- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Using an application object breaks the automat...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
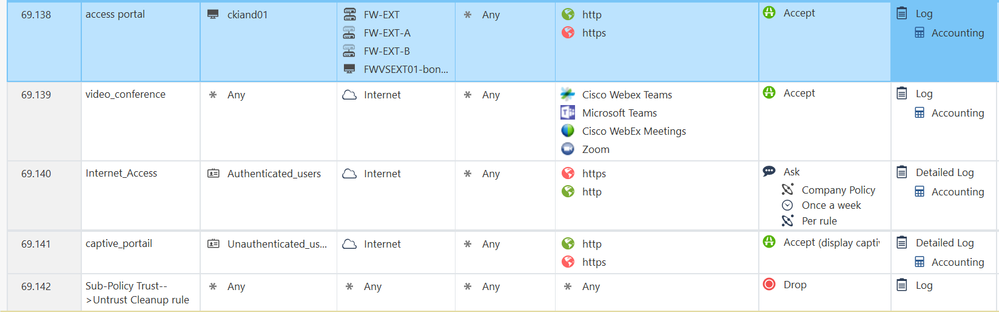
Using an application object breaks the automatic redirection to the captive portal
Hello,
I'm facing an issue with the firewall's captive portal
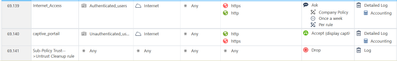
This is my rules
Everything works : unauthenticated users are automatically redirected to the captive portal when they try to surf on the Internet
But if I had a rule like this :
Webex / Teams / Zoom are working fine but the automatic redirection to the captive portal stop working and the user's packets are dropped by the rule 69.141...
The log of a dropped packet
Id: b161f674-b77b-d1ed-60ae-319e00000012
Marker: @A@@B@1622024052@C@1200369
Log Server Origin: 10.3.11.19
Time: 2021-05-26T11:31:43Z
Interface Direction: outbound
Interface Name: eth1-02.3
Connection Direction: Outgoing
Id Generated By Indexer: false
First: true
Sequencenum: 45
Service ID: https
Source: 10.30.3.200
Source Port: 50147
Destination: 172.217.168.228
Destination Port: 443
IP Protocol: 6
Xlate (NAT) Source IP: 212.166.62.52
Xlate (NAT) Source Port: 11288
Xlate (NAT) Destination Port:0
NAT Rule Number: 234
NAT Additional Rule Number: 0
Security Inzone: Trust
Security Outzone: Untrust
Context Num: 1
Action: Drop
Type: Connection
Policy Name: GHdC-Policy
Policy Management: SRVFWMGTND01
Db Tag: {B228AF78-7477-BD4F-9C40-CD6F2B61C40D}
Policy Date: 2021-05-26T09:51:51Z
Blade: Firewall
Origin: FW-EXT-B
Service: TCP/443
Product Family: Access
Logid: 0
Access Rule Name: Sub-Policy Trust-->Untrust Cleanup rule
Access Rule Number: 69.141
Policy Rule UID: 05a00e14-75ca-4b85-bb0a-6994640b919e
Layer Name: GHdC-Policy Trust_to_Untrust_sub_policy
Interface: eth1-02.3
Description: https Traffic Dropped from 10.30.3.200 to 172.217.168.228
Do you know why the redirection is not working anymore ?
Thanks !
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect the work that is happening to detect the various applications in rule 69.138 is causing it to bypass the Captive Portal.
Your Captive Portal rules do not require App Control to be invoked.
I suggest putting 69.138 after your Captive Portal rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunatly, I need to allow every users to access a set of specifics URL without asking for authentication (it's a business requirement...)
Maybe I'm wrong but I don't think I can move this rule :s
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are correct, you cannot move it up. However, You may want to add a rule for any to your FW above 69.139, to make sure the connectivity to captive portal works
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry, I don't understand your workaround. What can I add above 69.139 exactly ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to provide a way for users to open connection the the captive portal. As you are using an access role in 69.139, before the role itself is established, rule will not work. Either, use Any as a source (or internal networks, but not a user role), or add a rule allowing connectivity to the captive portal from any internal IP before that rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
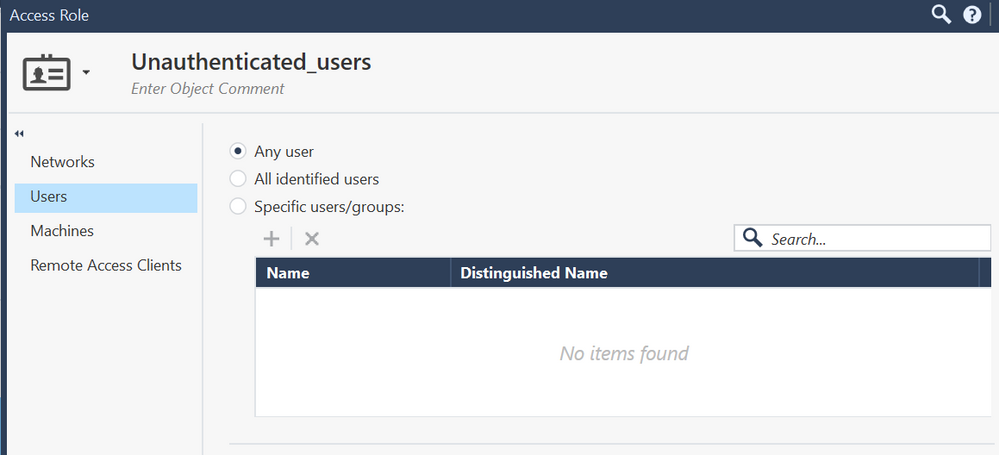
Also, show us how you define a user role for undefined users, please
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
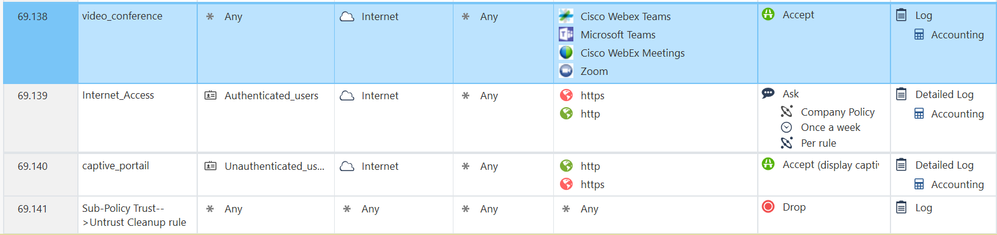
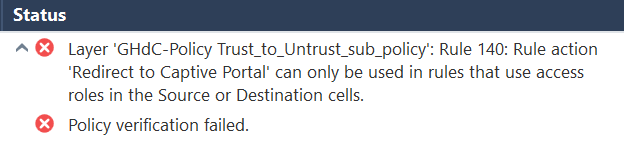
I changed the rules like this :
But I've the following error when I try to push the rules :
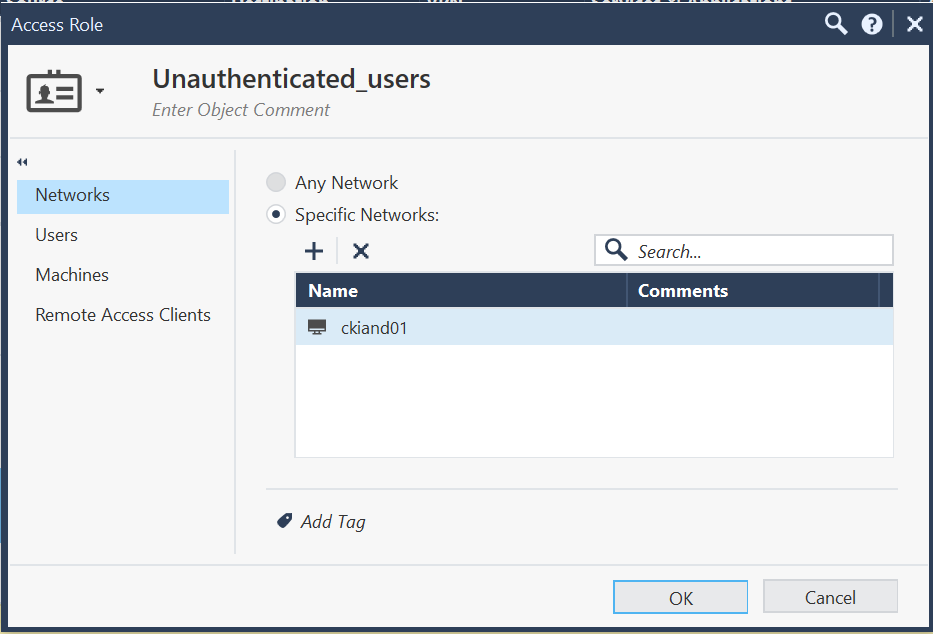
here is the content of the undefined users objet (ckiand01 is my test device)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, scratch "use any user" in the previous statement. You need to provide a rule that would allow connectivity from ckand01 to the portal, without auth. Put a rule allowing it access the portal on http and https, and try again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
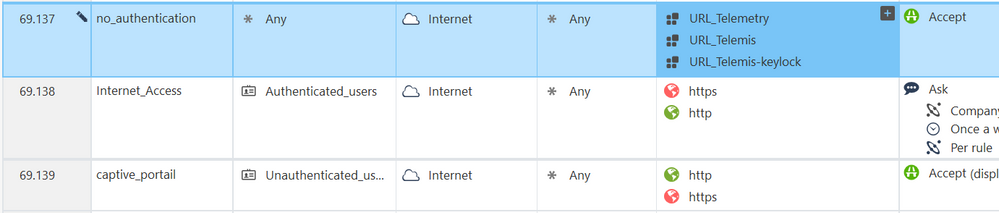
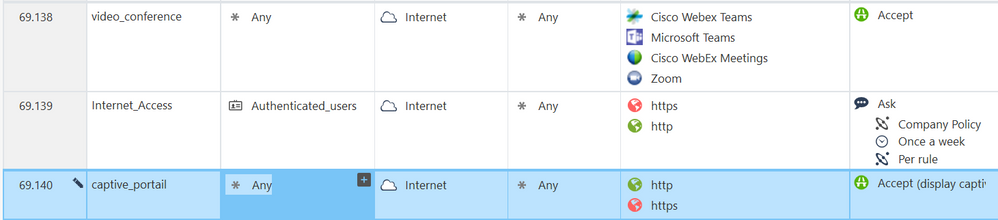
Like this ?
The automatic redirection is still not working 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you trying HTTPS or plain HTTP site?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https, everything is https today and I can't do https inspection if the user is not authenticated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, I see in the log above, you are using HTTPS. HTTPS Inspection should be enabled, if you need HTTPS connections to be redirected to the captive portal.
Also, there are some differences in behaviour, depending on the version you are using. You may want to look into sk121074 for more details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So
- If I don't use any application objet, the automatic redirection works, even if https inspection is disabled
- If I start using application objet, I need https inspection for the automatic redirection to work ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, https redirection should not work at all.
Which version of MGMT and GW are you using?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
80.40 JH 102
I don't know why but it works if I use the first set of rules (the first picture in my first post)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The following SK might explain why your original rules work: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
It's also why I suggested moving the rule with other applications below it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it's a known limitation...
Sadly, what I want to do is not possible without https inspection... And I can't enable https inspection if I don't know the user...
Thanks for your time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPSi is not related to the user management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's not what I mean.
I want to enable https inspection when the user is authenticated in the web portal or with the identity agent, not before
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understood the first time. HTTPSi happens before any other rulebase match, so you cannot enable it on per user basis only. You can bypass it based on source and destination though.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 29 | |
| 11 | |
| 10 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter