- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Check Point R80.20 Now GA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point R80.20 Now GA
R80.20, part of the Check Point Infinity architecture, delivers the most innovative and effective security that keeps our customers protected against large scale, fifth generation cyber threats.
The release contains innovations and significant improvements in:
- Gateway performance
- Advanced Threat Prevention
- Cloud Security
- Access policy
- Consolidated network and endpoint management capabilities
- And much more
This release is initially recommended for customers who are interested in implementing the new features. We will make it the default version (widely recommended) after significant adoption and make it available in the 'Showing Recommended Packages' section in the CPUSE tab in Gaia portal.
 Performance Enhancements More
Performance Enhancements More
Performance Enhancements
- HTTPS Inspection performance improvements
- Session rate improvements on high-end appliances (13000, 15000, 21000 & 23000 Security Gateway models).
- Acceleration remains active during policy installation, no impact on Security Gateway performance.
VSX Gateways
- Significant boost to Virtual Systems performance, utilizing up to 32 CoreXL FW instances for each Virtual System.
- Dynamic Dispatcher - Packets are processed by different FW worker (FWK) instances based on the current instance load.
- Changes in the number of FW worker instances (FWK) in a VSLS setup do not require downtime.
- SecureXL Penalty Box supports the contexts of each Virtual System, see sk74520.
 Significant Improvements & New Features More
Significant Improvements & New Features More
Advanced Threat Prevention
- Enhanced configuration and monitor abilities for Mail Transfer Agent (MTA) in SmartConsole for handling malicious mails.
- Configuration of ICAP Server with Threat Emulation and Anti-Virus Deep Scan in SmartConsole.
- Automatic download of IPS updates by the Security Gateway.
- SmartConsole support for multiple Threat Emulation Private Cloud Appliances.
- SmartConsole support for blocking archives containing prohibited file types.
- Threat Extraction
- Full ClusterXL HA synchronization, access to the original files is available after a failover.
- Support for external storage.
- Advanced Threat Prevention Indicators (IoC) API
- Management API support for Advanced Threat Prevention Indicators (IoC).
- Add, delete, and view indicators through the management API.
- Advanced Threat Prevention Layers
- Support layer sharing within Advanced Threat Prevention policy.
- Support setting different administrator permissions per Advanced Threat Prevention layer.
- MTA (Mail Transfer Agent)
- MTA monitoring, e-mails history views and statistics, current e-mails queue status and actions performed on e-mails in queue.
- MTA configuration enhancements
- Setting a domain object as next hop.
- Ability to create an access rule to allow SMTP traffic to a Security Gateway.
- Create a dedicated Advanced Threat Prevention rule for MTA.
- MTA enforcement enhancements
- Replacing malicious links in an email with a configurable template.
- Configurable format for textual attachments replacement.
- Ability to add a customized text to malicious e-mails' body or subject.
- Tagging malicious-mails using X-header
- Sending a copy of the malicious e-mail to a predefined recipients list
- Improvements in policy installation performance on R80.10 and above Security Gateways with IPS
- Performance impact of "Suspicious Mail Activity" protection in Anti-Bot was changed to "High" and is now off by default
CloudGuard IaaS Enhancements
- Automated Security Transit VPC in Amazon Web Services (AWS) - Automatically deploy and maintain secured scalable architecture in Amazon Web Services.
- Integration with Google Cloud Platform.
- Integration with Cisco ISE.
- Integration with Nuage Networks.
- Automatic license management with the CloudGuard IaaS Central Licensing utility.
- Monitoring capabilities integrated into SmartView.
- Data center objects can now be used in access policy rules installed on 41000, 44000, 61000 and 64000 Scalable Platforms.
Access Policy
- Updatable Objects – a new type of network objects that represent an external service such as Office 365, Amazon Web Services, Azure GEO locations and more, and can be used in the Source and Destination columns of an Access Control policy. These objects are dynamically updated and kept up-to-date by the Security Gateway without the need to install a policy.
- Wildcard network object in Access Control that represents a series of IP addresses that are not sequential.
- Only for Multi-Domain Server: Support for scheduled policy installation with cross-Domain installation targets (Security Gateways or Policy Packages).
- Rule Base performance improvements, for enhanced Rule Base navigation and scrolling.
- Global VPN Communities (previously supported in R77.30).
- Support for using NAT64 and NAT46 objects in Access Control policy.
- Security Management Server can securely connect to Active Directory through a Security Gateway, if the Security Management Server has no connectivity to the Active Directory environment and the Security Gateway does.
Identity Awareness
- Identity Tags support the use of tags defined by an external source to enforce users, groups or machines in Access Roles matching.
- Improved SSO Transparent Kerberos Authentication for Identity Agent, LDAP groups are extracted from the Kerberos ticket.
- Two Factor Authentication for Browser-Based Authentication (support for RADIUS challenge/response in Captive Portal and RSA SecurID next Token/Next PIN mode).
- Identity Collector
- Support for Syslog Messages - ability to extract identities from syslog notifications.
- Support for NetIQ eDirectory LDAP Servers.
- Additional filter options - "Filter per Security Gateway" and "Filter by domain".
- Improvements and stability fixes related to Identity Collector and Web API.
- New configuration container for Terminal Servers Identity Agents.
- Active Directory cross-forest trust support for Terminal Servers Agent.
- Identity Agent automatic reconnection to prioritized PDP gateways.
- Security Management Server can securely connect to Active Directory via a Security Gateway if the Security Management Server has no connectivity to the Active Directory environment
HTTPS Inspection
- Hardware Security Module (HSM) support – outbound HTTPS Inspection stores the SSL keys and certificates on a third party dedicated appliance
- Additional ciphers supports for HTTPS Inspection (for more information, see sk104562)
Mirror and Decrypt
- Decryption and clone of HTTP and HTTPS traffic
- Forwarding traffic to a designated interface for mirroring purposes
Clustering
- New CCP Unicast - a new mode in which a cluster member sends the CCP packets to the unicast address of a peer member
- New Automatic CCP mode - CCP mode is adaptive to network changes, Unicast, Multicast or Broadcast modes are automatically applied according to network state
- Enhanced cluster monitoring capabilities
- Enhanced cluster statistics and debugging capabilities
- Enhanced Active/Backup Bond
- Support for more topologies for Synchronization Network over Bond interfaces
- Improved cluster synchronization and policy installation mechanism
- New grace mechanism for cluster failover for improved stability
- New cluster commands in Gaia Clish
- Improved clustering infrastructure for RouteD (Dynamic Routing) communication
Gaia OS
Upgraded Linux kernel (3.10) - applies to Security Management Server only
- New file system (xfs)
- More than 2TB support per a single storage device
- Enlarged systems storage (up to 48TB)
- I/O related performance improvements
- Support of new system tools for debugging, monitoring and configuring the system
iotop(provides I/O runtime statistics)lsusb(provides information about all devices connected to USB)lshw(provides detailed information about all hardware)lsscsi(provides information about storage)ps(new version, more counters)top(new version, more counters)iostat(new version, more counters)Advanced Routing:
- Allow AS-in-count
- IPv6 MD5 for BGP
- IPv4 and IPv6 OSPF multiple instances
- Bidirectional Forwarding Detection (BFD) for gateways and VSX, including IP Reachability detection and BFD Multihop
- OSPFv2 HMAC-SHA authentication (replaces OSPFv2 MD5 authentication)
ICAP Client
- Integrated ICAP Client functionality
 Security Management Enhancements More
Security Management Enhancements More
SmartConsole
- SmartConsole Accessibility features
- Keyboard navigation - ability to use the keyboard alone to navigate between the different SmartConsole fields
- Improved experience for the visually impaired, color invert for all SmartConsole windows
- Required fields are highlighted
- Multiple simultaneous sessions in SmartConsole. One administrator can publish or discard several SmartConsole private sessions, independently of the other sessions.
Logging and Monitoring
- Log Exporter - an easy and secure method to export Check Point logs over Syslog to any SIEM vendor using standard protocols and formats
- Ability to export logs directly from a Security Gateway (previously supported in R77.30)
- Unified logs for Security Gateway, SandBlast Agent and SandBlast Mobile for simplified log investigation
- Enhanced SmartView in browser:
- Log viewer with log card, column profile and statistics
- Export logs with custom or all fields
- Automatic-refresh for views
- Relative time frame support
- Improved log viewer with cards, profiles, statistics and filters
- I18N support for 6 languages (English, French, Spanish, Japanese, Chinese, Russian)
- Accessibility support - keyboard navigation and high contrast theme
SmartProvisioning
- Integration with SmartProvisioning (previously supported in R77.30)
- Support for the 1400 series appliances
- Administrators can now use SmartProvisioning in parallel with SmartConsole
Mobile Access
- Support for reCaptcha, keep abusive automated software activities from interfering with regular portal operations
- Support for One Time Password (OTP) without any hardware tokens
Endpoint Security Management Server
Endpoint Security Server is now part of the main train.
- Support for SandBlast Agent, Anti-Exploit and Behavioral Guard policies
- SandBlast Agent push operation to move/restore files from quarantine
- Directory Scanner initial scan and full rescan takes significantly less time
- Stability and performance enhancements for Automatic Synchronization (High Availability)
Endpoint Security Management features that are included in R77.30.03:
- Management of new Software Blades:
- SandBlast Agent Anti-Bot
- SandBlast Agent Threat Emulation and Anti-Exploit
- SandBlast Agent Forensics and Anti-Ransomware
- Capsule Docs
- New features in existing Software Blades:
- Full Disk Encryption
- Offline Mode
- Self Help Portal
- XTS-AES Encryption
- New options for the Trusted Platform Module (TPM)
- New options for managing Pre-Boot Users
- Media Encryption & Port Protection
- New options to configure encrypted container
- Optical Media Scan
- Anti-Malware:
- Web Protection
- Advanced Disinfection
Compliance
- User can create custom best practices based on scripts
- Support for 35 regulations including General Data Protection Regulation (GDPR)
Download and release information here: Check Point R80.20
131 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are two different installation ISOs for R80.20:
- One that supports gateways and standalone installs with the older (2.6.18) kernel
- One for Security Management only that has the newer (3.10) kernel
So yes, you can upgrade a standalone to R80.20.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you do an in place upgrade of an R80.10 management server to R80.20 will the kernel be updated or does this require a fresh build and migrate export/import?
Iain
CISSP
CISSP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kernel is upgraded on in-place upgrades, but filesystem change from ext3 to xfs is not carried out. This requires advanced upgrade (export/import).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I was going to upgrade from r80.10 to r80.20 soon. You mentioned the "ext3 to xfs is not carried out" is this required and how to access advanced upgrade (export/import)?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is related to 3.10.X versions: New Linux Kernel Bug Affects Red Hat, CentOS, and Debian Distributions
Does it effects to Management of R80.20?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In order to exploit this, you'd have to be an authorized user (most likely an admin of some sort) and get to expert mode (i.e. not be in clish).
That assumes the bug is present in our kernel, which I can't say for sure.
In any case, these sorts of issues tend to get addressed in later releases/jumbo hotfixes since they pose no immediate risk.
Of course, this is just my initial assessment and should not be construed as official.
My guess is an official SK will appear on this in the near future.
If it's urgent, I recommend opening a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
same for the HP Gen10, it's very annoying that checkpoint hasn´t managed to fix support for this even after 1year+
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ProLiant DL360 Gen10 + ProLiant DL380 Gen10
Both supported with R80.20 MGMT : https://www.checkpoint.com/support-services/hcl/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Clarification: future of HCL (hardware compatibility):
Open server compatibility is expected to be much better with the new linux release.
As i explained above, mgmt GA works w the updated linux (so it is integrated in the GA). Updated HCL was published (mgmt is user space and therefore simpler).
We also have EA with r80.20 variant based on updated linux for GA - you are welcome to join this EA asap. With this release we will have the latest open servers supported in timely manner (so we hope to put to delayed HCL behind us, once we release the variant that works on the new linux).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply Dorit, is this GW EA also for VSX?
Within the open servers for HCL are you testing the new 25G nic together with the new servers?
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. The gw variant for new linux is in production EA for both open servers and clous usage
2. VSX w new linux is developed but not yet ready for EA. Why? With the gw move to new linux, the biggest change is replacing the VFRF module with “Name spaces” as VFRF no longer exist. So we released Gw-non-VSX first and now we are QAing the VSX. The exact date of EA for VSX depends on our quality validation and is expected to happen this quarter.
If you will join the EA for the new kernel GW, you will also get updates on the missing functionality (vsx)
Last: The exact functionality we certified for open server is based on priorities from the field (at the end we want to cerify everything possible and we believe that w the new kernel the time to market and quality of open servers support will be dramatically better and we can support anything needed).
To impact the order/priority of certifications for HCL, contact the local field and get them to present the business case to our solution center (the entity that manages the field priritization to such things)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does this mean that VSX is not jet working/supported in R80.20 gateways we can download from sk122485?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, there is a GA for gateway with R80.20 with kernel 2.6 (same kernel as R80.10) which is fully supported.
In parallel there is an EA for gateway with R80.20 with kernel 3.10 (same kernel as R80.20 Mgmt GA and R80.20.M1), which has limited scope.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And now I also understand ![]()
Thank you Norbert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sure we are aware of that, the question is specifically for GW.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cluster object name still cannot be the same as policy package name (and vice versa). Is there any special reason for that ? Beside that the name will be the same ?
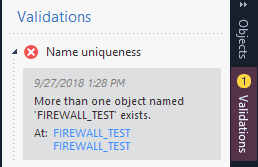
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me guess, you are trying to upgrade from R77.30, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, fresh installation of R80.20 MDS and playing with it around 10 minutes.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay. One of the limitations with R80.10 and up: unique names for everything. Name your policy package as FIREWALL_TEST_POLICY, that would do
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yep, this also happens in case you are going to create for example new Network Group with the name exactly the same as something else ...
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct. Each object HAS to have a unique name
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And to use a clear naming convention is useful for ages now (and so you don't run is such problems) ![]()
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Management API Version 1.3 released
Check Point - Management API reference
What's New in v1.3
This release, API version 1.3, introduces several new features and several changes.
New features:
- Updatable Object.
- Show objects as ranges:
- Show rules as ranges of IP addresses and ports instead of Check Point Objects.
- Show a nested group, group-with-exclusion or service-group as the accumulative ranges of IP addresses and ports.
- Show objects as ranges enables you to:
- Describe policies in a non-Check Point-language.
- Run custom validations easily.
- Find rules that are similar to your new rule request.
- Changes to the overrides parameter in the set threat protection:
- The option to add override (overrides > add) is no longer supported. Instead perform a set operation on the protection's override.
- The option to set override (overrides > set) for specific profile will change the override for this profile only, other profiles will not be changed.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon hi,
Now when R80.20 is released, do we know exact date when Falcon network cards will be released in catalogs?
BR
Vato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Offhand I do not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, do you have any news about this new feature indicated in r80.20 EA?
- HTTPS Inspection now works in conjunction with HTTPS web sites categorization. HTTPS traffic that is bypassed will be categorized.
There isn't in r80.20 GA?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Occasionally EA features do not make the GA.
I will check.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like this was added to R80.20.
It's listed in this SK as a Resolved issue: R80.20 GA and R80.20 Management Feature Release Resolved Issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, thanks for reply.
This is the bug fix note:
The "Categorize HTTPS sites" feature does not work when HTTPS Inspection is enabled. Refer to sk90840.
The sk indicated (sk90840) isn't linked to this issue:
sk90840 - HTTPS Inspection is not supported for IPv6 traffic in R76 / R77.X / R80.10
Can you verify?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure why they linked that SK to it, but good catch.
If the feature doesn't work as advertised, I'd say: open a TAC ticket. ![]()
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 11 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


