Currently doing a Juniper SRX migration and looked at doing a conversion using smartmove.
Some somewhat formatted information below. The results are pretty good so far; there is definitely data I can use (object creation and so on). Most of that fairly easy to script from the raw configuration files anyway.
This is a good start for smartmove, but it's not exactly perfect (and I probably wouldn't rely on it). I'll keep commenting as I get on.
First pass (including NAT checkbox) fails with:
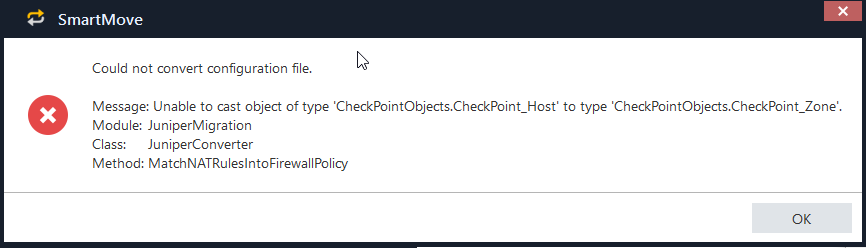
Unselected "Convert NAT configuration" and conversion succeeds. NAT's will need to be conducted manually.
// quick and dirty review below
Scripts generated are two-fold (objects.sh and policy.sh).
Objects.sh does a whole lot of the below with the address-book:
echo 'create host [xxxxxxx] with ip-address [1.2.3.4]'
cmd='mgmt_cli add host name "xxxxxxx" ip-address "1.2.3.4" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
echo 'create network [1.2.3.0_24]: subnet [1.2.3.0] mask [255.255.255.0]'
cmd='mgmt_cli add network name "1.2.3.0_24" subnet "1.2.3.0" subnet-mask "255.255.255.0" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
Does in fact create zone objects 
echo 'Create Zone Objects (x6) '
echo 'create zone [Trust]'
cmd='mgmt_cli add security-zone name "Trust" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo 'create zone [Untrust]'
cmd='mgmt_cli add security-zone name "Untrust" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
Create's a bunch of duplicate services:
echo 'create tcp service [junos-ftp-data]: port [20]'
cmd='mgmt_cli add service-tcp name "junos-ftp-data" port "20" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
echo 'Create DCE-RPC Service Objects (x21) '
echo 'create dce-rpc service [junos-ms-rpc-epm]: interface-uuid [e1af8308-5d1f-11c9-91a4-08002b14a0fa]'
cmd='mgmt_cli add service-dce-rpc name "junos-ms-rpc-epm" interface-uuid "e1af8308-5d1f-11c9-91a4-08002b14a0fa" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
Policy conversion creates a large bunch of sub-policies #drop rules etc.
echo 'Layers: Creating 20 sub-policies'
echo 'create layer [Trust_to_Untrust_sub_policy]'
cmd='mgmt_cli add access-layer name "Trust_to_Untrust_sub_policy" add-default-rule "false" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo 'Add rules to layer Trust_to_Untrust_sub_policy'
cmd='mgmt_cli add access-rule layer "Trust_to_Untrust_sub_policy" action "drop" track-settings.type "Log" position "top" name "Default action rule" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command
echo -n $'\rrule 1/41 '
cmd='mgmt_cli add access-rule layer "Trust_to_Untrust_sub_policy" source "any" destination "any" service "any" action "drop" track-settings.type "Log" position "top" name "default-deny" ignore-warnings true -s id.txt --user-agent mgmt_cli_smartmove'
run_command



