- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: R80.x Ports Used for Communication by Various ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
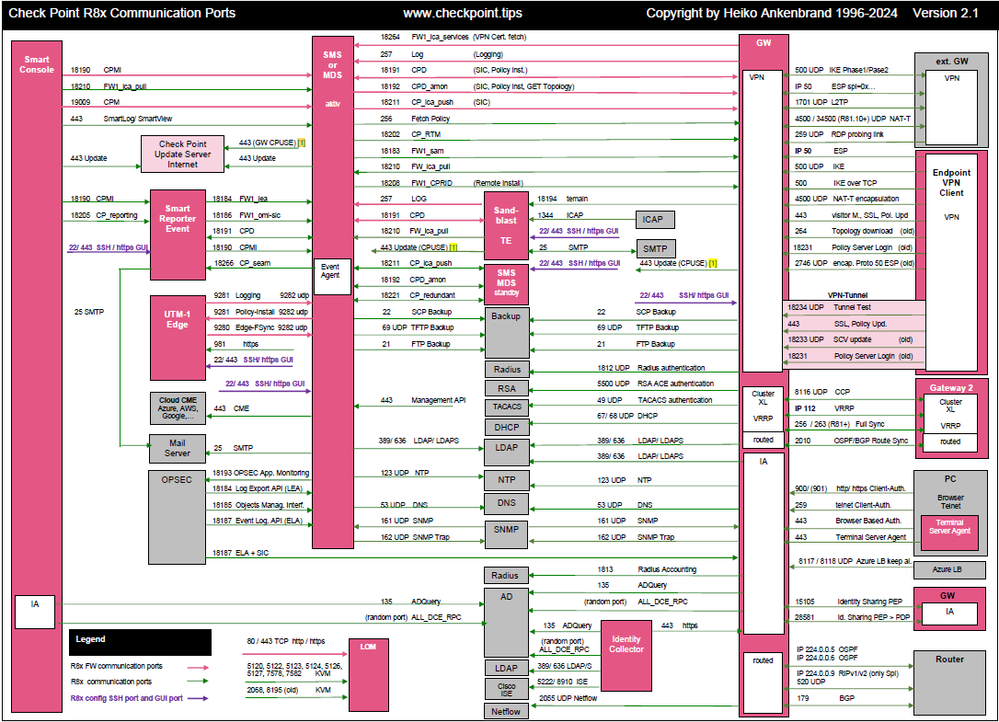
R8x Ports Used for Communication by Various Check Point Modules (new version 2.1)
| Introduction |
|---|
This drawing should give you an overview of the used R80, R81 ports respectively communication flows. It should give you an overview of how different Check Point modules communicate with each other. Furthermore, services that are used for firewall operation are also considered. These firewall services are also partially mapped as implied rules in the set on the firewall.
| Overview |
|---|
| Download PDF |
|---|
Download R8x:
R8x Ports Used for Communication PDF
| SmartConsole Extention |
|---|
New!
Now I have developed a SmartConsole Extension so that you can view the overview directly in the SmartConsole.
In the Access Policy section in the upper area, there is a tab called "Ports for Modules". More infos here.
Extension URL: https://www.ankenbrand24.de/ex/ports.json
| References |
|---|
Support Center: Ports used by Check Point software
| Versions |
|---|
Version 2.1:
+ v2.1c all new R82 ports + two bugs fixed 10/20/2025
+ v2.1b all new R82 ports (IA + RA VPN ikev2) 10/29/2024
+ v2.1a all new R81.20 ports (Cloudguard + VPN + ClusterXL) 07/15/2024
old Version 2.0:
+ v2.0f new! now with SmartConsole Extension 02/13/2023
+ v2.0e add LOM port 2048 01/31/2023
+ v2.0d add LOM ports 01/23/2023
+ v2.0c new colors + design 01/22/2023
+ v2.0b best mistake 🙂 SmartDashboard versus SmartConsole 01/22/2023
+ v2.0a correct names : SMS, MDS, SmartConsole, ... 01/21/2023
old Version 1.9:
+ v1.9a add port 443 cloud CME 19.03.2022
+ v1.9b fix port issue 442 cloud CME 22.03.2022
old Version 1.8:
+ v1.8a R81.10 EA update 04.05.2021
+ v1.8b add port 18264 30.05.2021
+ v1.8c R81.10 upgrade 28.07.2021
old Version 1.7:
+ v1.7a R81 EA update 17.07.2021
+ v1.7b bug fix 20.08.2021
+ v1.7c bug fix + new download link 25.06.2021
old Version 1.6:
+ v1.6a add Azure ports 05.05.2020
+ v1.6b add all cloud ports 15.06.2020
old Version 1.5:
+ v1.5a typos corrected 18.09.2019
+ v1.5b port update 26.01.2020
old version 1.4:
+ v1.4a bug fix, update port 1701 udp L2TP 09.04.2018
+ v1.4b bug fix 15.04.2018
+ v1.4c CPUSE update 17.04.2018
+ v1.4d legend fixed 17.04.2018
+ v1.4e add SmartLog and SmartView on port 443 20.04.2018
+ v1.4f bug fix 21.05.2018
+ v1.4g bug fix 25.05.2018
+ v1.4h add Backup ports 21, 22, 69 UDP and ClusterXL full sync port 256 30.05.2018
+ v1.4i add port 259 udp VPN link probeing 12.06.2018
+ v1.4j bug fix 17.06.2018
+ v1.4k add OSPF/BGP route Sync 25.06.2018
+ v1.4l bug fix routed 29.06.2018
+ v1.4m bug fix tcp/udp ports 03.07.2018
+ v1.4n add port 256 13.07.2018
+ v1.4o bug fix / add TE ports 27.11.2018
+ v1.4p bug fix routed port 2010 23.01.2019
+ v1.4q change to new forum format 16.03.2019
old version 1.3:
+ v1.3a new designe (blue, gray), bug fix, add netflow, new names 27.03.2018
+ v1.3b add routing ports, bug fix designe 28.03.2018
+ v1.3c bug fix, rename ports (old) 29.03.2018
+ v1.3d bug fix 30.03.2018
+ v1.3e fix issue L2TP UDP port 1701
old version 1.1:
+ v1.1a - added r80.xx ports 16.03.2018
+ v1.1b - bug in drawing fixed 17.03.2018
+ v1.1c - add RSA, TACACS, Radius 19.03.2018
+ v1.1d - add 900, 259 Client-auth - deleted od 4.0 ports 20.03.2018
+ v1.1e - add OPSEC -delete R55 ports 21.03.2018
+ v1.1f - bug fix 22.03.2018
+ v1.1g - bug fix - add mail smtp -add dhcp - add snmp 25.03.2018
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Tags:
- ad
- backup
- blades
- ccp
- clusterxl
- cmi
- communication
- dashboard
- dhcp
- dns
- dynamic routing
- edge
- endpoint vpn
- esp
- event agent
- ftp
- gateway
- ha_info
- http
- ia
- icap
- identity awareness
- identity collector
- ike
- implied rules
- infrastructure
- ise
- ldap
- log
- lom
- modules
- nat-t
- nat-tranversal
- netflow
- ntp
- opsec
- ospf
- performance
- ports
- r80
- r80.10
- r80.10 gateway
- r80.10 management
- r80.20
- R81
- r81.10
- radius
- rdp
- route
- routed
- router
- routing
- rsa
- sandblast
- secure client
- secure gateway
- security management
- smart event
- smart reporter
- smartdomain manager
- smtp
- snmp
- software blades
- tacacs
- threat prevnetion
- threatemulation
- used ports
- utm-1
- vpn
- vrrp
317 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice to learning for CCSA.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure if anybody said that already, but FW1_ica_services (tcp 18264) is missing in communication between SmartConsole and Management server. Also, not sure if 18210 is being used in that communacation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's indeed an omission from this otherwise great diagram. Note that tcp 18264 on the management is also accessed by gateways when they check for a CRL (they do this when runnig certificate based centrally managed VPN). With default settings and without access to the CRL, VPN connections fail with "invalid certificate".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have written very interesting articles here in Checkmates forum.
Thank you
Tsvika
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Really useful diagram, one to keep for sure.
I have a question regarding Endpoint Security VPN (formerly SecureClient), when creating the VPN sites the only way it would work is if I enabled visitor mode on the gateway. All appears to be working fine after creating the sites however I only ever see incoming 443 and UDP 4500, never see IKE over TCP or UDP, or ESP, is this behaviour right?
I assume the desktop policy doenloaded from the policy server now runs over 443 too?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great job @HeikoAnkenbrand .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great post!
How about Dedicated log server <> GW communication? Does this type communication needs MGMT<>GW ports? or narrower subset is enough?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
great job
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko!
Great diagram!
Regarding sk119134,
TCP 18264 should been added between SmartConsole and CPMgmt/MDM
That port allows SmartConsole to download CRLs from Management
and avoids the "CRLs failed to be downloaded"-issue during SmartConsole start.
Ciao Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
New ports updated.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Old R77.30 ports removed.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
great job
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice port overview
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
+v1.5b port update 26.01.2020
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I might be missing it, but I believe there is the following port missing from this diagram:
TCP 18264 - FW1_ica_services
When establishing a centrally-managed certificate-authenticated VPN tunnel, the gateways check the CRL over this port in plaintext (since tunnel is not yet up).
Thanks for the awesome diagram!!
Steven.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I am looking at version v1.5 cant see 18209 is this missing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great job @HeikoAnkenbrand
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
👍
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now with all new R80.40 ports.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice picture!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now with R80.40 update.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Azure ports update - 05.05.2020
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is an awesome diagram, much appreciated @HeikoAnkenbrand
I'm very interested in the R80.40 and Azure update as I'm currently having some communication issues between on prem management and CloudGuard IaaS (Azure)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 10 | |
| 10 | |
| 9 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter