- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Check Point R80.20 Now GA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point R80.20 Now GA
R80.20, part of the Check Point Infinity architecture, delivers the most innovative and effective security that keeps our customers protected against large scale, fifth generation cyber threats.
The release contains innovations and significant improvements in:
- Gateway performance
- Advanced Threat Prevention
- Cloud Security
- Access policy
- Consolidated network and endpoint management capabilities
- And much more
This release is initially recommended for customers who are interested in implementing the new features. We will make it the default version (widely recommended) after significant adoption and make it available in the 'Showing Recommended Packages' section in the CPUSE tab in Gaia portal.
 Performance Enhancements More
Performance Enhancements More
Performance Enhancements
- HTTPS Inspection performance improvements
- Session rate improvements on high-end appliances (13000, 15000, 21000 & 23000 Security Gateway models).
- Acceleration remains active during policy installation, no impact on Security Gateway performance.
VSX Gateways
- Significant boost to Virtual Systems performance, utilizing up to 32 CoreXL FW instances for each Virtual System.
- Dynamic Dispatcher - Packets are processed by different FW worker (FWK) instances based on the current instance load.
- Changes in the number of FW worker instances (FWK) in a VSLS setup do not require downtime.
- SecureXL Penalty Box supports the contexts of each Virtual System, see sk74520.
 Significant Improvements & New Features More
Significant Improvements & New Features More
Advanced Threat Prevention
- Enhanced configuration and monitor abilities for Mail Transfer Agent (MTA) in SmartConsole for handling malicious mails.
- Configuration of ICAP Server with Threat Emulation and Anti-Virus Deep Scan in SmartConsole.
- Automatic download of IPS updates by the Security Gateway.
- SmartConsole support for multiple Threat Emulation Private Cloud Appliances.
- SmartConsole support for blocking archives containing prohibited file types.
- Threat Extraction
- Full ClusterXL HA synchronization, access to the original files is available after a failover.
- Support for external storage.
- Advanced Threat Prevention Indicators (IoC) API
- Management API support for Advanced Threat Prevention Indicators (IoC).
- Add, delete, and view indicators through the management API.
- Advanced Threat Prevention Layers
- Support layer sharing within Advanced Threat Prevention policy.
- Support setting different administrator permissions per Advanced Threat Prevention layer.
- MTA (Mail Transfer Agent)
- MTA monitoring, e-mails history views and statistics, current e-mails queue status and actions performed on e-mails in queue.
- MTA configuration enhancements
- Setting a domain object as next hop.
- Ability to create an access rule to allow SMTP traffic to a Security Gateway.
- Create a dedicated Advanced Threat Prevention rule for MTA.
- MTA enforcement enhancements
- Replacing malicious links in an email with a configurable template.
- Configurable format for textual attachments replacement.
- Ability to add a customized text to malicious e-mails' body or subject.
- Tagging malicious-mails using X-header
- Sending a copy of the malicious e-mail to a predefined recipients list
- Improvements in policy installation performance on R80.10 and above Security Gateways with IPS
- Performance impact of "Suspicious Mail Activity" protection in Anti-Bot was changed to "High" and is now off by default
CloudGuard IaaS Enhancements
- Automated Security Transit VPC in Amazon Web Services (AWS) - Automatically deploy and maintain secured scalable architecture in Amazon Web Services.
- Integration with Google Cloud Platform.
- Integration with Cisco ISE.
- Integration with Nuage Networks.
- Automatic license management with the CloudGuard IaaS Central Licensing utility.
- Monitoring capabilities integrated into SmartView.
- Data center objects can now be used in access policy rules installed on 41000, 44000, 61000 and 64000 Scalable Platforms.
Access Policy
- Updatable Objects – a new type of network objects that represent an external service such as Office 365, Amazon Web Services, Azure GEO locations and more, and can be used in the Source and Destination columns of an Access Control policy. These objects are dynamically updated and kept up-to-date by the Security Gateway without the need to install a policy.
- Wildcard network object in Access Control that represents a series of IP addresses that are not sequential.
- Only for Multi-Domain Server: Support for scheduled policy installation with cross-Domain installation targets (Security Gateways or Policy Packages).
- Rule Base performance improvements, for enhanced Rule Base navigation and scrolling.
- Global VPN Communities (previously supported in R77.30).
- Support for using NAT64 and NAT46 objects in Access Control policy.
- Security Management Server can securely connect to Active Directory through a Security Gateway, if the Security Management Server has no connectivity to the Active Directory environment and the Security Gateway does.
Identity Awareness
- Identity Tags support the use of tags defined by an external source to enforce users, groups or machines in Access Roles matching.
- Improved SSO Transparent Kerberos Authentication for Identity Agent, LDAP groups are extracted from the Kerberos ticket.
- Two Factor Authentication for Browser-Based Authentication (support for RADIUS challenge/response in Captive Portal and RSA SecurID next Token/Next PIN mode).
- Identity Collector
- Support for Syslog Messages - ability to extract identities from syslog notifications.
- Support for NetIQ eDirectory LDAP Servers.
- Additional filter options - "Filter per Security Gateway" and "Filter by domain".
- Improvements and stability fixes related to Identity Collector and Web API.
- New configuration container for Terminal Servers Identity Agents.
- Active Directory cross-forest trust support for Terminal Servers Agent.
- Identity Agent automatic reconnection to prioritized PDP gateways.
- Security Management Server can securely connect to Active Directory via a Security Gateway if the Security Management Server has no connectivity to the Active Directory environment
HTTPS Inspection
- Hardware Security Module (HSM) support – outbound HTTPS Inspection stores the SSL keys and certificates on a third party dedicated appliance
- Additional ciphers supports for HTTPS Inspection (for more information, see sk104562)
Mirror and Decrypt
- Decryption and clone of HTTP and HTTPS traffic
- Forwarding traffic to a designated interface for mirroring purposes
Clustering
- New CCP Unicast - a new mode in which a cluster member sends the CCP packets to the unicast address of a peer member
- New Automatic CCP mode - CCP mode is adaptive to network changes, Unicast, Multicast or Broadcast modes are automatically applied according to network state
- Enhanced cluster monitoring capabilities
- Enhanced cluster statistics and debugging capabilities
- Enhanced Active/Backup Bond
- Support for more topologies for Synchronization Network over Bond interfaces
- Improved cluster synchronization and policy installation mechanism
- New grace mechanism for cluster failover for improved stability
- New cluster commands in Gaia Clish
- Improved clustering infrastructure for RouteD (Dynamic Routing) communication
Gaia OS
Upgraded Linux kernel (3.10) - applies to Security Management Server only
- New file system (xfs)
- More than 2TB support per a single storage device
- Enlarged systems storage (up to 48TB)
- I/O related performance improvements
- Support of new system tools for debugging, monitoring and configuring the system
iotop(provides I/O runtime statistics)lsusb(provides information about all devices connected to USB)lshw(provides detailed information about all hardware)lsscsi(provides information about storage)ps(new version, more counters)top(new version, more counters)iostat(new version, more counters)Advanced Routing:
- Allow AS-in-count
- IPv6 MD5 for BGP
- IPv4 and IPv6 OSPF multiple instances
- Bidirectional Forwarding Detection (BFD) for gateways and VSX, including IP Reachability detection and BFD Multihop
- OSPFv2 HMAC-SHA authentication (replaces OSPFv2 MD5 authentication)
ICAP Client
- Integrated ICAP Client functionality
 Security Management Enhancements More
Security Management Enhancements More
SmartConsole
- SmartConsole Accessibility features
- Keyboard navigation - ability to use the keyboard alone to navigate between the different SmartConsole fields
- Improved experience for the visually impaired, color invert for all SmartConsole windows
- Required fields are highlighted
- Multiple simultaneous sessions in SmartConsole. One administrator can publish or discard several SmartConsole private sessions, independently of the other sessions.
Logging and Monitoring
- Log Exporter - an easy and secure method to export Check Point logs over Syslog to any SIEM vendor using standard protocols and formats
- Ability to export logs directly from a Security Gateway (previously supported in R77.30)
- Unified logs for Security Gateway, SandBlast Agent and SandBlast Mobile for simplified log investigation
- Enhanced SmartView in browser:
- Log viewer with log card, column profile and statistics
- Export logs with custom or all fields
- Automatic-refresh for views
- Relative time frame support
- Improved log viewer with cards, profiles, statistics and filters
- I18N support for 6 languages (English, French, Spanish, Japanese, Chinese, Russian)
- Accessibility support - keyboard navigation and high contrast theme
SmartProvisioning
- Integration with SmartProvisioning (previously supported in R77.30)
- Support for the 1400 series appliances
- Administrators can now use SmartProvisioning in parallel with SmartConsole
Mobile Access
- Support for reCaptcha, keep abusive automated software activities from interfering with regular portal operations
- Support for One Time Password (OTP) without any hardware tokens
Endpoint Security Management Server
Endpoint Security Server is now part of the main train.
- Support for SandBlast Agent, Anti-Exploit and Behavioral Guard policies
- SandBlast Agent push operation to move/restore files from quarantine
- Directory Scanner initial scan and full rescan takes significantly less time
- Stability and performance enhancements for Automatic Synchronization (High Availability)
Endpoint Security Management features that are included in R77.30.03:
- Management of new Software Blades:
- SandBlast Agent Anti-Bot
- SandBlast Agent Threat Emulation and Anti-Exploit
- SandBlast Agent Forensics and Anti-Ransomware
- Capsule Docs
- New features in existing Software Blades:
- Full Disk Encryption
- Offline Mode
- Self Help Portal
- XTS-AES Encryption
- New options for the Trusted Platform Module (TPM)
- New options for managing Pre-Boot Users
- Media Encryption & Port Protection
- New options to configure encrypted container
- Optical Media Scan
- Anti-Malware:
- Web Protection
- Advanced Disinfection
Compliance
- User can create custom best practices based on scripts
- Support for 35 regulations including General Data Protection Regulation (GDPR)
Download and release information here: Check Point R80.20
131 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
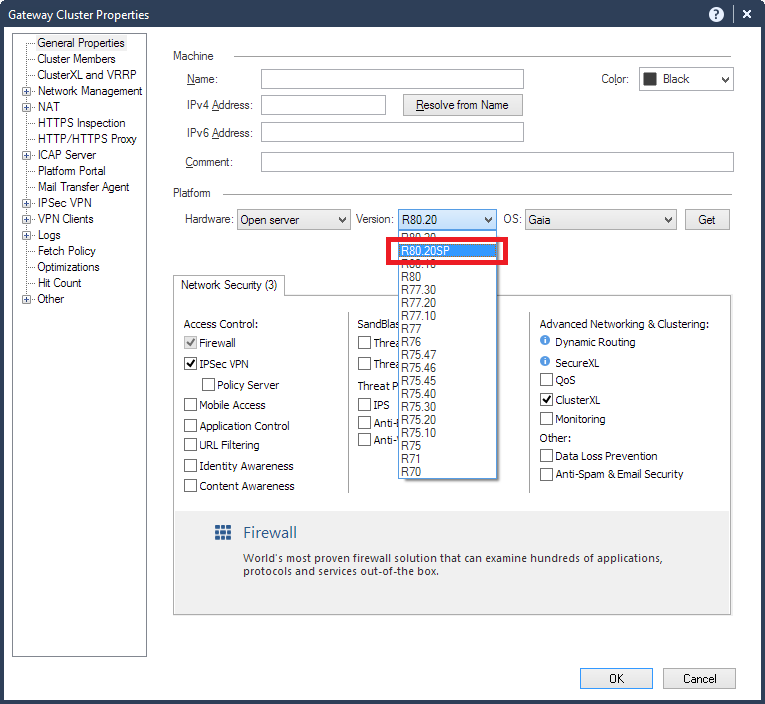
What kind of version is R80.20SP ?
EDIT: Was mentioned in this thread by Maor Elharar ... R80.20 for Scalable Platform
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SP means "Scalable Platform", which refers to 41/61k and 44/64k chassis based systems.
Current SP release is R76SP.50 because the branch was forked from R76 release and then developed in parallel.
R76SP.50 had already some features which didn't make it in R77.30/R80.10 maintrain, but on the other hand was missing others. With R80.20SP as far as I heard Check Point wants to close the gaps ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a rough ETA on R80.20SP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andreas,
You can found some ETA hereWill SP code ever get migrated into main R80.x code train?
If you are interested in R80.20SP EA (R80.20 for Scalable Platform) program you can contact Maor Elharar (maor@checkpoint.com )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
will the first release of R80.20SP support VSX? or is that going to be added later?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, VSX will be support on the first release of R80.20SP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After playing around with R80.20GA gateway for a few hours, the following things caught my eye:
1) Gaia is now required to be 64-bit.
2) Geo Protection can now be directly configured in a whitelist configuration (allow some countries and deny all others).
3) R80.20 gateway ClusterXL does not support Load Sharing (Active/Active) yet? Not a huge fan of load sharing to begin with but this is taking it to another level... 🙂
4) R80.20 gateways cannot be managed by an R80.20M1 SMS.
5) cphaprob state command now reports *far* more detail about ClusterXL state, including why the current member is active, last state transition & failover count, and active pnote problems. This extra information appears to be available separately via the new cphaprob show_failover command.
6) cphaconf set_ccp has two new options: auto and unicast (the latter only works with a 2-member cluster); used to just be broadcast and multicast.
7) Syn Attack (Syn Flood) protection is now implemented in SecureXL and will not cause all traffic handled by it to go F2F. Just mentioned this limitation in my TechTalk this week, quite ironic...
8) The undocumented ability for certain ports to be bypassed in the Dynamic Dispatcher mentioned on p. 245 of my book appears to be officially supported via the fw ctl multik add_bypass_port command among others.
9) The new fw ctl multik get_instance command can be used to identify which Firewall Worker core is handling a connection with the matching attributes specified on the command line.
10) The new fw ctl multik print_heavy _conn command will show the attributes of all "heavy" (elephant flow) connections currently pounding the Firewall Worker cores.
11) The new fw ctl multik utilize command will show the size & utilization of the Firewall Worker packet queues.
12) Many new screens added to cpview including Dynamic Routing Stats (routed), Hardware Health & Sensors, Disk I/O utilization, and Advanced...CPAQ.
13) Apparently fw monitor can now capture all traffic traversing the firewall regardless of whether it is accelerated by SecureXL. Haven't had a chance to verify this myself yet.
14) The long-awaited Network defined by routes antispoofing topology option checks the gateway routing table every second for any route changes that might impact antispoofing enforcement, the timer controlling this interval is located in the SmartConsole under Manage & Settings...Preferences.
15) I don't see the option to define VPN domains per VPN Community, at least not in the SmartConsole.
16) Ensuring that "Font Smoothing" is enabled in your RDP client substantially improves the graphical performance of the SmartConsole inside an RDP Session.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
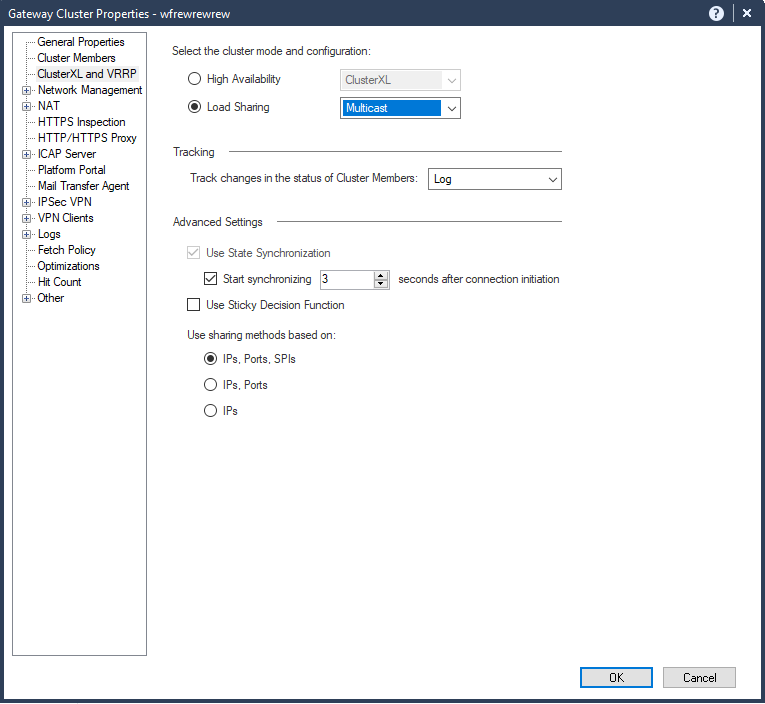
Regarding Load Sharing (Active/Active) configuration - This morning I managed this configuration. At list in my Lab, it works fine ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Concerning Load Sharing here is the Known Limitation from sk122486: R80.20 GA and R80.20 Management Feature Release Known Limitations
| MB-30 | R80.20 ClusterXL does not support Load Sharing mode. Therefore, R80.20 SmartConsole blocks such configuration with a warning message. This limitation is planned to be resolved during H1 2019. | R80. |
Curious that you were able to configure it, but just because you were able to do so doesn't mean it is a supported configuration based on the above.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can configure load sharing with R80.20 SmartConsole for clusters that aren't in version R80.20.
Do you think we should rephrase the sentence at Known Limitations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, perhaps clarify that R80.20 *gateway* does not support ClusterXL Load Sharing. It was clear to me that the R80.20 SmartConsole can still configure it for older gateway objects though.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
(1) If the version of the ClusterXL object is R80.20, then SmartConsole will not let you configure the LS mode.
You will get an explicit pop-up that says so.
(2) Is this text not clear enough "R80.20 ClusterXL does not support Load Sharing mode. Therefore, R80.20 SmartConsole blocks such configuration with a warning message." ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your feedback!
I like the fact that you point out the features that matter to you. To me this sometimes means more than your impressions on the features themselves.
We are also interested with feedback on: configuring countries and cloud servers in your security policy; changing the IPS workflow with gateways fetching updates independently, automatically preventing, while still managing the protection state and follow-up flags through SmartConsole; scheduling policy installations with Multi-Domain Security Management; and configuring malicious email policy with the Threat Prevention Profiles.
Maybe with a thread per feature.
Indeed, font smoothing works wonders with R80 SmartConsole and above [https://community.checkpoint.com/thread/6950-how-to-make-smartconsole-look-good-even-with-terminal-s... ]
And we hear your feedback at VPN domains per VPN community, loud and clear ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The fw monitor improvement sounds very good as I always forget fwaccel off prior to fw monitor ![]()
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you look at it this way...other people forget to turn it back on after a troubleshoot session.
My blog: https://checkpoint.engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
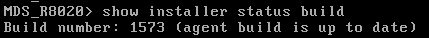
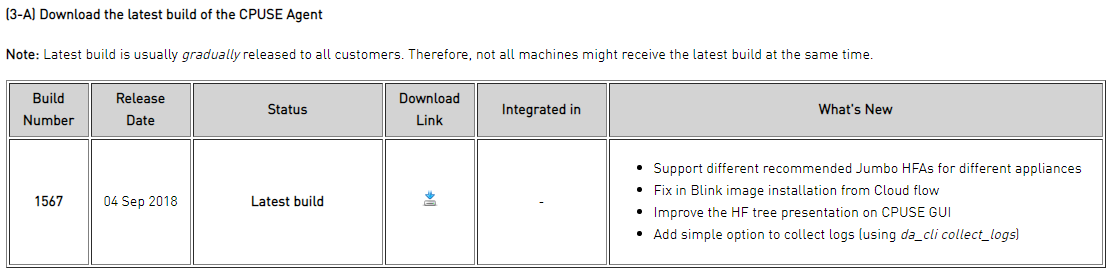
Just discovered that build version of Check Point Upgrade Service Engine (CPUSE) - Gaia Deployment Agent on R80.20 GA has been updated to the 1573, despite it isnt available for download (according SK, the latest version is 1567).
In addition, the download link isnt working anymore ?
The file you were trying to load could not be found or has been deleted.
CPinfo utility on R80.20 GA is the same version (182) as on R80.10 or R77.30. No changes there.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are correct, we had an issue with the SK, and it is now fixed. The latest CPUSE deployment agent is 1573 and now it can be downloaded from the SK.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Few answers
1. R80.20SP is in EA - ready for production. You are welcome to join. GA in Q4 and more EAs will help release faster
2. New kernel:
A. Integrated in the GA for user space (cpuse pkg for mgmt is part of the GA)
B. Kernel (mgmt+gw) requires different software variant for now. Its already in EA for cloud and open server. Join the EA if you want to run it in production now and on the way, learn more and contribute feedback.
3. Upgrade of every release to R80.20 uses the normal CPUSE package and is fully supported, except R80.20M1 which is different.
Why? We started to implement new/improved mgmt upgrade code which in the future will be our standard code and right now is only implemented from M1 to GA. So M1 upgrade is still “escorted”. We have now updateability to the update code itself, so we can later (after its fully tested) make the m1 upgrade also go thru the normal CPUSE package.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oops missed #4
4. Accelerator card support is in EA and runs in production - please join the EA and help us get it released faster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you email me with more info about what the accelerator card will do, what appliances it will work in, etc? How do I join the EA for this? I'm very interested in this, particularly for SSL offload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're welcome to review R80.20 Security Management features with Check Point R80.x Cloud Demo

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure if my calulator is wrong, or something is not correctly counted within Object Explorer. Taken from R80.20 Demo Mode. The same incorrect number is seen also in real mode.
According Object Explorer there are 8984 objects in total, but in fact if we count all objects in Categories, we will get 8195.
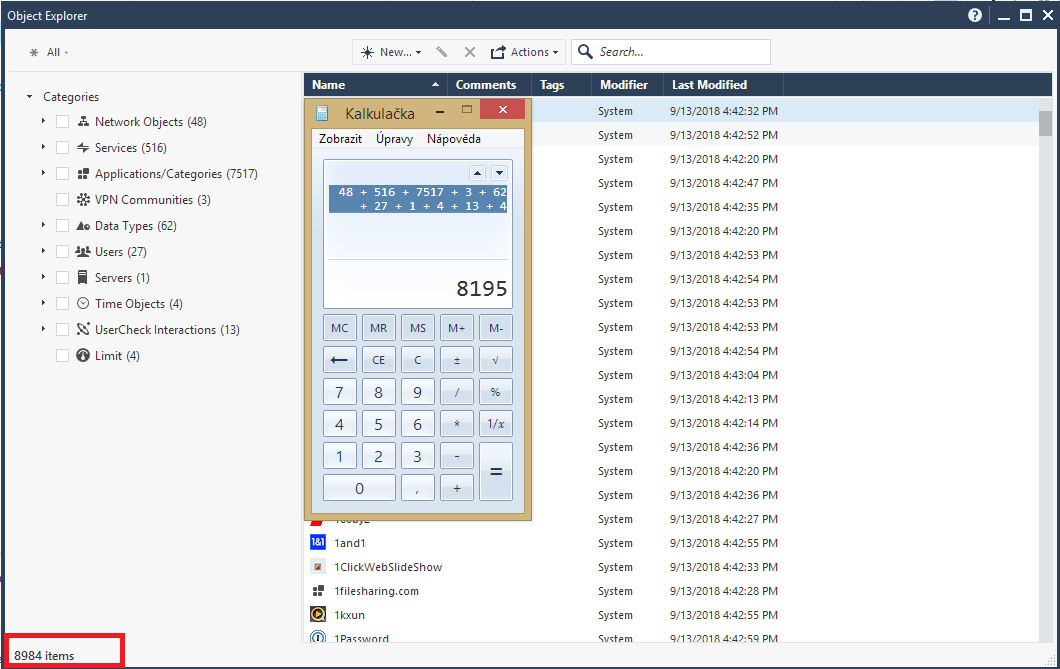
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Jozko Mrkvicka, we'll look into this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I did my AIO upgrade to R80.20 at the weekend - rolled back to day after some issues. Upgrade from R80.10 with JHF T141.
I am running a system with PPP interfaces and thus SecureXL is permenantly disabled. I discovered after the upgrade that SecureXL has changed in the way that it is configured, I no longer had an option in cpconfig to disable it and the "cp_conf sxl enable/disable" as per the guide wasn't a flag cp_conf recognised.
This left me in a predicament, as that is obviously our gateway out to the wider world. I found I could work around this by disabling the various parts of SecureXL manually, but still had sporadic traffic throughput issues and "fwaccel stat" still reported that "Throughput acceleration was enabled" even though all the features I could find to disabled, were so.
Has there been a change in R80.20 where SecureXL is now a required item and thus cannot be disabled?
I also noted that it was listing interfaces, so made some assumptions that SecureXL could be enabled and disabled on a per-interface basis which seems interesting, not too certain how that works with my historical understanding of traffic being forwarded between accelerated and non-accelerated interfaces.
Overall, other than this issue - which is just simply a deal killer for me I was pleased with the experience. The new console is smart (no pun intended) and it feels overall more polished. Still some issue swith scaling and the like in Windows 10 when viewing the topology, but minor niggles.
If someone could clarify the SecureXL situation in R80.20 that would be great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel, why don't you want to disable acceleration with fwaccell off command?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's fine for run-time but comes back on at boot. It also didn't resolve all of my SecureXL related issues.. as it said there was still acceleration features enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh, I see, you want to off-load SXL completely from the kernel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah like we used to through cpconfig. But that option seems to be missing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do also have problems with SecureXL. After disable SecureXL ( fwaccel off -a) all my connections problems gone (even UDP). But unfortunately they are activated after policy installation or reboot. I have to rollback to R80.10.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 15 | |
| 9 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


