- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Anti-Bot looking at inbound traffic on externa...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anti-Bot looking at inbound traffic on external interface?
I am under the impression that the Anti-Bot blade looks at traffic leaving internal networks in an attempt to find internal hosts that have already been compromised and the internal network is defined by the settings for interfaces in the topology, "Leads to: Internet (External) , internal, etc.
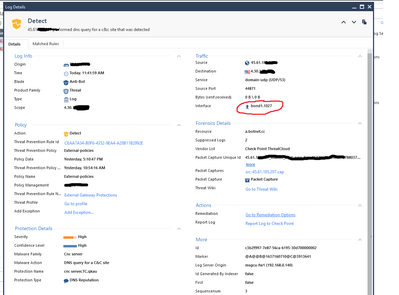
I recently enabled ABOT and am surprised to see log cards for udp/53 DNS query for a C&C site requests being detected by ABOT coming in on a external interface as shown in the screen shot.
The interface bond1.1027 is indeed set to "External"
The only thing I can think of to explain this is that my public IP in the log card is used as a static NAT in a host object for a host that lives off of a "Internal" interface.
Is that why Anti-Bot picked this up?
The internal host that 4.3.x.x NAT's to does indeed accept and service DNS requests from the internet.
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In R81 and above, I believe it also looks at stuff coming in from external as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I should have specified.... I am running 80.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm pretty sure the up arrow next to the bond interface in the log card indicates the packet was detected by AB leaving that interface outbound, not coming into it. So if that interface is declared External that would indeed be considered outbound traffic and fall under the purview of Anti-Bot.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
I see what you mean about the up arrow and that makes sense. What still doesn't make sense to me is my hosts IP is the 4.30.x.x. If this is outbound traffic shouldn't the 4.30.x.x IP show as the source?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
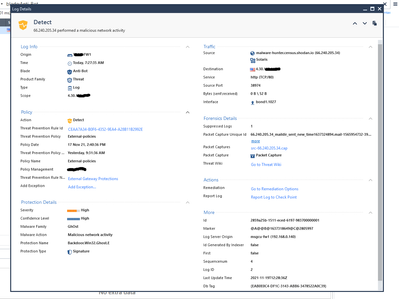
I had a similar scenario this morning this time for a Backdoor.Win32.Ghost.E ABOT protection. Per the log card the source is external and the destination is my organizations public IP 4.30.x.x which of course is on a external interface.
Basically from the source and destination in the log card this looks like external traffic coming into my organization.
This time I was able to download a pcap from the Forensic Details:
It appears there was a NAT translation as the 172.19.x.x IP is a host object of mine that has a static NAT in it for the 4.30.x.x IP.
Is the "offending packet" the first one listed in the PCAP that caused the ABOT log? If it is this shows the traffic did indeed originate from the public internet and came into a external interface.
With that being said the PCAP does show my 172.19.x.x IP replying to the alleged malicious host so is packet # 2 the offending packet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think this strangeness you are seeing may be caused by how different applications behave. Some are "client talks first" and some are "server talks first". An example of "server talks first" is FTP, once the TCP 3-way handshake is complete the server presents a 220 banner first then the client replies with USER. An example of "client talks first" is HTTP, where after the TCP 3-way handshake is complete the client issues an HTTP verb to the server and the server responds. Perhaps this detection happened in a "server talks first" scenario where your client initiated the connection, but there wasn't any data to make the detection until the server talked back first inbound.
A little-known fact covered in my 2021 IPS/AV/ABOT Video Series is that if the TP action is Detect and "Packet Capture" is set (as in your case), you can get up to 100KB of packets in the capture if the connection continues, whereas you will normally only get one offending packet if the action is Prevent. This behavior when Detect is set gives additional context, but can make figuring out the offending packet a bit tougher. See here for more reading: sk148492: Packet capture for IPS logs with "Prevent" or "Detect" actions does not show the desired n...
Given what I've stated above, does what you are seeing in the packet capture make more sense now?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
Yes, that makes sense with the FTP server talk first example. What about DNS queries? From what I understand that is a "client talk first", right?
I replicated this scenario in my lab and ABOT performs the same way. If I make a DNS query to a known malicious site to a DNS server that sits behind my lab gateways Check Point's ABOT "prevents" it. In my lab I changed ABOT from detect to prevent and I do see the difference in fewer packets captured. In this DNS query example I now only see 1 packet which must be the offending packet. The pcap shows the offending packet with a source IP of the host "outside/external" to my gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DNS is indeed a client talks first protocol and detection can happen on the very first packet because there is no handshaking with UDP, and it sounds like you are seeing what you should in regards to how many packets are captured with Detect vs. Prevent.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why would a inbound DNS request on a external interface be looked at by Anti Bot?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Timothy_Hall Does AB ever inspect inbound DNS traffic? I think I see what Mike is talking about as the source/destination IP addresses make it seem like this is external --> internal traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If an internal client makes a DNS lookup request for a site name and the outbound DNS request does not run afoul of Domain Reputation, the IP provided in the inbound DNS response would then need to be checked by Anti-bot for IP reputation. Or perhaps Anti-bot waits until the actual outbound connection request to the resolved IP, and then applies the IP Reputation check at that point? This latter scenario is heavily implied in the "Reputation Layer" section of the ATRG for AV/ABOT, but I'm not 100% sure about this and we'll probably need someone in R&D to comment. Tagging @PhoneBoy
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would make sense that'd we catch the DNS reply before we make the actual IP connection.
Maybe @TP_Master or someone on the team knows for sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Damon, it's not the reply Check Point is catching. My system actually never sends a reply. It is the initial DNS query inbound that Check Point is catching.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then...you have your answer 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I eventually opened a TAC case for this to investigate the ABOT traffic flow. In summary per TAC ABOT doesn't care about what interfaces are set as internal or external and all that matters is the Threat Prevention Rule Base. If I want to have ABOT look at traffic leaving my internal networks only I would have to configure the Threat Prevention Rule Base accordingly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting, thanks for the follow-up.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter