- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Application Control POC
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Application Control POC
Greetings Esteemed Members.
I am in the planning stages of a POC for inserting Open Server R80.10 gateway with R80.20 management virtual machines into a customer network.
The objective is to replace their current URL filtering solution with Check Point's SSL Inspection, Application Control and URL blades in the initial phase.
The customer's perimeter firewall is a Cisco ASA cluster and currently terminates VPN tunnels.
I was wondering whether the gateway can be inserted into the routing path using a single interface only, meaning that their layer 3 switch uses it as its default gateway and the Check Point's default gateway will be the ASA cluster, or do I need to physically place it between the internal network and the ASA cluster.
HTTP Proxy is not an option.
Thanks in advance for your support.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look for "Deploying a Security Gateway or a ClusterXL in Bridge Mode" in Installation and Upgrade Guide R80.20 and check limitations and notes before doing it.
From the table, it looks like you can achieve most of what you want with a single gateway in a bridge mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
Thanks for the link, in fact it is something that I looked at last night and I'm considering it.
It will also be the least intrusive topology option for the POC.
Only concern is this note #3
Identity Awareness in Bridge Mode supports only the AD Query authentication
I take it that it means Identity Collector isn't supported?
Do you know?
Cheers,
Calvin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not certain. Can someone from Check Point chime in please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep would really like to have Check Point clarify Identity Collector compatibility w/ gateway bridge mode
I don't see any reason why it won't work though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could another solution be to employ two vlans on your single interface? You should be able to route through with that configuration...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jason,
This thought did cross my mind and it's an excellent idea.
Thanks for pointing it out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok so after careful consideration and discussions w/ the client, it would be best to use bridge mode since the POC requires that no routing changes to the current network are to be made at this time.
The only risk in my mind then is that the server identified for the POC does not have bypass NICs in case of hardware failure or having to reboot for whatever reason.
Appreciate everyone's input thus far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could also use proxy mode, than you don't need to be inline, the working is abou the same for the actual policy.
Regarding the policy itself I have created a mgmt_cli script to create a shared APCL/URLF policy, which you can use ordered or as a inline internet filter.
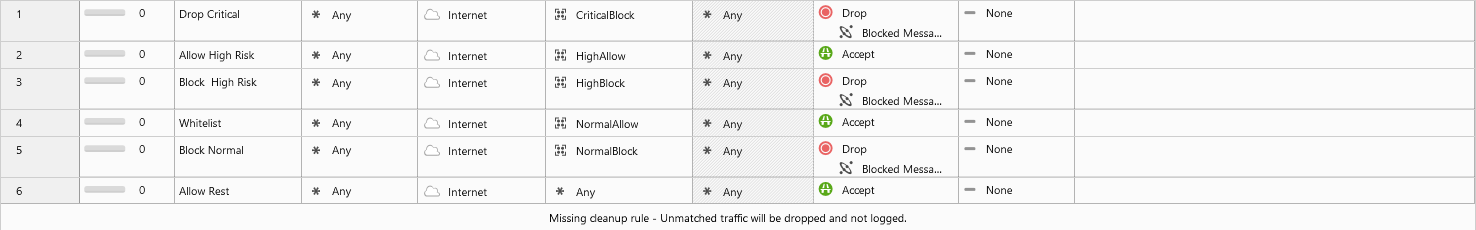
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Maarten - this is a good approach also, but the client does not want proxy mode.
How has your experience w/ this been in terms of performance, because as I understand it, proxy mode does not benefit from SecureXL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have 1 customer running it on a 13500 with around 4000 users and 700Mb of traffic running through it and it is humming just fine. I see it is running around 50/50 FW/PXL and they are not using HTTPS decryption.
I also need to tell you that all Guest network connections run inline, not using the proxy, I do not know the number of users on guest.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok good info.
This POC will run as a Hyper-V VM as follows:
Management - 8GB RAM, 4 vCPU, 100GB disk, 1Gbps vNIC
Gateway - 4GB RAM, 4 vCPU, 100GB disk, 1Gbps vNIC
1000 corporate users, no guests
SSL Inspection required
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can hit it with 8 cores, the all-in-one Eval is supporting 8 cores...
Normally we calculate with a multiplier of 1,6 for ssl inspection.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you explain the multiplier?
What value is multiplied by 1.6?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you ever looked at the CP Sizing tool? There the outcome for a appliance will be a certain load lets say 60% with the parameters that you have set, which means that with SSL inspection, you need to mylitply the 60% with 1.6 = 96% load on the appliance.
So far this has been pretty accurate.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have used the sizing tool but always wondered about the SSL. So my configs were always analyzed by the SSL team. But it's good to know about the 1.6 multiplier.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 28 | |
| 16 | |
| 10 | |
| 10 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


