- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Understanding Threat Emulation logs
In a TE log you can find additional important information how a file was processed:
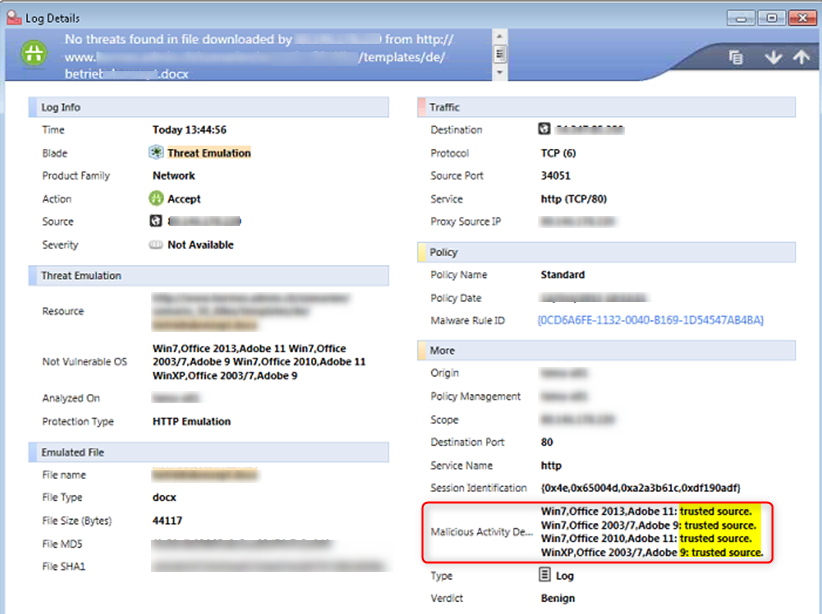
In the example above "trusted source" means that this file was bypassed by the global whitelist hence it was not emulated.
Different values explained:
| Value | Comment |
|---|---|
| trusted source | file bypassed emulation due to Check Point maintained and automatically updated TE whitelist |
| emulator | file was locally emulated on a SandBlast Appliance |
| cloud emulation | file was sent to cloud emulation |
| remote emulation | file was sent to a remote SandBlast Appliance for emulation (this log is usually issued by a gateway connected to a SandBlast appliance) |
| static analysis | file was pre-filtered by static analysis and was not emulated |
| local cache | file´s SHA1 was already found in cache (# tecli cache dump all) and was not emulated; action is based on the cached verdict |
| archive | handled file was an archive |
| logger | You get "logger" for a "malicious" file as verdict decider when the file was not successfully emulated but other advisories already convitced the file as malicious |
| file | When trying to emulate the file the actual file size was 0 |
In depth info of e.g. static analyis, cache handling etc can be found in the amazing ATRG: Threat Emulation SK:
With this knowledge you can easily query all files that e.g. were really sent to cloud for emulation:
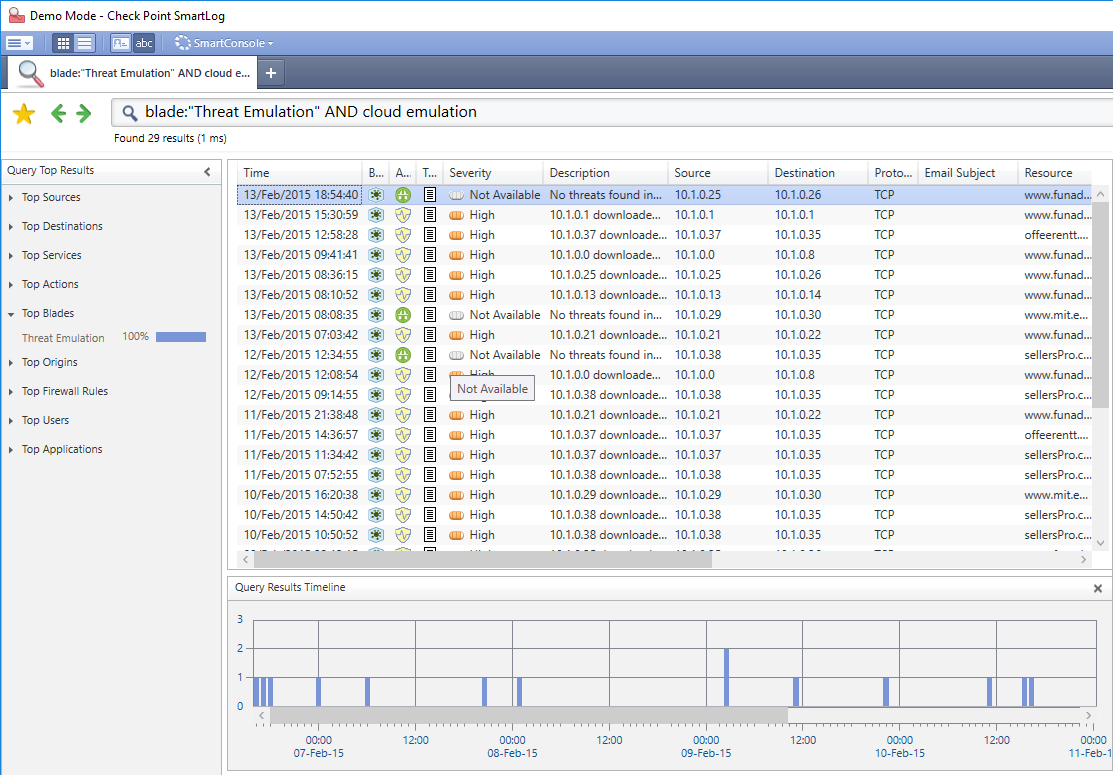
With SmartLogs Timeline results you can even quickly check how file amount was handled over a certain timeframe.
This is also helpful for investigating performance/throuput issues.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


