- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Workspace
- :
- Endpoint
- :
- Re: Unable to install E82.00 on macOS 10.15.1 (Gat...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Unable to install E82.00 on macOS 10.15.1 (Gatekeeper)
Having issues because the app is not verified or authorized by macOS Gatekeeper to install. Is this a known issue or are there recommended workarounds?
How to reproduce:
- Download the package from the following: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Opened up the DMG: Endpoint_Security_VPN.dmg
- Clicked the package installation.
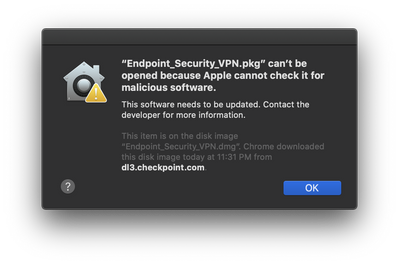
Prompted to with the following error:
“Endpoint_Security_VPN.pkg” can’t be opened because Apple cannot check it for malicious software.
This software needs to be updated. Contact the developer for more information.
This item is on the disk image “Endpoint_Security_VPN.dmg”. Chrome downloaded this disk image today at 11:31 PM from dl3.checkpoint.com.
About my Mac:
- Model Name: MacBook Pro
- Model Identifier: MacBookPro13,2
- Processor Name: Dual-Core Intel Core i7
- System Version: macOS 10.15.1 (19B88)
- Kernel Version: Darwin 19.0.0
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you search for a remedy Apple gives you https://support.apple.com/en-us/HT202491
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you search for a remedy Apple gives you https://support.apple.com/en-us/HT202491
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
This is correct. Limited Availability version is not yet notarized by Apple. Check Point works on this and GA version has already passed all required procedures. We don't have exact release date yet as we are still running final quality assurance cycle. Keep watching SK for updates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have exactly the same problem. Is it solved? I have a mac version Catalina 10.15.2, and the endpoint vpn does not run (although it says that it supports version 10.15 and catalina). It gives me the same error message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is still not resolved as of 8-18-2020. Running macOS 10.15.6 and with the latest version of CP Endpoint Security (E83.20). The last I heard from support was that it would not be resolved until the end of this calendar year.
Support for Apple Mac is a very low priority for Check Point as you can tell from the fact that the VPN client just now got support for Multiple Authentication Factors, 3+ years after that feature was mainstream for Windows platforms. What I don't get is why Check Point can't spend the $99 for an Apple Developer Account and take the extra 3 steps to notarize the PKG file in the build process. It literally took me 30 minutes the other day to find a nice write-up someone did online on signing a PKG file using the command line tools and to sign and notarize the PKG for installation.
It may be possible to re-sign the PKG file if you happen to have your own Apple Developer Account (and Developer ID Installer certificate) and then submit that to Apple for notarization. This may be the only way for users that are using a UEM/MDM platform to manage their Mac computers as there is no other way to automate the Gatekeeper approval otherwise.
The PKG is already signed, they just either didn't notarize it or didn't stable the notarization to the PKG:
heath@Heaths-MBP ~ % pkgutil --check-signature ./Endpoint_Security_VPN.pkg
Package "Endpoint_Security_VPN.pkg":
Status: signed by a developer certificate issued by Apple for distribution
Signed with a trusted timestamp on: 2020-08-03 17:17:39 +0000
Certificate Chain:
1. Developer ID Installer: Check Point Software Technologies (TZ3UEPFYKD)
Expires: 2022-02-08 14:55:35 +0000
SHA256 Fingerprint:
F9 2B BE 97 52 FE 57 7A F6 A3 8C CE 22 72 58 0C F8 DA BA 05 B2 5A
B8 50 D2 9D BC EB CB 37 BC 31
------------------------------------------------------------------------
2. Developer ID Certification Authority
Expires: 2027-02-01 22:12:15 +0000
SHA256 Fingerprint:
7A FC 9D 01 A6 2F 03 A2 DE 96 37 93 6D 4A FE 68 09 0D 2D E1 8D 03
F2 9C 88 CF B0 B1 BA 63 58 7F
------------------------------------------------------------------------
3. Apple Root CA
Expires: 2035-02-09 21:40:36 +0000
SHA256 Fingerprint:
B0 B1 73 0E CB C7 FF 45 05 14 2C 49 F1 29 5E 6E DA 6B CA ED 7E 2C
68 C5 BE 91 B5 A1 10 01 F0 24
heath@Heaths-MBP ~ % stapler validate --verbose Endpoint_Security_VPN.pkg
Processing: /Users/heath/Endpoint_Security_VPN.pkg
Properties are {
NSURLIsDirectoryKey = 0;
NSURLIsPackageKey = 0;
NSURLIsSymbolicLinkKey = 0;
NSURLLocalizedTypeDescriptionKey = "Installer package";
NSURLTypeIdentifierKey = "com.apple.installer-package-archive";
"_NSURLIsApplicationKey" = 0;
}
Sig Type is RSA. Length is 3
Sig Type is CMS. Length is 3
Package Endpoint_Security_VPN.pkg uses a checksum of size 20
We do not know how to deal with trailer version 29928. Exepected 1
Endpoint_Security_VPN.pkg does not have a ticket stapled to it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with getting this long time issue resolved. It has been an issue way to long. Details matter in this case and it seems to be sloppiness from a development teams standpoint. I agree that Apple has a work around as listed in the article https://support.apple.com/en-us/HT202491/ But the simple matter of fact is that other companies that develop Apple applications have figured this out. Why can't CP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To make it even worse, it is only 3 commands added to the auto-build script that I'm sure is in use to submit the package for notarization, check on the status of notarization and then to staple the notarization to the package so that it can be installed offline on the system. Including the time it takes Apple to actually do the notarization, it may be about 30 minutes to the process.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter