Hi PhoneBoy,
thank you for the reply.
1) The VPN Communities are settled as star communities.
VPN Routing: last option To center or thro... , internet and other VPN targets.
2) ON the encription domain of peer_A i have: only 172.29.70.0/24 - 172.29.71.0/24 from my side with peer_A i have: 172.29.71.0/24, and the single host 10.10.4.34, 10.11.1.47, 10.200.4.33
On the encription domain of peer_B they have add 172.29.70.0/24 and other network....
from my side with peer_B i have add 172.29.70.0/24 and other network...
3) NAT is done by me versus peer_A with this network 172.29.71.0/24
In the mean time we had tried a lot and probably we achive a solution:
First we tried to add on the encription domain of peer_A also the network of peer_B 10.200.4.0/23 (so we connect directly the single host 10.200.4.33 without nat) everythings worked fine. So we were sure that's the problem was NAT done by me.
We split the NAT network into two networks: 172.29.71.0/25 and 172.29.71.128/25; we used the first network for nat host and device behind my gateway and the second one for nat host behind peer_B. But now it’s peer_B that is natting the hosts behind itself (10.200.4.33) so the package from peer_B is already NATTED and my checkpoint just reroutes through VPN.
Seem that's this is the way, as you see this are the last attempt
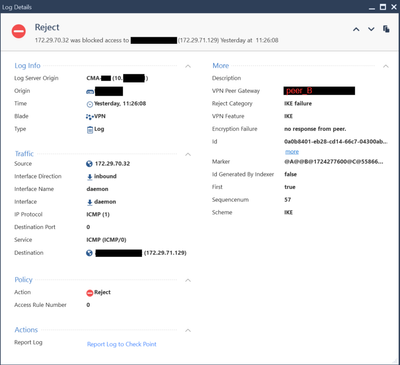
1) host (behind peer_B) 10.200.4.33 natted 172.29.71.129 that's is comunicating with network_A 172.29.70.0/24 working fine
2) host (behind peer_A) 172.29.70.32 that's is comunicating with the host 172.29.71.129 (behind peer_B) it's not working but
My checkpoint gateway re-route correctly in the vpn communities of peer_B ( and this wasn't done before).

I think that's now is just a misconfiguration on peer_B this are the detail of the third log: