

Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest

***Last update - 24/12/20 - updated after a threat encountered at CloudGuard NDR. (Kudus @Nir_Naaman)
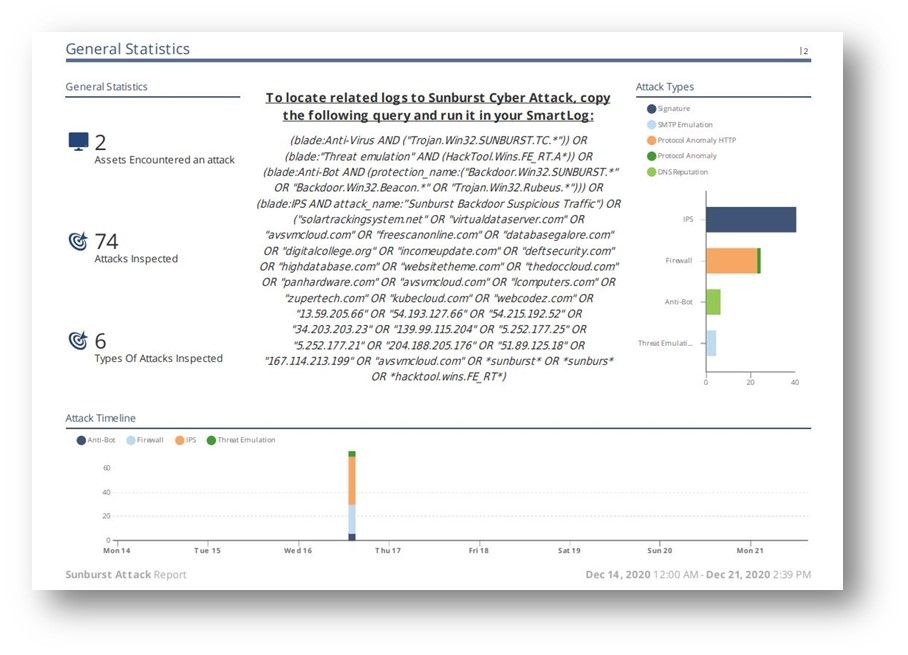
In December 2020, a large-scale cyberattack targeting many organizations – predominantly tech companies, mainly in the United States, but not only there – was discovered to have been going on for several months. The attack was of a degree of sophistication that led to a quick consensus of involvement by a foreign government, and was extraordinary in both the amount of care taken in crafting it and the exotic vector of entry; instead of the usual phishing or even exploitation, the attackers carried out an elaborate supply chain attack.
in this report you will be able to see results related to the attack if you have been affected.
More materials:
https://research.checkpoint.com/2020/sunburst-teardrop-and-the-netsec-new-normal/
https://blog.checkpoint.com/2020/12/16/solarwinds-sunburst-attack-what-do-you-need-to-know/
-------------------------------------------------------------------------------------------------
How to use the report:
extract the file Sunburst_attack.cpr file to your desktop
import the report to SmartView application (SmartConsole or Web)
go to Report TAB
double click on the report and define the time of query to start from 1.12.20
-------------------------------------------------------------------------------------------------
in parallel, run the following query in your smartlog:
"solartrackingsystem.net" OR "virtualdataserver.com" OR "avsvmcloud.com" OR "freescanonline.com" OR "databasegalore.com" OR "digitalcollege.org" OR "incomeupdate.com" OR "deftsecurity.com" OR "highdatabase.com" OR "websitetheme.com" OR "thedoccloud.com" OR "panhardware.com" OR "avsvmcloud.com" OR "lcomputers.com" OR "zupertech.com" OR "kubecloud.com" OR "webcodez.com" OR "13.59.205.66" OR "54.193.127.66" OR "54.215.192.52" OR "34.203.203.23" OR "139.99.115.204" OR "5.252.177.25" OR "5.252.177.21" OR "204.188.205.176" OR "51.89.125.18" OR "167.114.213.199" OR "avsvmcloud.com" OR *sunburst* OR *sunburs*
when analyzing the logs, understand if the log was created from a research that was conducted by a SOC analyst in your network or the source of the activity is a host/server.
-------------------------------------------------------------------------------------------------
in case you have a log related to one of the indicators OR the report resolved insights, contact Check Point Incident Response Team.
emergency-response@checkpoint.com
+1-866-923-0907
-------------------------------------------------------------------------------------------------
for more information on "how to import" the report, use the following documentations:
https://sc1.checkpoint.com/documents/R80.10/WebAdminGuides/EN/CP_R80.10_LoggingAndMonitoring_AdminGu...
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
***Last update - 24/12/20 - updated after a threat encountered at CloudGuard NDR. (Kudus @Nir_Naaman)
In December 2020, a large-scale cyberattack targeting many organizations – predominantly tech companies, mainly in the United States, but not only there – was discovered to have been going on for several months. The attack was of a degree of sophistication that led to a quick consensus of involvement by a foreign government, and was extraordinary in both the amount of
...;


About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY