- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026
Inception is On!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Disable NAT on SIP payload - breaks ICE
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Disable NAT on SIP payload - breaks ICE
How do we disable NAT on SIP and SDP payloads, when using NAT? The ATRG: VoIP documentation states the following:
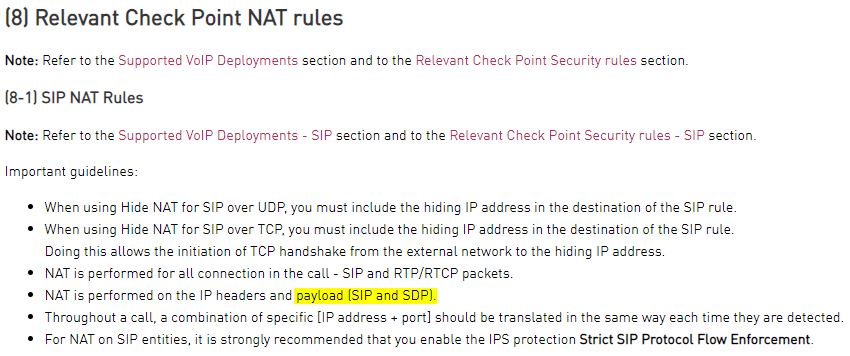
We're running Asterisk with ICE (Interactive Connectivity Establishment), which essentially provides multiple candidates in INVITE or SDP negotiation messages, where each is an IP and port combination. It discovers the public candidates by connecting to STUN servers on the public internet.
Why would we not want the security gateway to NAT the payload?
We intend on using Bria Stretto as a mobile SIP application. The app works perfectly in all environments, when in the foreground and subsequently registered directly to our office SIP server. The problem we're having is when the app is in the background, becoming completely inactive. Public SIP servers operated by CounterPath essentially register in place of the mobile and send a wake-up push notification when they receive a call. The push appears to provide the app with a copy of the original invite, so it should receive both the higher priority ICE host candidates as well as the lower priority server reflexive (natted IP and port) candidates.
The problem with the Check Point overwriting the SIP and SDP payload is that a mobile device connected to either private cellular APN or corporate WiFi will exclusively be provided with the public IP and results in one way audio. Everything works perfectly when the mobile is using LTE or natted through a home WiFi network.
What we're after:
We would simply like the Check Point to continue applying a NAT policy to the headers but leave the SIP and SDP payloads alone. This is typically accomplished by simply turning off SIP ALG processing.
Sample packet leaving SIP server towards CounterPath's public push servers:
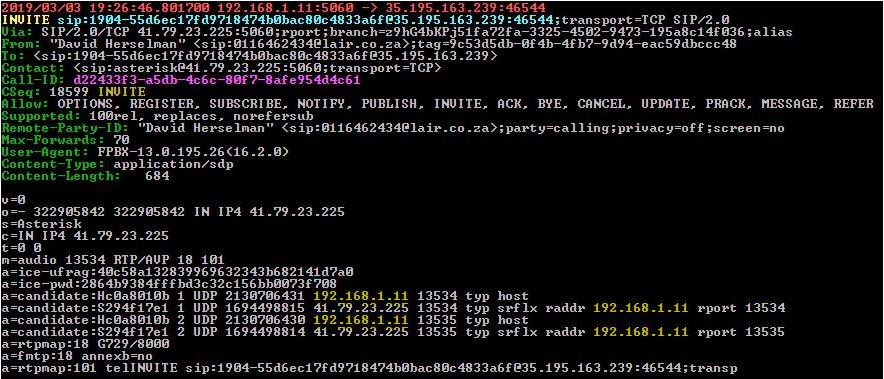
Sample packet after NAT processing by Check Point:
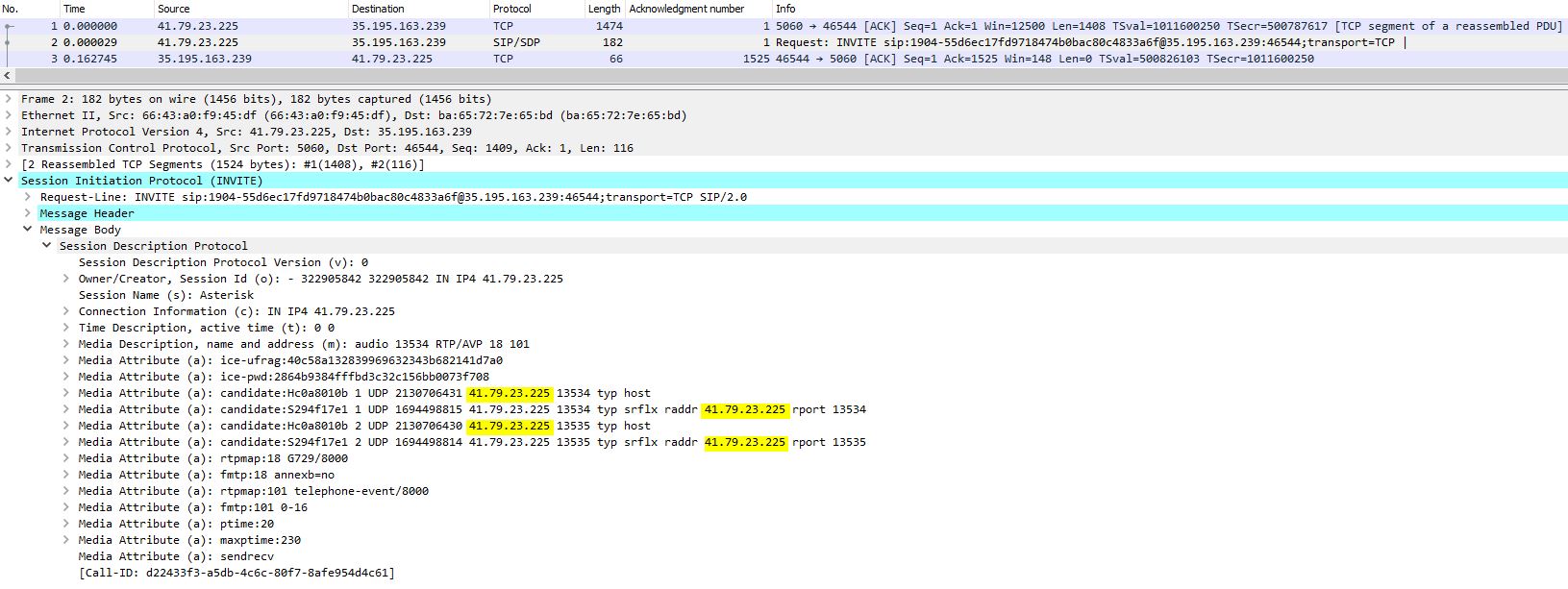
We have not had success in following the following recommendations. Both of these however appear to apply to cases where threat prevention policies were blocking packets, not the Check Point simply natting packets like any other UDP packet and leaving the payload alone:
- How to disable SIP ALG inspection in a specific rule in Checkpoint? Also Could this be done globally...
- Tried disabling SIP inspection
fw ctl set int voip_multik_enable_forwarding 0
echo voip_multik_enable_forwarding=0 >> $FWDIR/boot/modules/fwkern.conf
The following is an excellent summation of the ICE protocol:
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I hope I understand your problem!
If the following setting "fw ctl set int voip_multik_enable_forwarding 0" does not work, you still have the following option.
If you want to disable NAT in SIP content, you can also set the protocol type in SIP service TCP to "none". This should also disable the SPI inspection. Therefore no PSL should be used in the F2F path or no PXL should be used in the medium path. This means that the passive streaming library is no longer used. So no SIP packet is manipulated anymore. You can find out more about PSL/PXL here R80.x Security Gateway Architecture (Logical Packet Flow)or here https://community.checkpoint.com/docs/DOC-3073-r80x-security-gateway-architecture-content-inspection.
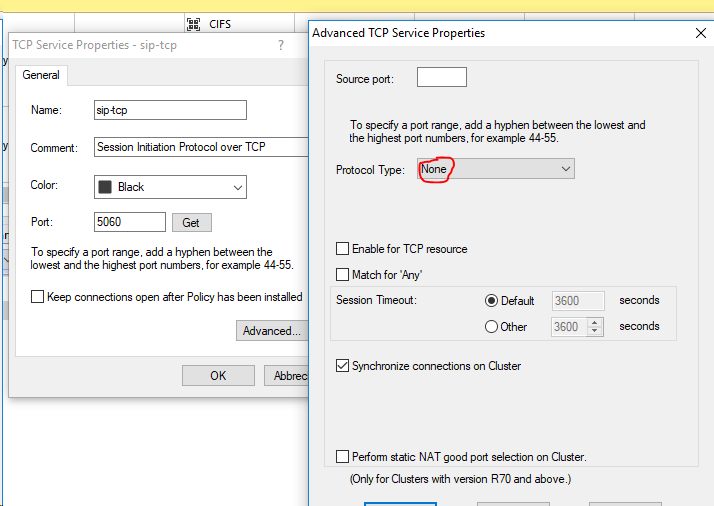
The problem is that the negotiated RTP ports are no longer written to the state table. So you have to allow all RTP UDP high ports in a rule.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I hope I understand your problem!
If the following setting "fw ctl set int voip_multik_enable_forwarding 0" does not work, you still have the following option.
If you want to disable NAT in SIP content, you can also set the protocol type in SIP service TCP to "none". This should also disable the SPI inspection. Therefore no PSL should be used in the F2F path or no PXL should be used in the medium path. This means that the passive streaming library is no longer used. So no SIP packet is manipulated anymore. You can find out more about PSL/PXL here R80.x Security Gateway Architecture (Logical Packet Flow)or here https://community.checkpoint.com/docs/DOC-3073-r80x-security-gateway-architecture-content-inspection.

The problem is that the negotiated RTP ports are no longer written to the state table. So you have to allow all RTP UDP high ports in a rule.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thanks for your suggestion, your explanation does make sense but it's unfortunately not working.
We're running MDS so the global 'sip-tcp' object can not be edited or disabled. We have already created a replacement sip_tcp object and configured it not to reference a protocol. The security gateway has additionally been set to disable voip_multik_enable_forwarding. These steps were detailed in How to disable SIP ALG inspection in a specific rule in Checkpoint? Also Could this be done globally....
Herewith snippets showing the custom service object for SIP TCP:
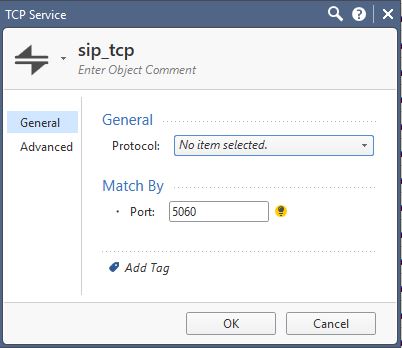
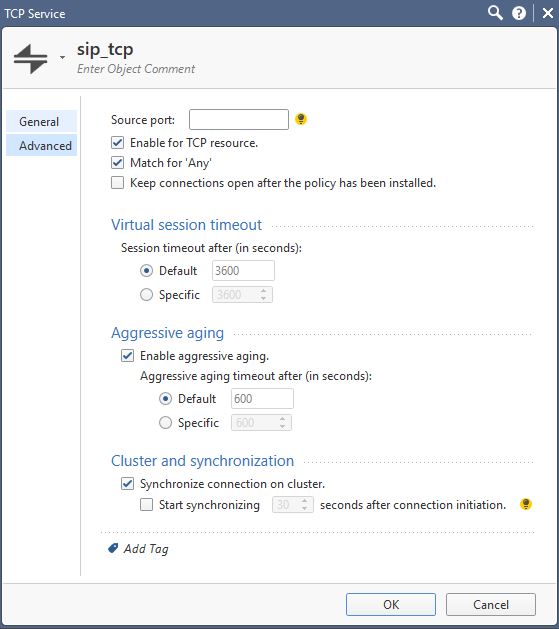
Herewith snippets showing the custom service object for SIP UDP:
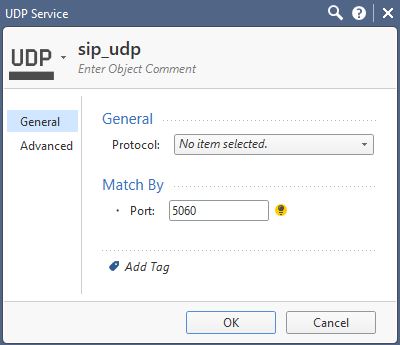
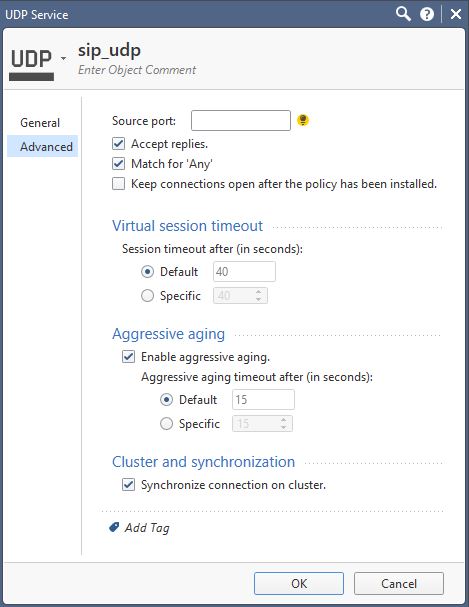
Searching for 'where used' on the default global objects shows no reference to these in the policies:
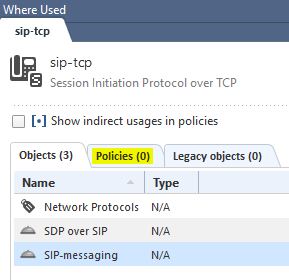
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hrm... Restarted the security gateway and it's now working. Packet capture after the Check Point NAT shows it behaving as we want it to:
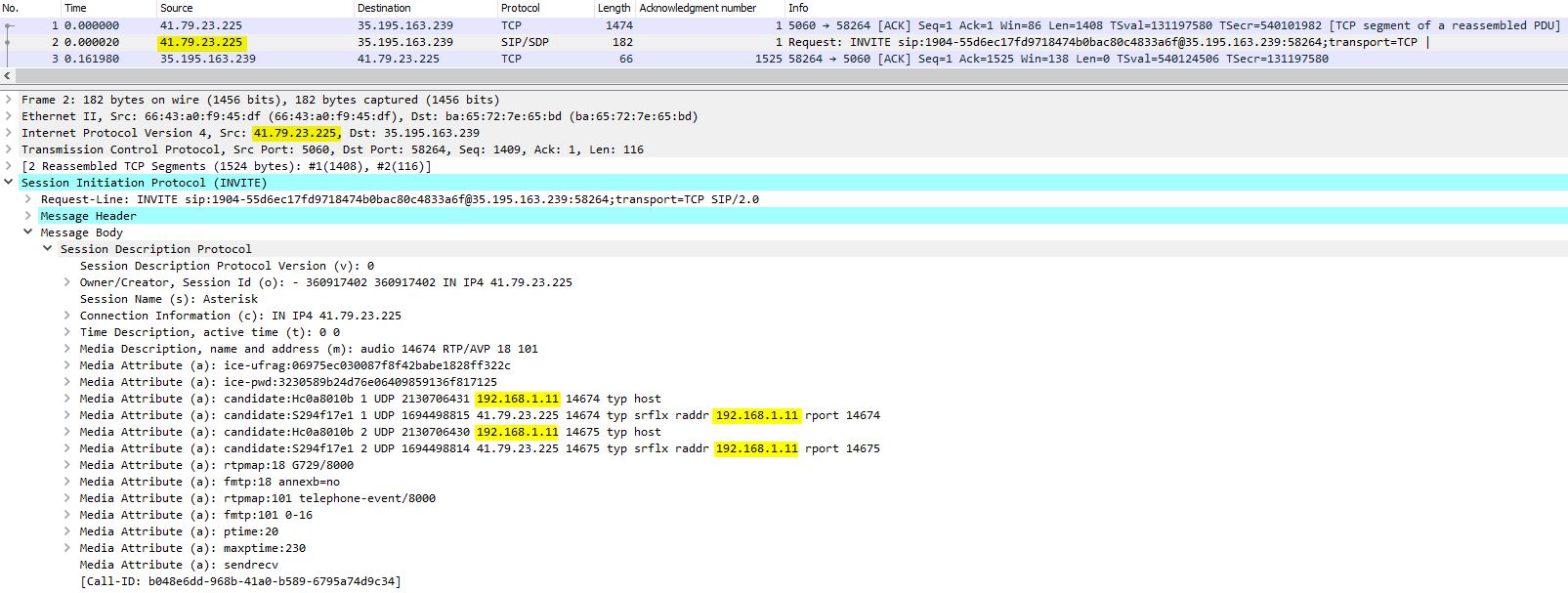
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some kernel variables cannot be changed on the fly with fw ctl set int and have the expected effect; adding them to fwkern.conf and rebooting the gateway is necessary. The relevant SKs don't say it is required for the voip_multik_enable_forwarding variable, but it sounds like this is the case based on your experience.
--
"IPS Immersion Training" Self-paced Video Class
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Timothy,
Are you aware of a document which details the effects of the voip_multik_enable_forwarding variable and others? Searching Google and Check Point Support Centre for 'voip_multik_enable_forwarding' only yields referencing to flipping the switch on this magic variable, not a proper explanation of exactly what it does or disables.
Check Point Support Centre:
How to disable 'fw early SIP nat' chain / SIP inspection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I'm reading the SKs correctly, and the fact that the variable contains "multik" (which is another word for CoreXL), I'd say if this variable is set to 1 (the default) it allows VoIP traffic including the SIP handler to be processed by several Firewall Workers (kernel instances) instead of all VoIP traffic being handled by instance 0 (typically the highest numbered CPU). In gateway releases prior to R80.10, most VoIP and IPSec VPN traffic could only be processed by the lowest-numbered Firewall Worker, as these inspection features were not completely compatible with CoreXL. Some portions of VoIP handling may still not be completely compatible with being spread around multiple worker cores by CoreXL, and I assume setting this variable to 0 moves all VoIP processing back onto a single worker core.
--
"IPS Immersion Training" Self-paced Video Class
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the same problem. One exception - the traffic goes through VPN tunnel. I changed SIP services to custom one.
No we have internal IP inside SIP packet but source still External IP of the gateway.
What should I do to change this situation? I need the packet to be with internal IP of the phone server as it goes through VPN site-to-site tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you find a solution to this prob ? if yes how did you rectified it
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 21 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


