In a TE log you can find additional important information how a file was processed:
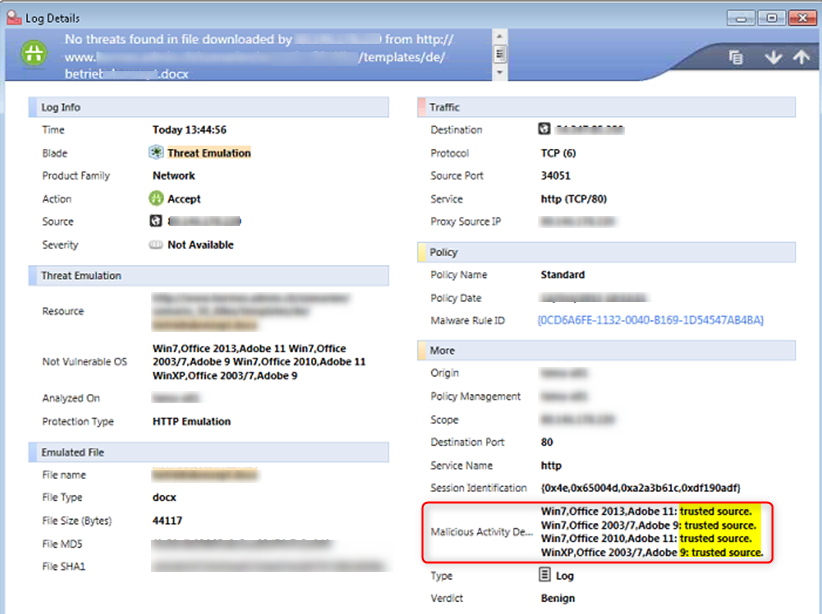
In the example above "trusted source" means that this file was bypassed by the global whitelist hence it was not emulated.
Different values explained:
| Value | Comment |
|---|
| trusted source | file bypassed emulation due to Check Point maintained and automatically updated TE whitelist |
| emulator | file was locally emulated on a SandBlast Appliance |
| cloud emulation | file was sent to cloud emulation |
| remote emulation | file was sent to a remote SandBlast Appliance for emulation (this log is usually issued by a gateway connected to a SandBlast appliance) |
| static analysis | file was pre-filtered by static analysis and was not emulated |
| local cache | file´s SHA1 was already found in cache (# tecli cache dump all) and was not emulated; action is based on the cached verdict |
| archive | handled file was an archive |
| logger | You get "logger" for a "malicious" file as verdict decider when the file was not successfully emulated but other advisories already convitced the file as malicious |
| file | When trying to emulate the file the actual file size was 0 |
In depth info of e.g. static analyis, cache handling etc can be found in the amazing ATRG: Threat Emulation SK:
ATRG: Threat Emulation
With this knowledge you can easily query all files that e.g. were really sent to cloud for emulation:
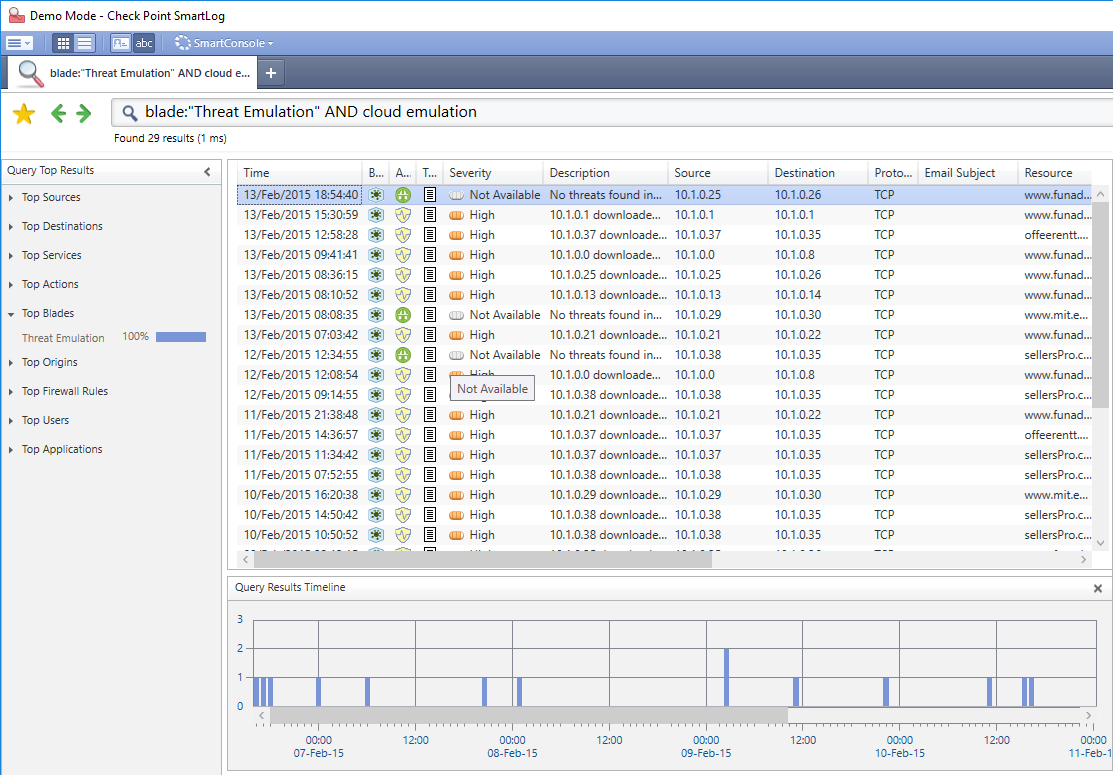
With SmartLogs Timeline results you can even quickly check how file amount was handled over a certain timeframe.
This is also helpful for investigating performance/throuput issues.




