- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Routing between VPNs
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Routing between VPNs
Dear all,
I need your advice about a VPN routing challenge we have.
As part of the different VON communities we have, we have the following 2 ones:
[Office A - Gaia 80.30] <------ S2S Meshed VPN Community ------> [Data Center - Gaia 77.30]
[Data Center - Gaia 77.30] <----- S2S Meshed VPN Community -----> [AWS Cloud]
Now we would like to allow users in the Office A to connect to instances in AWS.
Therefore we would need to route the AWS Network through the 1st community to our Data Center and then through the 2nd one to AWS.
We tried to add a IPv4 static routing in the Checkpoint of the Office A to the IP of the one in our Data Center but the traffic is not routed through the community.
I saw several post talking about editing conf file on the router or using some R80 features but there was so many variant that I'm unsure what we should do. Another solution we think about would be to merge both community in a star one.
So any advice on how to get this working is welcome 🙂
Many thanks
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dhueber,
Use a star community.
For more granular control over VPN routing, edit the vpn_route.conf file in the $FWDIR/conf/ directory of the Data Center SMS:
[Office A - Gaia 80.30] <-- S2S Star VPN Community ---> [Data Center - Gaia 77.30] <--S2S Star VPN Community---> [AWS Cloud]
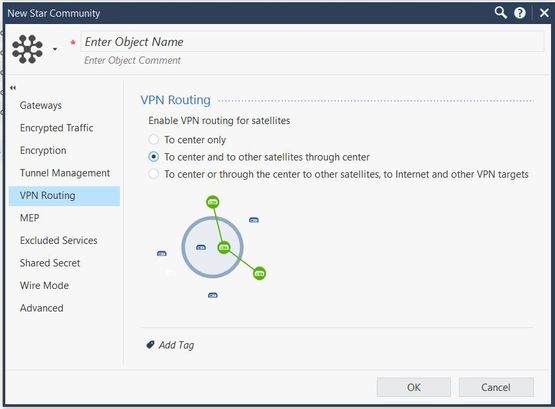
Consider a simple VPN routing scenario consisting of Hub and two Spokes. All machines are controlled from the same Security Management Server, and all the Security Gateways are members of the same VPN community. Only Telnet and FTP services are to be encrypted between the Spokes and routed through the Hub:
Alhough this could be done easily by configuring a VPN star community, the same goal can be achieved by editing vpn_route.conf:
Destination Next Hop router interface Install on
Spoke [Office A - Gaia 80.30] Hub [Data Center - Gaia 77.30] Spoke [AWS Cloud]
Spoke [AWS Cloud] Hub [Data Center - Gaia 77.30] Spoke [Office A - Gaia 80.30]
And enable VPN routiong to center and to other satellites through center (same on R77.30):
PS:
R77.30 is since approximately one year out of support:-)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dhueber,
Use a star community.
For more granular control over VPN routing, edit the vpn_route.conf file in the $FWDIR/conf/ directory of the Data Center SMS:
[Office A - Gaia 80.30] <-- S2S Star VPN Community ---> [Data Center - Gaia 77.30] <--S2S Star VPN Community---> [AWS Cloud]
Consider a simple VPN routing scenario consisting of Hub and two Spokes. All machines are controlled from the same Security Management Server, and all the Security Gateways are members of the same VPN community. Only Telnet and FTP services are to be encrypted between the Spokes and routed through the Hub:
Alhough this could be done easily by configuring a VPN star community, the same goal can be achieved by editing vpn_route.conf:
Destination Next Hop router interface Install on
Spoke [Office A - Gaia 80.30] Hub [Data Center - Gaia 77.30] Spoke [AWS Cloud]
Spoke [AWS Cloud] Hub [Data Center - Gaia 77.30] Spoke [Office A - Gaia 80.30]
And enable VPN routiong to center and to other satellites through center (same on R77.30):
PS:
R77.30 is since approximately one year out of support:-)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
thanks for the reply and feedback. This is what we thought.
Won't be the easiest solution to recreate all our VPNs but we will have to go through this process.
Many thanks for taking time to answer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
migrating to one community with your datacenter as Center and officeA and AWS as satellites would be the best solution.
Then you have to enable VPN routing on the community and everything should work.
In your described environment with two communities you can configure VPN routing via vpn_route.conf file.
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
It‘s written for an SmartLSM environment but the solution is the same for you.
Have a look at the documentation Configuration in the VPN Configuration File
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see, @HeikoAnkenbrand sent an answer a little bit earlier then me.
😀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Congratulations @HeikoAnkenbrand you’re the winner today 😂
And we could help @dhueber with a solution.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko/Wolgagn,
I had a similar scenario and hoped you could help with a doubt. Our scenario is the same but instead of [AWS cloud] we have a third party Gateway. So in this case i think vpn_route.conf does not apply because it is not possible to define the third party in the "install on" column of the file. I was wondering how to address this. My first option was to migrate to a star community as you described before, but i am not sure if the option "To center and to other satellites trough center" will work with the third party gateway (i think it won't). So if you have any idea to get the same goal with the third party, it would be appreciated. Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks very much for that information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue is when you define the vpn_route.conf file, the install_on column must be the gateway object. I define my remote fw which is Fortinet is Interoperable Device. Below is the issue come out when I tried to install the policy.
reading vpn_route.conf: install on gw object is not a firewall (fortinetfw.fortiddns.com)
Do you know how to sort it out ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, i have the same issue with vpn_route.conf. Did you find a solution?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, i have the same issue with vpn_route.conf. Did you find a solution.
Thanks
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 28 | |
| 27 | |
| 11 | |
| 10 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter