- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: DNS Passive Learning Design Question
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DNS Passive Learning Design Question
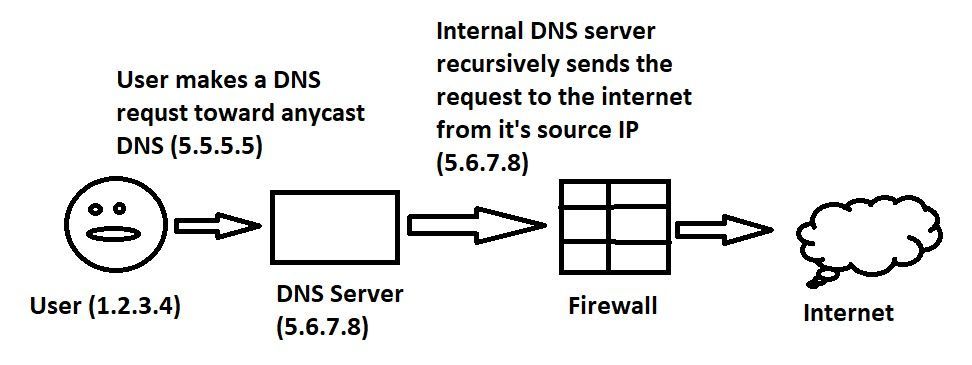
In regards to the new R80.40 feature, DNS Passive Learning, I'm curious if all DNS requests can be watched or only certain ones. sk161612 talks about using the same resolver as the gateway or configuring a setting in an object to mark it as a DNS server, but in this scenario, the firewall sees the needed DNS requests, just FROM the DNS servers making the recursive request to the internet. It does NOT see the request between the client and the DNS server. I don't know what recursive servers are on the internet, so I can't create objects there. Can the gateway watch the DNS between the DNS server AND the internet?
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only the requests to known DNS servers can be watched.
The reason for this is that DNS requests could traverse the gateway that are going to malicious DNS servers.
We assume the gateway is using a "trusted" DNS server.
Any other DNS server defined as described in sk161612 is considered trusted.
FYI, the list and IPs of the root name servers is well known and published: https://www.iana.org/domains/root/servers
What your internal DNS server is using is a different matter, and I assume whoever manages your DNS server can tell you that.
The reason for this is that DNS requests could traverse the gateway that are going to malicious DNS servers.
We assume the gateway is using a "trusted" DNS server.
Any other DNS server defined as described in sk161612 is considered trusted.
FYI, the list and IPs of the root name servers is well known and published: https://www.iana.org/domains/root/servers
What your internal DNS server is using is a different matter, and I assume whoever manages your DNS server can tell you that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What about requests FROM known DNS servers? Can those be watched?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DNS Passive Learning is a mechanism for constructing an IP / domain cache in which DNS traffic will be inspected and parsed for these purposes. This only works for defined DNS servers in an FW object. In this case the DNS answers are written to the FW DNS cache. It does not work for undefined DNS servers.
DNS Passive Learning is enabled by default in R80.40.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, the mechanism will only trust DNS information received from known DNS servers, regardless of who is making the query (a client or a DNS server).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgive me for asking, but what exactly is DNS Passive Learning from Checkpoint? I've been trying to do some searches both on the forums here, the Checkpoint KB's and the Internet as a whole and I'm getting glimpses of what it's supposed to do, but nothing is completely clear about what it provides? All of my DNS servers are marked as DNS servers on my firewalls as described, so I presume my gateways are using this DNS Passive Learning, but I don't know exactly what that means?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disclaimer: I don't have this setup as I'm waiting for an additional feature.
Check out sk161612 for more information.
This feature allows you to specify a domain (and the subdomains) to allow access to. Let's say a source needs access to *.something.biz and there isn't' a relevant application. You can try to write you own application, but often, that might not be feasible (think non-web encrypted traffic). The gateway can watch the DNS requests looking for anything that matches something.biz and store the corresponding IPs in its cache. This way when the rule in question is evaluated, the gateway can check the cache and allow/deny access.
A domain object won't work here because reverse DNS doesn't exist or doesn't match the site.
An FQDN domain object won't work here because you don't know all the FQDNs that will be called.
Make sense?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But, for this feature to work, queries to those trusted DNS servers must traverse the gateway.
Otherwise, we can't "learn" about these mappings passively.
Otherwise, we can't "learn" about these mappings passively.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have two questions regarding DNS passive learning:
1) will the DNS-entries, which are learned by DNS passive learning, be replicatet to the standby-member in an Cluster-environment (active/passive)
2) how can I querry the list which is learned by DNS passive learning. Can it be done with the "domains_tool"?
Thank you in advance
Best regards
Sascha
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. I'm not 100% sure, but checking it out on a cluster, I see some entries replicated for a domain, but not all. So I'm not sure if there is a time period before a sync or what.
2. domains_tool -d <domain> || domains_tool -ip <ip_addr>
One more side note on something I discovered. If you are watching the recursive traffic from a local DNS server to the authoritative name server and the request type is CNAME (not A), the firewall will not populate the entry since the response isn't an IP address and passive learning doesn't watch the chain. If the firewall is watching client to DNS server communications, this is NOT an issue since the DNS server will respond with the full chain (CNAME + A).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
it's been a while ( Since R55 ) lol
Can you clarify , but i believe so , if the customer has an internal DNS server behind the GW that is authoritative , so no forwarding nor relay to an external specific DNS server ( SP DNS for instance ) , it will not work right ?
as we need to declare the external DNS server to which requests will be monitored ...
i assume we need to declare a non-FQDN domain object as well , right ?
thanks ,
Farid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For DNS Passive Learning to work, the Security Gateway must be in the path to actually see the DNS Requests and the “trusted” DNS servers must be explicitly configured (either using the same DNS as configured in on the gateway OR explicitly configured DNS Server objects).
In the environment you’ve described, additional configuration will be required to make this work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you , i understand ...and this needs to be clarified with the customer for my particular use case.
can you confirm that it will enhance the situation where non-fqdn domain are used and in the case where no reverse dns entries exists in DNS ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure if this will work with non-FQDN.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 28 | |
| 16 | |
| 10 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 3 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter