- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E5:
Powering Prevention: The AI Driving Check Point’s ThreatCloud
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata, Securing the Agentic AI Era
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- VPN problems - Clear text packet should be encrypt...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
VPN problems - Clear text packet should be encrypted
Hi,
Check Point R81.10 appliance. Cisco ASA 5506 peer.
I am trying to get IPSec policy-based VPN up and running on a field installation.The VPN connection was working fine for several years, until the remote end changed to Oneweb satellite provider and our Cisco ASA was moved from a public IP to a 192.168 private address on their network. T
When trying to establish the VPN connection, I get a 'Clear text packet should be encrypted' from their Oneweb gateway IP in our firewall for UDP/4500, and the packet is dropped.
I have configured user.def & crypt.def on our management server according to https://support.checkpoint.com/results/sk/sk108600, but this did not help... NAT-T is enabled on out firewall.
The IP address of the remote is x.x.x.0. Could the zero IP-address cause problems with a Check Point firewall?
Best,
Nils
Labels
- Labels:
-
Site to Site VPN
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Found the solution!
UDP4500 IKE_NAT_TRAVERSAL had to be added to 'Excluded Services' for the VPN community...
A big thanks to all that took time to help!!
Best,
Nils
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That message means the firewall received a packet from a source address in some peer's encryption domain to a destination address in its own encryption domain. You need to figure out which address shouldn't be in which encryption domain and remove it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The encryption domains is as they were when we had a public IP on the ASA and a operational VPN.
Double checked and the encryption domains are OK and configured like all the other VPN field connections we have.
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That message is always an encryption domain issue.
What is the interoperable device's IPSec VPN > Link Selection set to?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are 100% correct, but maybe not so obvious on their end until someone does the remote session to verify. @NilsKS , did you work with TAC as of yet or no?
Regards,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, I have not worked with TAC. I have contacted our Check Point vendor, but they have not come up with a solution.
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Link Selection: Always use this IP address: Main address.
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And which one is the main IP address?
You should probably use the private address as the main IP address on the object, set Link Selection to use a statically NATed address, and specify the public address there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IP for ASA external interface is 192.168.200.10.
I have tried to set this as the IP for the interoperable object and configured the IP on the modem via Link Selection > Always use this IP address > Statically NATed IP, but this did not work. I do not see any traffic from either of these IP-addresses in the logs.
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do they see on Cisco side? Here is simple debug guy I used to work with few years ago gave me (he worked for Cisco TAC in India)
Regards,
Andy
debug vpn:
debug crypto condition peer x.x.x.x
debug crypto ikev1 200 (or v2, whichever is used)
debug crypto ipsec 200
to cancel all debugs-> undebug all
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I remember right, crypto map on Cisco refers to phase 2 and debug shows it all matching, so logically, seems like something on CP is no "agreeing" with Cisco side.
Can you verify 100% that vpn domain on CP side indeed includes eveything thats supposed to go through the tunnel? I mean, everything needed behind the CP firewall.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
Thanks for still being in the loop on this one! Much appreciated!
The VPN domain for the center gateway (Check Point) is the same as for our 10+ other VPN installations using Cisco ASA. It contains all the networks defined on the enc. domain on the ASA.
The VPN domain for the satellite gateway (the ASA) is the internal 172.22.154.128/27 network on the ASA.
I am not able to find any anomalies with this.
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
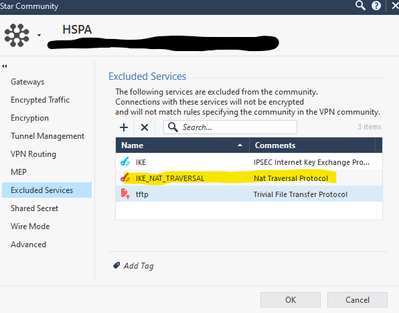
Found the solution!
UDP4500 IKE_NAT_TRAVERSAL had to be added to 'Excluded Services' for the VPN community...
A big thanks to all that took time to help!!
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad its fixed, but I find it odd that was the solution. I had never seen a scenario where that needed to be done.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Older thread but just recently ran into this. I'm curious but by chance do you have Implied rules disabled on your gateway? We have implied rules disabled and found that by default, implied rules are not encrypted but since we don't have them on we had to manually add to the Excluded Services like you did.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see what Bob is saying, as that message would always imply an issue with enc. domain, since it specifically means that packet that came in clear should have been encrypted, meaning go through the VPN tunnel.
If you do fw monitor for that IP, what do you see? If last insp. point (O) shows, that means its NOT being encrypted.
Also, just on a side note, if natting through VPN is taking place, ensure that nat is enabled inside VPM community (advanced tab I believe)
Cheers,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
NAT is enabled within the community.
ONEWEB=ISP PUBLIC IP
CHECKPOINT=CHECK POINT PUBLIC IP
# fw monitor -F "$ONEWEB,0,$CHECKPOINT,0,0" -F "$CHECKPOINT,0,$ONEWEB,0,0"
...
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=39737
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=39752
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=19902
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=19902
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=27692
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=27692
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=39772
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=7485
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=7485
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 168 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=41057
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=41066
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=28322
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=28322
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=2851
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=2851
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=42857
UDP: 500 -> 500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=21689
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=21689
UDP: 500 -> 500
create_one_data: no packets left to merge, but 168 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=44621
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=44628
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=31060
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=31060
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=13765
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=13765
UDP: 500 -> 500
create_one_data: no packets left to merge, but 420 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=45293
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=45301
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=6269
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=6269
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=352 id=17475
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=352 id=17475
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=156 id=45323
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=23191
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=23191
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=332 id=8697
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=332 id=8697
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=45443
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=6628
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=6628
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=46179
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=12098
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=12098
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=46199
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=13925
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=13925
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=46209
UDP: 500 -> 500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=13308
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=13308
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=47113
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=6325
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=6325
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=47764
UDP: 500 -> 500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=8267
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=8267
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=48022
UDP: 500 -> 500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][ppak_0] bond0.901:id[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=18576
UDP: 4500 -> 4500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=124 id=18576
UDP: 4500 -> 4500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=48962
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=10778
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=10778
UDP: 500 -> 500
create_one_data: no packets left to merge, but 84 bytes left in buffer!
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=50122
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=3817
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=3817
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=50275
UDP: 500 -> 500
create_one_data: no packets left to merge, but 252 bytes left in buffer!
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=19307
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=96 id=19307
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=352 id=24226
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=352 id=24226
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=156 id=50371
UDP: 500 -> 500
[vs_0][ppak_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=332 id=31644
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:i[44]: ONEWEB -> CHECKPOINT (UDP) len=332 id=31644
UDP: 500 -> 500
[vs_0][fw_0] bond0.901:O[44]: CHECKPOINT -> ONEWEB (UDP) len=260 id=50382
UDP: 500 -> 500
^C monitor: caught sig 2
Thanks!
Best,
Nils
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The filtering is wrong. You are looking to GW to GW IKE/IPsec traffic with this filter. In fact, you want to see the traffic which is cleartext while should be encrypted. Use the IP address from the drop VPN log to filter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
This is the traffic being blocked...
Id: 0affff37-b5bb-e31d-6553-31c035650000
Marker: @A@@B@1699916401@C@8872156
Log Server Origin: x.x.x.x
Time: 2023-11-14T08:37:20Z
Interface Direction: inbound
Interface Name: bond0.901
Id Generated By Indexer:false
First: true
Sequencenum: 16
Log ID: 404822
Source: ONEWEB
Source Port: 4500
Destination: CHECKPOINT
Destination Port: 4500
IP Protocol: 17
Scheme: NA
Methods: ESP: AES-256 + SHA256
Encryption Failure: Clear text packet should be encrypted
VPN Feature: VPN
Action: Drop
Type: Connection
Policy Name: xxx
Policy Management: yyy
Db Tag: {9229EFFB-8C2B-F84A-B1B0-FAF838AF6345}
Policy Date: 2023-11-14T06:58:28Z
Blade: VPN
Origin: CHECKPOINT
Service: UDP/4500
Product Family: Access
Logid: 1
Interface: bond0.901
Description:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What does it show in vpnd.elg when you filter for peer's external IP?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the firewall module:
grep $ONEWEBIP $FWDIR/log/vpnd.elg*
Nothing...
Best,
Nils
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 32 | |
| 16 | |
| 13 | |
| 12 | |
| 10 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 5 |
Upcoming Events
Fri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter