- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Route specific subnet out second ISP interface
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Route specific subnet out second ISP interface
Hi,
Need some assistance setting up policy based routing or a static route. Basically just looking to route traffic from one VLAN out a secondary ISP link. Reading through the Policy based routing article SK100500 this does not give me the scenario. There is no way to specific "internet" as a destination.
Source: 192.168.178.x - Destination: Internet - Gateway - ISP 2 (eth1)
See my mspaint diagram below. Can anyone advise how i would route this traffic our my second ISP link?
Any advice/assistance would be great!
Cheers,
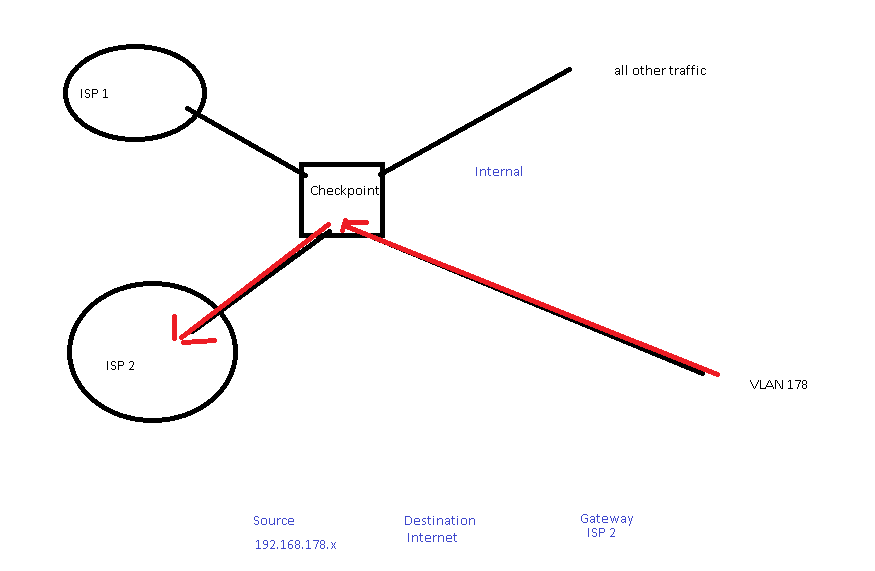
Called checkpoint support, they didnt really understand what i meant, even after i drew them a basic diagram in paint.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mike,
PBR is based on IP and Ports, there is no Internet Object as on regular policy.
To route VLAN178 through ISP2 and assuming ISP1 is configured as your default route, yo have to do the following:
1. Create a new PBR table of type Default Route that points to ISP2 next hop address.
2. Add a new PBR rule with source Inbound Interface of VLAN178 (I'm assuming is locally conected on a subinterface ethx.178) who uses the PBR table created earlier. On this case, you can't solely use the segment 192.168.178.X/XX since the Firewall probably has an IP address on this segment and could derive on unwanted behavior.
Please note the following:
- Hide behind Gateway NAT or Hide Behind IP (on ISP2 range) must be configured for VLAN178's Network Object to allow traffic leave the ISP2 interface with correct IP address. If you use Hide behind IP, Proxy ARP may be neccesary
- Since PBR is processed before regular Routing Table, if you follow the two steps mentioned above, all traffic from VLAN178 will be redirected to ISP2 link no matter which is the final destination. If you want to route to local networks, you will have to create a new PBR table including those you need to reach locally and specify the output interface (like a copy of your routing table); after that you need to create a PBR rule with lower priority pointing to this table.
- There is no automatic failover, so if ISP2 is down on some place along the path; all traffic still be sent to this link.
- If you have ISP Redundancy configured, PBR is bypassed.
Regards.
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mike,
PBR is based on IP and Ports, there is no Internet Object as on regular policy.
To route VLAN178 through ISP2 and assuming ISP1 is configured as your default route, yo have to do the following:
1. Create a new PBR table of type Default Route that points to ISP2 next hop address.
2. Add a new PBR rule with source Inbound Interface of VLAN178 (I'm assuming is locally conected on a subinterface ethx.178) who uses the PBR table created earlier. On this case, you can't solely use the segment 192.168.178.X/XX since the Firewall probably has an IP address on this segment and could derive on unwanted behavior.
Please note the following:
- Hide behind Gateway NAT or Hide Behind IP (on ISP2 range) must be configured for VLAN178's Network Object to allow traffic leave the ISP2 interface with correct IP address. If you use Hide behind IP, Proxy ARP may be neccesary
- Since PBR is processed before regular Routing Table, if you follow the two steps mentioned above, all traffic from VLAN178 will be redirected to ISP2 link no matter which is the final destination. If you want to route to local networks, you will have to create a new PBR table including those you need to reach locally and specify the output interface (like a copy of your routing table); after that you need to create a PBR rule with lower priority pointing to this table.
- There is no automatic failover, so if ISP2 is down on some place along the path; all traffic still be sent to this link.
- If you have ISP Redundancy configured, PBR is bypassed.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow! , thanks for the detailed response. Didn't expect that!
Will be giving this a shot today. Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just reporting back that this worked perfectly. not sure why checkpoint support couldn't have pointed me in this direction. Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's great to know that, Mike!
We're here to help.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, sorry for the late answer, I wasnt available on the community for a while.
When you're using default route statement, all traffic goes through that interface. So is neccesary to add each directly connected network entry to a PBR Rule/Table before the default route entry.
If I remember correctly, without the additional network entries, you're able to reach all firewall interfaces on any net (as long you have firewall permissions) but not beyond that.
Regards.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 9 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


