- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: R82 – Install ElasticXL Cluster
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R82 – Install ElasticXL Cluster
| Overview |
|---|
ElasticXL is a new cluster technology that enables simplified operation with a single management object with automatic configuration and software synchronisation between all cluster members.
ElasticXL is expected to be delivered with R82 or later versions. ElasticXL is based on similar technology to Maestro, but without MHOs. It is based on Check Point's SP versions for a scalable platform that allows you to increase the performance of the security gateways almost linearly.
I have tested it with the R82 EA version.
You can find more information about ElasticXL in this article: R82 ElasticXL
| Install first ElasticXL gateway |
|---|
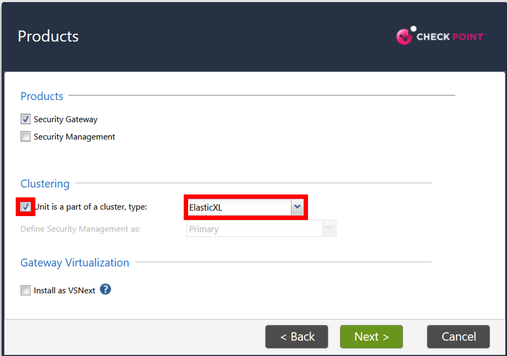
1) Run the GAIA installation wizard on the appliance and select "ElasticXL" for clustering.
If you want to use VSNext (replacement for the classic VSX), click the checkbox "Install as VSNext".
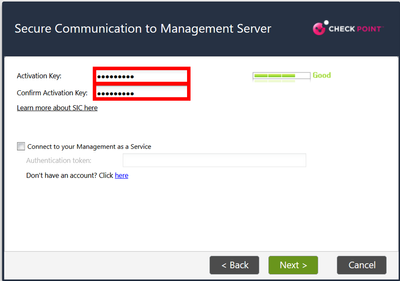
2) Assign a SIC one-time password.
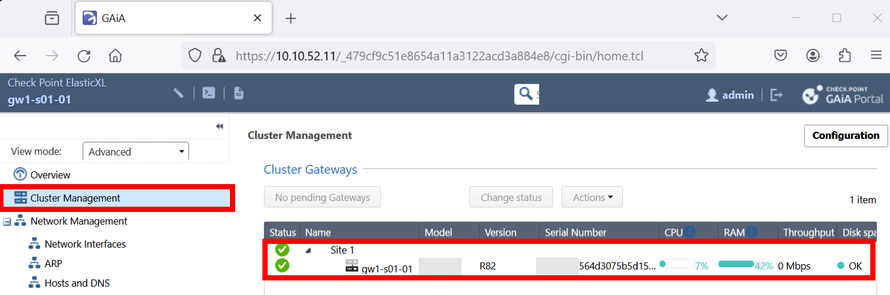
3) After installation, you will find the ElasticXL Gateway under the "Cluster Management" menu item.
4) Create a new gateway object (not CLusterXL object) in the SmartConsole.
5) Now establish a SIC connection to the ElasticXL gateway IP from the SmartDashboard.
6) Afterwards, install a policy on the gateway.
| Add more ElasticXL gateways to the cluster. |
|---|
1) Wire the next appliances via the switch infrastructure so that all sync interfaces are connected to same network.
Normally the ElasticXl sync interface is the eth1 interface.
2) Start the appliance and do not run the installation wizard.
3) Log in to the appliance via console cable or via LOM interface.
You are now in the gclish (global clish). Execute the following command:
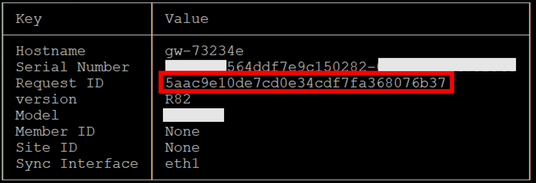
g> show cluster member info
Copy the "Request ID" to the clipboard or to a text file.
4) Open a SSH session to the previously installed appliance and add the appliance with the following command in the gclish:
g> add cluster member method request-id identifier 5aac9e10de7cd0e34cdf7fa368076b37 site-id 1 format json
5) The appliance should be installed automatically after approx. 5 minutes.
The access policy is automatically synchronised by the first ElasticXL gateway (SMO).
6) Both gateways should now be shown in the GAIA portal under the side 1.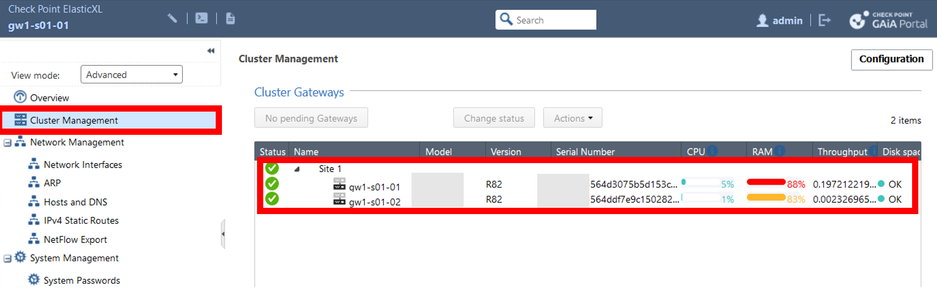
7) Open an SSH session on the first gateway and check if the ElasticXL cluster is working.
You can check this with the following command in the expert mode:
# asg monitor
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There will be a presentation in Vienna at the CPX:
Wednesday 15:20-16:20 --> R82 - ElasticXL and VSNext Generation Under the Hood
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @patones1,
The P letter stands for Pivot. This means this member get all the traffic and distribute to other members for enforcing security.
SMO and Pivot are tasks which currently in R82 both managed by first active members in the active site.
So the bottom line is we can say Pivot is SMO.
Regards,
Shai.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Though support is in the plans, it is not a currently supported configuration to mix hardware types in an ElasticXL Cluster.
80 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice! 👍
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possible the final instructions may differ once R82 is released as undoubtedly this was done based on EA code.
Even so, it gives people an idea of what to expect. 👍🏻
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just curious...will this be available for regular Gaia appliances or only maestro?
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock
Should be possible on the regular appliances.
But we should wait for the GA version.
Best,
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great news.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On ElasticXL is it possible to configure different (and compatible) models as Cluster? If yes could you send me a documentation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Though support is in the plans, it is not a currently supported configuration to mix hardware types in an ElasticXL Cluster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock ElasticXl is for physical clusters only, not Maestro.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to be clear, the only major difference hardware-wise between Maestro and non-Maestro are:
- The addition of the hardware orchestrator
- The installation image used (though the underlying software is the same for Maestro and non-Maestro)
- Some functionality differences between Maestro and non-Maestro configurations: https://support.checkpoint.com/results/sk/sk148074
ElasticXL brings a lot of the functionality of Maestro without the hardware orchestrator.
It is designed to replace ClusterXL for HA/Load Sharing configurations and will use a lot of the same commands and concepts as Maestro (including the Single Management Object).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will R82 and ElasticXL be presented at the CPX in Vienna?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There will be a presentation in Vienna at the CPX:
Wednesday 15:20-16:20 --> R82 - ElasticXL and VSNext Generation Under the Hood
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hope the video of it is posted here, would be awesome.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aren't you coming to Vegas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No buddy, not coming.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Videos of CPX sessions will be posted after Las Vegas next week.
I can assure you we will also cover this topic in future CheckMates sessions 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And it was a really good presentation. Thanks for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I try this elasticXL with 5800 device,
2 box 5800 already reimage with r82 version and running first time wizard for thats 2 box 5800, do I need to reset one box ?
1) Wire the next appliances via the switch infrastructure so that all sync interfaces are connected to same network.
Normally the ElasticXl sync interface is the eth1 interface. --> this is the UTP interface? I dont have sfp interface
We can do add more sync interface on SMO if we add more gateway to elasticXL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Ricki_Juntak ,
you find some hints on ElasticXL in this guide here. Essentially:
- have your appliances imaged with R82
- cable all machines as indicated in admin guide
- make sure management and sync network ports are connected to dedicated networks
- make sure internal and external interfaces are connected to dedicated networks
- run First Time Wizard on one of the appliances
- this will become your first member of the ElasticXL system
- power up your second appliance
- don't touch it
- it will start and advertise on SYNC network "here I am - I am an R82 appliance and ready to join an ElasticXL cluster"
- open Gaia Web UI on first ElasticXL member
- go to Cluster Management menu
- see the second appliance is ready to join
hope this helps - greetings
pelmer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Peter,
Thank you,
I think this success:
[Global] GW1-s01-01> cphaprob stat
Cluster Mode: HA Over LS
ID Unique Address Assigned Load State Name
1 (local) 192.0.2.1 50% ACTIVE(!P) GW1-s01-01
2 192.0.2.2 50% ACTIVE(!) GW1-s01-02
Active PNOTEs: IAC
Last member state change event:
Event Code: CLUS-110405
State change: ACTIVE -> ACTIVE(!)
Reason for state change: Sync interface is down
Event time: Thu Nov 28 14:24:42 2024
but I use Sync to the direct connect to device not use switch for sync.
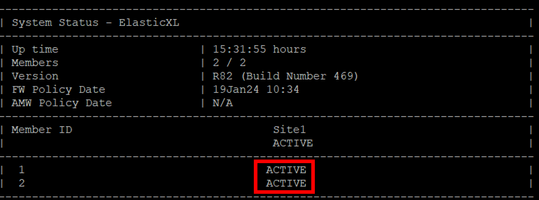
[Global] GW1-s01-01> asg stat
--------------------------------------------------------------------------------
| System Status - ElasticXL |
--------------------------------------------------------------------------------
| Up time | 03:49:47 hours |
| Members | 2 / 2 |
| Version | R82 (Build Number 777) |
--------------------------------------------------------------------------------
| Site Parameters |
--------------------------------------------------------------------------------
| Unit | Site1 |
--------------------------------------------------------------------------------
| Members | 2 / 2 |
--------------------------------------------------------------------------------
[Global] GW1-s01-01>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Ricki_Juntak ,
Can you please clarify that you connected the out of bound interfaces called "Sync" on your appliances directly?
Please check output from both appliances :
# ifconfig Sync
#ifconfig eth1-Sync
Check state is UP RUNNING
Regards,
Shai.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ShaiF,
this is capture from interface sync:
Sync interface main gateway:
Sync Link encap:Ethernet HWaddr 0A:BA(sorry filter mac)
inet addr:192.0.2.1 Bcast:192.0.2.255 Mask:255.255.255.0
UP BROADCAST RUNNING MASTER MULTICAST MTU:1500 Metric:1
RX packets:5783338 errors:0 dropped:0 overruns:0 frame:0
TX packets:8315604 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:635378829 (605.9 MiB) TX bytes:4115666344 (3.8 GiB)
eth1-Sync Link encap:Ethernet HWaddr :0A:BA
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:5783338 errors:0 dropped:0 overruns:0 frame:0
TX packets:8315604 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:635378829 (605.9 MiB) TX bytes:4115666344 (3.8 GiB)
sync interface member 2:
Sync Link encap:Ethernet HWaddr 16:40(sorry mac filter)
inet addr:192.0.2.2 Bcast:192.0.2.255 Mask:255.255.255.0
UP BROADCAST RUNNING MASTER MULTICAST MTU:1500 Metric:1
RX packets:6243350 errors:0 dropped:0 overruns:0 frame:0
TX packets:5489883 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1386116696 (1.2 GiB) TX bytes:605367536 (577.3 MiB)
eth1-Sync Link encap:Ethernet HWaddr 16:40
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:6231909 errors:0 dropped:0 overruns:0 frame:0
TX packets:5485444 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1382366395 (1.2 GiB) TX bytes:604904865 (576.8 MiB)
my question:
why this elasticXL need external switch for SYNC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it does not. you can connect directly in case you have only 2 members.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, but I think its more great and cool if we can edit another interface to be a SYNC interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is going to remove the need for 3 IP addresses per subnet I suppose? No need for 1x IP per cluster members + 1x VIP? This will make it very attractive for remote locations with restricted access to WAN subnets larger than /30 address space.
Does it have to run in active-active mode? I understand why active-active might be ideal for throughput, but there might be scenarios where you'd want it to be active-standby to have less complexity, and to avoid having the orchestration of traffic. When deploying virtual, like on "private cloud" solutions such as VMware ESXi, Nutanix AHV, etc. If both members are running on the same host, there isn't much benefit to have both members active at the same time.
ElasticXL seems like a no-brainer compared to clusterXL, both for HA and for Load Sharing. Have to see if there is any known limitations, and most customers will avoid using new technology for some time. But this all sounds like a great solution over clusterXL to me.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CUT>>>
Does it have to run in active-active mode? I understand why active-active might be ideal for throughput, but there might be scenarios where you'd want it to be active-standby to have less complexity, and to avoid having the orchestration of traffic. When deploying virtual, like on "private cloud" solutions such as VMware ESXi, Nutanix AHV, etc. If both members are running on the same host, there isn't much benefit to have both members active at the same time.
<<<CUT
We are talking about a connection HA. This means that it is not a gateway HA or LS.
The advantage is that in the event of a hardware error, the connections are distributed to the remaining gateways.
PS:
VMWare is currently not supported.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ElasticXL and VSnext (requires ElasticXL) is not supported on VMware ESXi? I guess this means hypervisors in general? Is this from a support point-of-view, meaning it won't be officially supported by Check Point, thus no help from TAC, or won't it work as a result of something in the current R82 software is simply not compatible with VMware and/or other hypervisors?
Asking because I have access to R82 EA and was going to play with it in on my home network (VMware ESXi 8.0) and LAB at work (also VMware ESXi 8.0). But my biggest attraction towards R82 is all related to ElasticXL, and some VSnext. So I won't waste my time if it's not supposed to work at all.
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There must be ways to get it working, as @Peter_Elmer from Check Point demonstrated it at CPX 2024 in Vienna. As far as I remember there is a problem with interface names when constructing sync and management bonds automatically. So, VSNext and ElasticXL seem to run in VMware. Maybe Check Point can post some hints to get this running in labs. That would be really nice.
But besides that, ElasticXL and VSNext will not be officially supported in VMware.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter