- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: SAML authentication stops working after FW Upg...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SAML authentication stops working after FW Upgrade / Fresh Install
Hello Check Mates,
we have seen on three occasions that the SAML authentication method fails for Client VPN after upgrading to a new Jumbo or reinstalling the gateway from scratch (fresh install).
Reason for our fresh install was to get rid of the ext3 filesystem which we have on very old and long running firewalls.
since we rely on special custom hotfixes we are stuck to run at R81.10 HFA 110
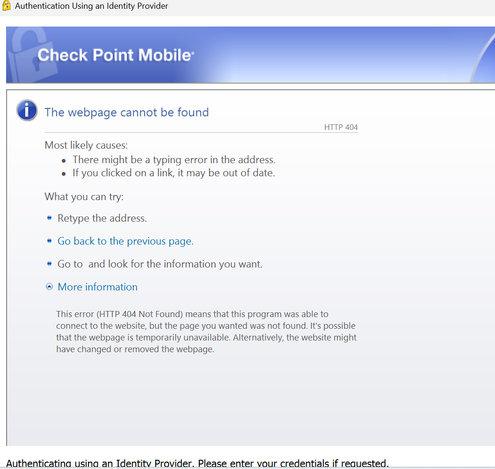
we get this error message:
x
The error lookalike depends on how the embedded browser is built into the VPN Client, sometimes its the full browser which shows and error, sometimes the browser is embedded into the VPN client itself.
It is very hard to restore the SAML login option.
Its more like a guessing game to remove the SAML authentication from the gateway, push policy again and adding SAML again. or do many reboot or fail overs. I cannot really say what brings it back ... its more a random success to have the SAML portal working again.
anyone from the audience has seen this before?
since it struck us 3 times now, i think there is indeed a systemic reason behind it.
after some discoveries i found some interessting hints:
i see way too little Multiportals running ???
| active member with broken SAML portal | working member set to standby to check behavior |
| [Expert@XXXY1:0:ACTIVE]# mpclient list DLPSenderPortal SecurePlatform UserCheck nac nac_transparent_auth saml-vpn |
[Expert@XXXZ2:0:STANDBY]# mpclient list DLPSenderPortal ExchangeRegistration ReverseProxyClear ReverseProxySSL SecurePlatform UserCheck nac nac_transparent_auth saml-vpn sslvpn |
when i check if the paths for the SAML portal do exist ... i get disappointed on the newly installed active member they missing, also some directories are not there.
path is:
https://XXXXX.ZZZZ.com/saml-vpn/spPortal/ServiceProviderTabs?realm=vpn_XXXXX_SAML&session=6i7hz9koxb...
[Expert@XXXY1:0:ACTIVE]# find / -name ServiceProvider\*
/opt/CPSamlPortal/htdocs/spPortal/ServiceProvider
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/htdocs/spPortal/ServiceProvider
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
[Expert@XXXZ2:0:STANDBY]# find / -name ServiceProvider\*
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
/opt/CPSamlPortal/htdocs/spPortal/ServiceProvider
/opt/CPSamlPortal/htdocs/spPortal/ServiceProviderTabs
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/htdocs/spPortal/ServiceProvider
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/htdocs/spPortal/ServiceProviderTabs
so it seems the directories and files to run the SAML portal where just not created ... how come?
TAC has to be involved ...
best regards
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
TAC finally solved it ...
PRHF-33044 is the Bug ID
the issue seemed to start with HFA113, which breaks some files in /opt/CPSaml file structure.
Fresh install with R81.10
install HFA in HFA 129 in my case
Install custom fix provided by TAC for HFA129
SIC + Policy Push
and SAML is working again ...
i hope they integrate it into the next GA HFA ...
otherwise you can do it manually:
backup of both directories
and copy the good files to the affected FW.
scp -rp /opt/CPSamlPortal/* admin@XXXXX:/opt/CPSamlPortal
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have experienced the same issue with after we upgraded a AWS GEO cluster from r80.40 to r81. We have a case open with TAC.
The second scenario is for Maestros.. initially it was running on r81.10 take 95 + custom fix for SAML.
After upgrade to take 132 ( which required the custom fix to be uninstalled ) SAML is broken/firewall cannot be accessed using GUI, and there are issues with IPsec tunnel rekey. case is open with TAC for this as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello yes understood.
well TAC is already working on it ... iam confident they will find it 🙂
also check this SK sk181971 but its for Error 400 and not Error 404.
i suspect i could easily transfer the folders from the working FW to the broken FW. but i want a solid hotfixes and explanation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
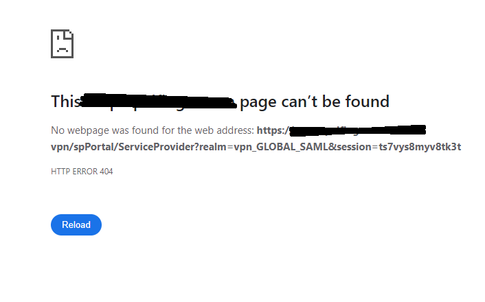
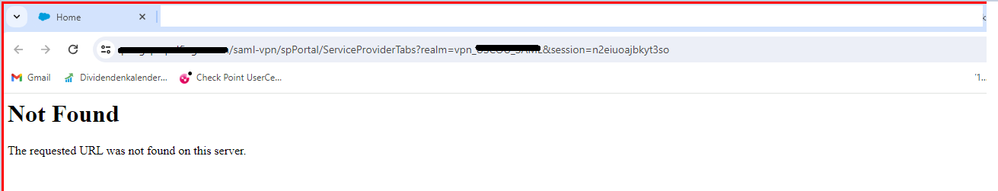
Same "Not Found" issue after upgrading to 81.10.
I noticed ServiceProvider changed to ServiceProviderTabs in the URL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had same problem after fresh install + take 130
The fix is: uninstall JHF, install an intermediate JHF (in my case #78), then upgrade to latest JHF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
TAC mentioned, this issue is known as : PRHF-33044.
if required they will build a custom fix for you.
if it affects a R81.20 fresh install is still under investigation!
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
TAC finally solved it ...
PRHF-33044 is the Bug ID
the issue seemed to start with HFA113, which breaks some files in /opt/CPSaml file structure.
Fresh install with R81.10
install HFA in HFA 129 in my case
Install custom fix provided by TAC for HFA129
SIC + Policy Push
and SAML is working again ...
i hope they integrate it into the next GA HFA ...
otherwise you can do it manually:
backup of both directories
and copy the good files to the affected FW.
scp -rp /opt/CPSamlPortal/* admin@XXXXX:/opt/CPSamlPortal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Thomas,
It seems that we encounter the same issue as yours with the broken SAML Portal (404 on connection attempts).
Our SG cluster is in R81.10 with Hotfix 139.
The current CPSamlPortal structure is as follows:
[Expert@PROXIMA:0]# find / -name ServiceProvider\*
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProvider.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/phpincs/simplesamlphp/vendor/simplesamlphp/saml2/src/SAML2/Configuration/ServiceProviderAware.php
/opt/CPSamlPortal/spPortal_BEFORE_R81_10_jumbo_hf_main/htdocs/spPortal/ServiceProvider
/opt/CPSamlPortal/htdocs/spPortal/ServiceProvider
As we only have one cluster with the same broken SAML structure, we don't have the possibility to copy the original files to /opt/CPSamlPortal.
Would you (or any generous soul) be willing to send us these files in order to fix the VPN SAML connection?
Thanks 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I did use "Fresh Install and Upgrade feature" to upgrade from R81.10 take 130 to R81.20 and I got the same issue. I had to rollback the upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For anyone interested to fix the issue without the custom fix, i suggest the previous workaround:
-clean install 81.10
-install JHF 78
-Install latest JHF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Team,
better use a BLINK image and go to R81.20 directly!
then you should have NO issues!
or downgrade to a hotfix around ~R81.10 HFA 110 and upgrade to to HFA 150 ... then SAML should stay.
also there is a hotfix for this issue!
PRHF-33044
fw1_wrapper_HOTFIX_R81_10_JHF_T129_937_MAIN_GA_FULL.tar
but its R81.10 HFA120
-> reach out to TAC, they shall give you a portfix for your version!
i have no more customer running on R81.10, believe or not .. so i cannot send any files.
what u can also do is to install a GW in a VMware and copy the files as well!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the SK in reference for fw1_wrapper_HOTFIX_R81_10_JHF_T129_937_MAIN_GA_FULL.tar
Documented to be fixed R81.10 jhf 152
https://support.checkpoint.com/results/sk/sk182128
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I had SAML working with R81.20 JHF84 and it's not in JHF89. We aren't even getting to the provider link now from the portal. There were some new changes to SAML and also, The Security Gateway may fail to resolve external Network Feeds whose URL contains a port number (such as "https://example.com:8080/feed.csv". Refer to sk182684. maybe it fixed 8080 and broke 8443
Update: we fixed this by changing this attritube in the Identity.xml file:
from "true" to "false" WantAuthnRequestsSigned="false"
This page isn’t working
portal.ssl.somedomain.com is currently unable to handle this request.
HTTP ERROR 500
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi there,
i have the same issue at 81.20 on our cluster. i configured the SAML (properly, i hope) but i end with "Not found" as im trying to access it
the link in the adressbar is right so far: mysamldomain.com/spPortal/ServiceProviderTabs?realm=vpn.....
at least the domain is correct, i cant tell anything about the rest built by checkpoint.
Unfortunately i dont have any backup or old stuff laying around to recover some of those maybe missing files.
Could someone upload a zip with the files in it, at least to compare whats missing?
i also checked the error_log of the portal and get those lines:
[Mon Jan 27 13:26:39.274902 2025] [php7:notice] [pid 28000] [client 10628] error SamlPolicyReader: IDP_POLICY_DIRECTORY /opt/CPVPNPortal/phpincs/spPortal __DIR__ /opt/CPSamlPortal/phpincs/spPortal, referer: https://mfax.de/webapps/openid/spPortal/ServiceProviderTabs?realm=vpn_RVDev_MFA&session=cvaq33za55jeezt
[Mon Jan 27 13:26:39.275958 2025] [php7:notice] [pid 28000] [client :10628] error allowRealms: 'vpn' is not a SAML realm., referer: https://mfax.de/webapps/openid/spPortal/ServiceProviderTabs?realm=vpn_RVDev_MFA&session=cvaq33za55jeeztThanks in advance
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Florian,
When authenticating, I´d start with a small browser extension like "SAML-Tracer" for having a look, what is when called and submitted. Also Browsers Development tools can help in fiddling out, where a problem might be. i.e. if a css file is not "accessible", like in my current case... I´m fighting something similar at the moment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hy Nüüül and thanks for your hints.
unfortunately the browser isnt doing a lot but opening and showing that "Not Found" stuff. the login procedure isnt started because of that issue
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Floriam
did u fix the problem ?
same logs, same issue
apparently files/direcotry/permission are correct, looking into another working environment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
No, unfortunately not. its still not working. we asked our Checkpoint-Service for help on that. They think that it propably could come into account that our used IP-Address is already configured elsewhere in the system (and also not the cluster main IP)
So we ordered a new external IP-Adress and try then to forward 443 to this
i will update the thread if were working it out. If you find anything new feel free to post it here as well
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is likely not your issue, as it was working previously, but I had the exact same 404 error, my issue was I had the wrong IDP object assigned to my gateway. VPN Clients -> Authentication -> IDP Auth Provider -> Auth Methods -> Identity Provider - Auth Settings.
My IDP object was pointing to the SAML URL of a different gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, RE: the identity file, we changed this attribute from true to false. WantAuthnRequestsSigned="false" We still have to have this in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we solved that issue with the implementation of new external IP addresses
the problem is that the checkpoint portal already listens on 443
i hadnt to change my idp object. we just used a new and free IP-Address for the saml-vpn and now it works as it should
summary: you need a free ip
regards
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter