retransmission attack" is often caused by a connectivity problem. If the client doesn't get a SYN-ACK in response to its SYN, it will send the SYN again. If anything about the SYN changes, the firewall reports it as an attack. "Retransmitted SYN with different window scale", for example. This almost always means the client simply didn't hear back from the server.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter