- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Quantum Spark Management Unleashed!
Introducing Check Point Quantum Spark 2500:
Smarter Security, Faster Connectivity, and Simpler MSP Management!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- IPS issue (R80.20) - cannot remove IPS blade from ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPS issue (R80.20) - cannot remove IPS blade from GW object
hi chaps
got an interesting one
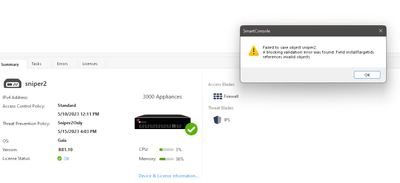
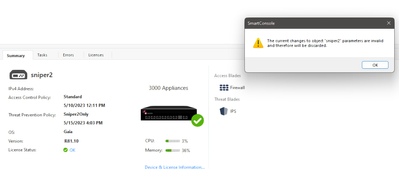
1. object of the GW has IPS enabled, when trying to untick and disable it I cannot seem to save the changes as SmartConsole shout on me as following:
a. "Failed to save object "xxx". A blocking validation error was found: Field InstallTargetIds references invalid object
b. "The current changes to object "xxx" parameters are invalid and therefore will be discarded"
and that's all. when "a" occur the only way to move on is to click OK, when done "b" appears.
any idea what and why? literally nothnig has changed on that "StandAlone" Appliance since original install of R80.20.
ps. cpinfo -y all below (also see enclosed 1.png)
[Expert@xxx:0]# cpinfo -y all
This is Check Point CPinfo Build 914000190 for GAIA
[IDA]
No hotfixes..
[CPFC]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[MGMT]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[FW1]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
FW1 build number:
This is Check Point Security Management Server R80.20 - Build 007
This is Check Point's software version R80.20 - Build 047
kernel: R80.20 - Build 047
[SecurePlatform]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[CPinfo]
No hotfixes..
[DIAG]
No hotfixes..
[PPACK]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[CVPN]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[SmartLog]
No hotfixes..
[Reporting Module]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[CPuepm]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[VSEC]
HOTFIX_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[R7520CMP]
No hotfixes..
[R7540CMP]
No hotfixes..
[R76CMP]
No hotfixes..
[SFWR77CMP]
No hotfixes..
[R77CMP]
HOTFIX_R80_20_JHF_COMP Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC
[R75CMP]
No hotfixes..
[NGXCMP]
No hotfixes..
[EdgeCmp]
No hotfixes..
[SFWCMP]
No hotfixes..
[FLICMP]
No hotfixes..
[SFWR75CMP]
No hotfixes..
[MGMTAPI]
No hotfixes..
[CPUpdates]
BUNDLE_CPINFO Take: 0
BUNDLE_R80.20_SC Take: 101
BUNDLE_R80_20_JUMBO_HF_MAIN Take: 47
BUNDLE_R80_20_JUMBO_HF_MAIN_SC Take: 73
Jerry
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right-click on the gateway object and select "Where Used". That should help you figure out where the reference to that object is that is blocking you. My guess is you are referencing that particular gateway for "Install On" in a custom Threat Prevention rule, IPS ThreatCloud exception or possibly even a Core Activations exception.
Geo Policy is not part of IPS starting in R80 (and this feature is now deprecated) but there still may be some remaining hooks to IPS here as I sometimes still notice references to IPS in the logs for Geo Policy drops.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats pretty much how it works for any blade, if blade is NOT active, rules will never apply.
Andy
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jerry,
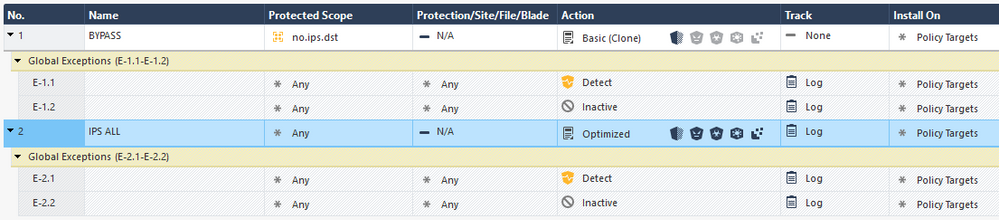
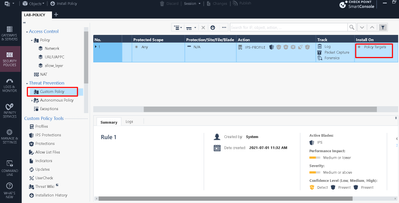
Please go over the Threat Prevention Policy rules [Security Policies > Threat Prevention > Each Threat Prevention Layer] and make sure the Security Gateway with the IPS blade is not directly selected as an Install On target.
If it is, try changing the Install On for each rule so that it is * Policy Targets and then try disabling the IPS blade.
HTH
Tal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
see below Tal. I have never had here any "targets" selected though I don't think this applies to my case.
Now the GW has IPS blade enabled, and after the complete reboot of the GW all seems just fine:
I have really no clue why I couldn't "deselect" blade on GW object and save it 1h ago.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jerry,
that's magic. Maybee some earth rays or other things in the air are affecting the SMS..
I love our IT job, normally it consist of 0 and 1 but sometimes something between 8)
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also having problems disabling IPS. Exactly the same situation as the original poster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I remember one time I had this problem ages ago, I changed something in Guidbedit to make it work, but it was more than 10 years ago, so definitely before R80 version. Can you send a screenshot?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
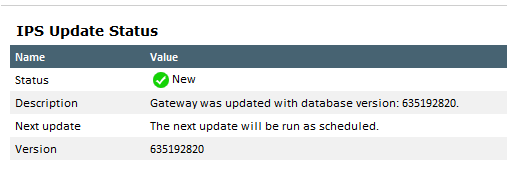
I found some posts where it says to remove scheduled ips updates (if enabled) and also remove from here, IF its enabled
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't have anything under Install On other than 'Policy Targets'. Nothing specific. I unchecked IPS updates and now the entire dialog for IPS updates is gone (edit: It seems it changed the focus from Threat Prevention to Updates which is why it disappeared. I had to click back on Threat Prevention>Updates to get back to where I was.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a Geo Policy defined but there is no way to tell it NOT to install on this device I am trying to remove IPS from without impacting the device I don't want to. I can 'view' the items under Gateways but you cannot manipulate them. So you cannot really say, hey don't push Geo Policy to X device, at least I don't know how you would do that. I believe Geo Policy is a part of IPS so that could be what is stopping it from being deactivated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the legacy GeoPolicy requires IPS.
See: https://support.checkpoint.com/results/sk/sk16921
From R80.20 and above, you can use Updatable Objects for various locations in your regular Access Policy.
This does not require IPS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think what @Timothy_Hall gave makes total sense. Follow those instructions and let us know what gives.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right-click on the gateway object and select "Where Used". That should help you figure out where the reference to that object is that is blocking you. My guess is you are referencing that particular gateway for "Install On" in a custom Threat Prevention rule, IPS ThreatCloud exception or possibly even a Core Activations exception.
Geo Policy is not part of IPS starting in R80 (and this feature is now deprecated) but there still may be some remaining hooks to IPS here as I sometimes still notice references to IPS in the logs for Geo Policy drops.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Under Objects there was IPS Scheduled Update. I had tried fussing with that earlier based on what Andy suggested,
so I went back and revisited it. I toggled it to 'install on specific' and 'back to Install' on all clicked okay.
Went back and tried to disable IPS and this time it worked. Yay team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good job @Tony_Graham 💪💪
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I have an unrelated, related question. If you push a policy that contains IPS, for instance you shotgun out a policy to all gateways, does CP know that since the blade isn't running on that device to just drop the rules or does it get the whole policy but just ignores the bits it cannot enforce. Is there a benefit to pushing different policies since the ruleset would be less complicated?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats pretty much how it works for any blade, if blade is NOT active, rules will never apply.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assumed that but...you know about assumptions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yea, I do know...heard that from a woman long time ago...a**...U...me 🤣🤣
Anyway, will go play some chess now, maybe beat FAKE Magnus Carlsen...aka Chat GPT chess player, where it teleports the queen from nowhere into 3rd dimension and bishop reappears from ancient times to save the game lol
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jerry,
we had the same problem last month.
As Tal_Paz-Fridman wrote, we removed the directly assigned gateway from the install target column adn now you can uncheck IPS from gateway properties.
Please too check your IPS exceptions, maybee there is too an direct assignment of the gateway.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Conclusion: Don't disable the IPS blade.
Why would you even want to do that? 🙂
Why would you even want to do that? 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
neva! 😛
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I needed to disable IPS according to sk163752
I did not have a target in the Install On column of the Threat Prevention policy.
For me, the issue was that the gateway was selected under automatic install after IPS update.
I had to remove the gateway, install database and only then i could uncheck the IPS blade.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 |
Upcoming Events
Wed 10 Sep 2025 @ 11:00 AM (CEST)
Effortless Web Application & API Security with AI-Powered WAF, an intro to CloudGuard WAFWed 10 Sep 2025 @ 11:00 AM (EDT)
Quantum Spark Management Unleashed: Hands-On TechTalk for MSPs Managing SMB NetworksFri 12 Sep 2025 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 38: Harmony Email & CollaborationWed 10 Sep 2025 @ 11:00 AM (EDT)
Quantum Spark Management Unleashed: Hands-On TechTalk for MSPs Managing SMB NetworksFri 12 Sep 2025 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 38: Harmony Email & CollaborationAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter