- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Blocking Psiphon 3 R80.10
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Blocking Psiphon 3 R80.10
I'm trying to block Psiphon 3
I have blocked the single application, the category: anonymizers.
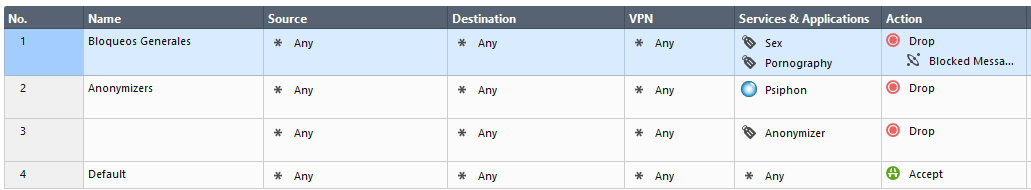
I have enabled the HTTPS Inspection for all the categories

The logs shows Psiphon is blocked but it's still working
Has anyone successfully blocked Psiphon 3 ???
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Psiphon, like many anonymizes, evolves specifically to avoid detection.
As a result, from time to time, the application signature needs to be updated.
I recommended engaging with the TAC and providing some packet captures so we can take a look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I really did block Psiphon3 with this configuration:
a) Enable HTTP Inspection in all categories
b) Block categories: Anonymizers, Unknown traffic
c) Block SSH in Firewall Layer (I had to allow ssh to my specific destinations)
The problem is: A few applications are not identified by Check Point, so they are blocked beacuse of the "unknown traffic" category drop
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ricardo,
Full HTTPS inspection and blocking SSH protocol is indeed crucial for successful blocking of the Psiphon client.
Did you try to enforcing it without blocking 'Unknown Traffic' and failed to do so?
As Dameon stated above you may contact us via TAC and send us captures of the specific unblocked traffic, in the meanwhile we'll work on trying to reproduce the issue in our lab as well.
In case you are interested in adding new detection for apps which are currently not detected ("Unknown Traffic") you may submit a request via the following form and request a new application:
Thanks,
Idan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Idan,
I did try without blocking "unknown traffic" category, but Psiphon is not blocked. So, in my case it was necessary.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still i have same problem. 1 year continue working with TAC. but they didnot solve my problem. Psiphon very fast getting new updates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are correct Psiphon is quickly getting new updates, therefore the best way is to find the culprit. alert when there is a multiple ssh connection from same source. Fortunately, I have SIEM to do that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also facing same issue, though i have blocked open SSH & unknown traffic also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally able to block the psiphon with the help of tac.
The procedure is :
-install the latest hotfix in both gateway and management (may or may not be required)
- Enable https inspection and generate the self sign certificate.
- generate self-signed certificate and install it on all PC of the network (Would be easy if Active Directory is in use)
- Make a Policy for https inspection with "https" and "http_and_https_proxy" with ACtion=Inspection
- Add url and application policy to block the category "support file sharing".
Note: the psiphon is block for only devices in which we install the self-sign certificate.
Thanks,
Sagar Manandhar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does not work without HTTPS Inspection?? What happens on BYOD scenarios??
I have a customer with a WiFi deployment for Students where each one has his own tablet to access shared resources and for Internet Access, according to policy all Media Sharing and Media Streams are blocked, but still bypassed with Psiphon because I can't deploy a certificate for those devices.
Any ideas of a workaround?
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like I said previously:
Psiphon, like many anonymizes, evolves specifically to avoid detection.
As a result, from time to time, the application signature needs to be updated.
I recommended engaging with the TAC and providing some packet captures so we can take a look.
Contact Support | Check Point Software
Others have suggested (earlier on the thread):
- Blocking outbound SSH traffic to unknown servers
- Blocking Unknown Traffic
- Not allowing traffic on "all" ports, but specific ones
Obviously HTTPS Inspection is not always possible but is also effective as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Want to provide some update on this as the latest version of Psiphon has been updated to support QUIC.
In order to effectively block Psiphon, the following is needed:
- Block Psiphon
- Block Quic Protocol
- Block SSH Protocol (using the service in R80.10 or the application in R77.X)
- Block Unknown Traffic
- Full https inspection on the client machine without exceptions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But if we block QUIC protocol, will it impact any google services traffic i.e. google search, google mail, YouTube etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have not encountered any Google Service that also isn't available over traditional HTTP/HTTPS.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 18 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


