- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: View the IP/VMAC/MAC of the VIP and the IP/MAC...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Show cluster members interfaces all from Gaia Clish - see the IP/MAC of each member and VIP
show cluster members interfaces all from Gaia Clish
Hello, good afternoon:
If I don't have access to expert mode.
With the commands:
-show cluster members interfaces all from Gaia Clish.
Can I see the IP and MAC of the Cluster VIP ?
-How can I see the IP/MAC of each member, as well as the VIP VMAC of the firewalls, in order to track and identify these MAC in the adjacent switches, to map where each interface of the two firewalls is connected.
The objective is:
Identify the VIP IP/VMACs and the individual IP/MACs, of each of the Firewalls.
Example the VIP IP is the IP 172.16.200.254, associated to eth1 and one of the Firewalls has the IP 172.16.200.1 and the other Firewall has the IP 172.16.200.2.
If I run from one of the Firewalls, "show interface eth1". It shows me the MAC/IP of the VIPs, but not the individual ones. I want to know how to see both the VIPs IP and their MAC/VMAC, as well as the IP/MAC of each of the firewalls in the cluster. This in order to keep track of their respective VMAC and MAC and to be able to identify which switches are connected to each of the Firewalls, to keep track of the interfaces and to know which interfaces of the switches are connected to Firewall 01 and Firewall 02.
Thanks for your time
I remain attentive
Best regards
30 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can run cphaprob -a if even from clish.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock Thank you for your time and comments.
I run, on one of the Firewalls directly.show interface eth1, show interface eth2.
And with these commands it showed me the VIP IP, that is to say the VIP IP of the cluster of each one.
But if I then run, "show cluster members ips" and it shows me the IP of each member of the cluster, example: Unique IP's Table ---- Member Interface IP-AddressFor the eth1 172.16.100.3For the local eth1 172.16.100.2The VIP is 172.16.100.1.
When I put show interface eth1, by ssh directly on the main FW, i.e. show interface eth1, I get the IP 172.168.100.1 ( THE VIP ) with MAC 00:1c:7f:83:d5:f0.But here is my confusion, it is supposed that with "show interface eth1" it should show me the local IP of the Firewall, the individual one not the VIP ? the expected result is that with show interface if it shows me the VIP ?
There is no way to see the IP/MAC of each member, that is to say the individual IP/MAC for each Firewall of the cluster?
Since when entering the FW01, I enter, I execute show interface eth1 or show interface eth2, and it shows me the IP/MAC of the VIP of the Cluster, but not the individual ones.
I am mapping what is connected to what, to correctly map the Interfaces of the adjacent switches to the Firewalls, therefore I will need to see the MAC of both the FW01 and FW02, not only the VIP, to then track the MAC from the switches.
Thanks for your time.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey mate,
Lets connect tomorrow morning, I got some time, so I can show you my perfectly working R81.10 lab with cluster configured. Mgmt is R81.10, then I have R81.10 HA cluster, as well as single R81.10 gateway. Happy to run any commands and we can figure it out.
Just message me privately and we can set something up. Im good for 10 am EST tomorrow if that works.
Let me know.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock colleague, thank you very much for your time and for your proposal.
I'm a bit full tomorrow, between sessions, meetings, etc. Thank you very much for your good will.
Finally the goal of this is to understand and find out the following:
-The IP/VMAC/MAC of the Cluster VIP IPs and also to be able to have the individual IP/MAC for each of the Firewalls.
I mean example: One of the members has IP: 172.16.100.3 the other Firewall has the IP 172.16.100.2 and the VIP is the 172.16.100.1. Therefore recognize both the MAC/VMAC of the VIP IP and the IP/MAC of each individual firewall.
Thank you very much for your time and comments. For now, in order not to bother you, if you could help me to know with which "commands" exactly ( with or without Expert mode access ) I could collect this information, that I just told you.
The purpose is to have everything mapped, correctly, IP/MAC/VMAC/VIPs, etc in order to have the MACs and follow these MACs on the adjacent switches and thus be able to determine where it is connected to which switches and which interfaces of the Firewalls.
Again, thank you very much for your help and time.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, let me run some commands tomorrow and will update you.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How about show interfaces all? (a clish command)
You can use something like the following to see it on all gateways: https://community.checkpoint.com/t5/SmartConsole-Extensions/Execute-Commands-SmartConsole-Extension/...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was thinking that too, but then reading the posts, sounded like there was more to it. Lets see what @CheckGatzMet says : - )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, how are you doing, thanks for the reply.
If I run the commands show interface all or show interface eth1 or show interface eth2, the output of these commands shows the VIP IP, that is if I connect to the FW01 and run show interface all or show interface eth1 or show interface eth2, it shows me the IP and VMAC/MAC of the VIP.
What I am looking for is to have the IP/VMAC/MAC of the VIP and also the IP/MAC of each of the IP members of the cluster.
Example: The VIP eth1 has the IP 172.16.200.254 has X VMAC/MAC and each Firewalls of the Cluster, each node has the eth1 IP 172.16.200.1, and the other node has the eth1 IP 172.16.200.2. Both the IP 172.16.200.1 and the IP 172.16.200.2, have their own MAC, in each Firewall.
It is that information that I need, the MAC/VMAC of VIP 172.16.200.254 and the MAC of IP 172.16.200.1 of Firewall Node 1 and the MAC of IP 172.16.200.2 of Firewall Node 2.
That is the precise information I need to collect and get from the firewalls.
Thank you for your time, collaboration and good disposition
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only commands I can think of are what @PhoneBoy gave you, show interface all and then cphaprob -a if, which would show you the VIP/VMAC as well.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock @PhoneBoy , thank you for your comments.
The point here is that, if I run the show interface eth1 or show interfaces all. The issue here is that if I run show interface eth1 or show interfaces all, on the FW01 node, it shows me the IP/MAC of the VIP, not the IP of the Node which is what I have been explaining and detailing in the post.
With the command, cphaprob -a if, it shows me the VIP IPs and the MAC/VMAC.
But what I need to know and get is
VIP IP eth1 172.16.100.1/24 its VMAC/MAC of the VIP.
Firewall Node 1: IP eth1 172.16.100.2, its specific MAC, from that IP the 100.2 ( Not from the VIP but from the Node )
Firewall Node 2: IP eth1 172.16.100.3, its specific MAC, from that IP the 100.3 ( Not from the VIP but from the Node ).
Example:
172.16.100.1 VIP VMAC/MAC: 00:1c:7f:83:d5:f2 ( VMAC/MAC of the VIP )
Node1: 172.16.100.2 MAC: 00:1c:7f:83:d5:89 ( Your own specific MAC )
Node2: 172.16.100.3 MAC: 00:1c:7f:83:d5:72 ( Your own specific MAC )
With one or multiple commands, or however you can, but the idea is to be able to obtain that precise information, VIP/VMAC/MAC of the Cluster and of each of the nodes, their respective IP/MAC.
Thank you for your time, comments and collaboration.
I remain attentive to your comments
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me know when you are free Friday and we can do remote and check.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ip -4 a
Or even if you dont have access to firewall you can run the command from dashboard by right clicking on cluster member and then run script.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ifconfig -a (from expert mode) should show the real MAC addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy has already described it well.
Maybe the following will help you.
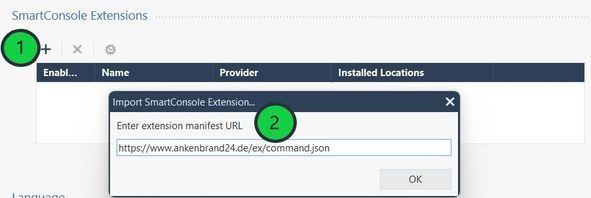
1) Install the SmartConsole extension "Execute Commands"
1a) On SmartConsole, go to Manage & Settings > Preferences > SmartConsole Extensions > +.
1b) Enter the web-service manifest URL
https://www.ankenbrand24.de/ex/command.json
and click OK.
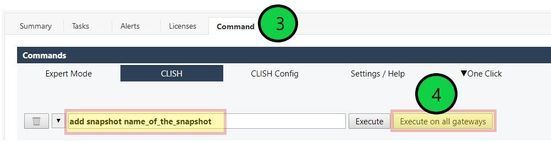
2) On SmartConsole, go to Gateways & Servers > Command
3) Open the menu item "CLISH". The same works with Expert Mode commands in the menu "Expert Mode".
4) Add the Clish command "show interfaces all" and then execute "Execute on all gateways".
Now "show interfaces all..." will be executed on all your gateways.
PS:
You can also use the Expert Mode oneliner from this article "Interface State - All ", this shows you all interface settings:
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be able to pull Cluster IPs from this command. I would suspect once you have this information a quick ping/ARP check should give you the MAC of each. Unless someone knows of a specific way to gather that information from GUI/CLI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @CE_SE thanks for your comments.
From Gaia Clish, I can run, "show cluster members ips" and with that get the cluster member IPs OK. If, after that, in the same firewall, you recommend doing a ping, from one of the firewalls, and then pinging the cluster member IPs. After that, consult with show arp dynamic all or with arp -a, to validate the MACs associated with the IPs, in the arp table. Is this what you mean?
Both the commands show arp dynamic all or arp -a (confirm if these arp commands are correct please ), and ping , are commands that can be executed from Clish ? or do you need to enter expert mode? or are these commands compatible with clish ?
Thank you, stay tuned, best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@CheckGatzMet All show commands has to run from clish or from cpshell while rest are linux commands which can be run from Linux bash shell i.e. #
Below commands would help you to identify ()
# cphaprob -a if
#fw ctl get ifs
#ip -4 a
clish> show interfaces all
clish> show cluster members interfaces all
# cpstat fw -f interfaces
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Blason_R Thanks a lot for your comments
Ok, so all the commands you mention can be executed with Gaia Clish, without having to log in as an expert ?
With the command, cphaprob -a if, it shows me the VIP IPs and the MAC/VMAC. If I use show interface all or show interface eth1, for example, the output show the VIP.
But what I need to know and get is:
VIP IP eth1 172.16.100.1/24 its VMAC/MAC of the VIP.
Firewall Node 1: IP eth1 172.16.100.2, its specific MAC, from that IP the 100.2 ( Not from the VIP but from the Node )
Firewall Node 2: IP eth1 172.16.100.3, its specific MAC, from that IP the 100.3 ( Not from the VIP but from the Node ).
Example:
172.16.100.1 VIP VMAC/MAC: 00:1c:7f:83:d5:f2 ( VMAC/MAC of the VIP )
Node1: 172.16.100.2 MAC: 00:1c:7f:83:d5:89 ( Your own specific MAC )
Node2: 172.16.100.3 MAC: 00:1c:7f:83:d5:72 ( Your own specific MAC )
With one or multiple commands, or however you can, but the idea is to be able to obtain that precise information, VIP/VMAC/MAC of the Cluster and of each of the nodes, their respective IP/MAC.
Thank you for your comments, your time and your collaboration.
Stay tuned
Kind regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately - I am still not getting it. Does that mean you need interface details or IP address details configured on members?
And if you see the commands I provided (#) -> indicates bash shell while I mentioned clish> as a prompt in front of the commands that needs to be executed in clish prompt.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Blason_R, thanks for your comments
I repeat the example and give more details.
Before building a Cluster, each Node has:
Firewall Node1: 172.16.100.2 with a single Mac, example: 00:1c:7f:83:d5:89.
The Node 2 Firewall: 172.16.100.3, with a unique MAC, example, 00:1c:7f:83:d5:72.
Therefore you have a different MAC for each Firewall in their respective Node1 Eth1 of Firewall Node 1, and another Eth1 Node 2 Firewall, both with their respective and unique IP, and with their respective and unique MAC.
Now when you build the Cluster, generate a VIP for that network.
In other words, the VIP IP will be 172.16.100.1, with its unique VMAC/MAC of the VIP and its IP members will be IP 172.16.100.2 and IP 172.16.100.3.
Now if I go to Node1 and Node2, and run a show interface eth1, I see the IP and MAC/VMAC of 172.16.100.1, but not the MAC of their respective member IPs, that is, I no longer see the MAC of the interfaces eth1, IP 172.16.100.2 nor 172.16.100.3. By running show interface eth1 or show interfaces all. I only keep seeing the VIPs, do you understand me?
What I want to know is like in a Cluster, where I know that IP 172.16.100.1 is the VIP and the member IPs are 172.16.100.2 and 172.16.100.3, what I need is to be able to see the original and unique MAC of each Node of its eth1 interface, that is, NODE1 172.16.100.2 and its unique MAC (not of the VIP) and in NODE2, with IP 172.16.100.3, to be able to see its unique MAC (not of the VIP).
That's what I need to be able to get from the firewalls.
Both the MAC/VMAC of the VIP, example 172.16.100.1, and the unique MAC of each node, that is, MAC 172.16.100.2 and MAC 172.16.100.3
With the show interface or show interface all command, it shows me the VIP, if I run it on each firewall, not the only one for each firewall, which is what I need, the only one for each node, it only shows me the VIP.
-FW-Node1===eth1===IP 172.16.100.2 -your unique MAC ( 00:1c:7f:83:d5:89 )
-FW-Node2===eth1===IP 172.16.100.3 - your unique MAC ( 00:1c:7f:83:d5:72 )
-VIP Cluster===eth1===IP 172.16.100.1 ( VIP su VMAC/MAC 00:1c:7f:83:d5:f2)
So that information I need, the Unique IP and MAC of the member nodes individually, and also the VIP IP/VIP/VMAC/MAC.
Thank you, I hope with the detail, my point has been a little clearer
Thank you for your time and for your collaboration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So VMAC can be disable if you dont want those. On a cluster member page you can uncheck the option vmac and cluster will not then have vmac enabled.
And if you need individual information then login to cluster member from expert mode #ip -4 a and cluster interfaces #cphaprob -a if
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Blason_R , thanks for your comments.
And what problems can exist when disabling the VMAC?
Now I will tell you, if I execute cphaprob -a if in each member of the cluster, it will give me information about the VIPs and their MACs, but not about the MACs of each cluster member, but about the VIP MACs and the IPs, but not the MACs of each node. Unfortunately I do not have Expert access to the Firewalls. How is it possible to obtain the MAC of the IPs of each member of the Cluster, without having to enter as an expert? Isn't there any other way? I don't think I'm the only one who needs to get information like this.
Is there any way to get this information from the console, SMART-1/from SmartConsole, by GUI or something like that? Yes, I have expert access to the Console/SMART-1, but not to the firewalls, just only acces direct clish on the firewalls.
Thank you for your time, good vibes and your collaboration
Stay tuned
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I personally did not find any issue if you are disabling the VMAC. Only if in case any of the cluster member failure and traffic is failed over to other member the floating IP is shifted to other member and at that time the devices the next hops should be immediately able to do the ARP resolution and start forwarding the traffic.
And correct cphaprob -a if command wont show physical mac; it would show only VMAC (if enabled) else you will have to use linux command to find physical MAC.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As @Blason_R mentioned, only linux commands work to get physical mac.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock , thank you for asking.
At the moment, they have not been able to give me access again to the Cluster to validate.
If only I had access to a virtual cluster, I could validate. At the moment I am waiting for the new session, to do the validations, execute the commands, and validate correctly the IP/MAC for the VIP, as well as for the individual nodes.
For the moment I am just waiting.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you mean virtual cluster? Whichever member is active will always be tied to virtual IP.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock thanks for your reply
I mean if I had access to a virtual environment, that is, a virtual Checkpoints, FW environment to set this up myself and test it, to validate something as simple as this, that's what I meant by virtual cluster. I think I find it complex and even confusing, how something as simple as identifying an interface/ip/mac, can give so much trouble and that there are multiple versions of how to reach such a goal.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I mentioned before, I have perfectly working cluster, so if you want me to test anything, its R81.10 cluster HA lab, so its not a problem.
Let me know.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter