- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Question in regards to sk167210
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Question in regards to sk167210
Hey guys,
I hope someone might be able to tell me how to fix this, or if not, at least point me in right direction or what to even look for : - )
I followed sk167210 and all is fine, BUT what fails is what I try to create a rule with generic data center I created. I used below link and it does show connected, its from here:
https://secureupdates.checkpoint.com/IP-list/TOR.txt
But when I try add it to the rule itself, below is what I get:
Any idea why? Also, to add, I cant find single log about it, haha.
Any help is always greatly appreciated 🙂
Btw, found only single community post on this with no responses and cant find much on support site about it either.
Cheers,
Andy
Best,
Andy
Andy
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Network Feed option requires R81.20 all around.
Meanwhile, you can use this took to convert IP-TOR into a JSON file: https://community.checkpoint.com/t5/Scripts/tor2json-bash-script-to-download-TOR-file-and-save-it-in...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock ,
Like we talked in other occasions, we're using Generic DataCenter Objects, and for that we've adapted the script from (https://github.com/HGrigorov/checkpoint) and we added some extra functions on it.
That script collects IP's from those 6 lists and builds a JSON that contains all that data (I've attached the JSON for reference so you can have a look).
|
# Text for <name> field in JSON file NAME[1]="TOR_Exit_Nodes" NAME[2]="TOR_IPBlacklist_Nodes" NAME[3]="OpenDBL_TOR_Exit_Nodes" NAME[4]="OpenDBL_TALOS_Nodes" NAME[5]="OpenDBL_EmergThreats_Nodes" NAME[6]="OpenDL_Bruteforce_Nodes" |
# Download URL #TOR_URL="https://check.torproject.org/torbulkexitlist" TOR_URL[1]="https://secureupdates.checkpoint.com/IP-list/TOR.txt" TOR_URL[2]="https://secureupdates.checkpoint.com/IP-list/IP-blacklist.txt" TOR_URL[3]="http://www.opendbl.net/lists/tor-exit.list" TOR_URL[4]="http://www.opendbl.net/lists/talos.list" TOR_URL[5]="http://www.opendbl.net/lists/etknown.list" TOR_URL[6]="http://www.opendbl.net/lists/bruteforce.list" |
If you have questions, let me know.
Thank you,
PS: Indeed I could have used IoC Feeds, but I wanted a graphical solution, that would be easier to use . I'll go back and have a look 😊 .
(I remember why I didn't use IoC, because it's used only by AntiBot blades, and we wanted to use in Firewall rules...)
Maybe in the next version upgrade (as we're with R81) we will move to R81.20 and start using Network Feed .
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
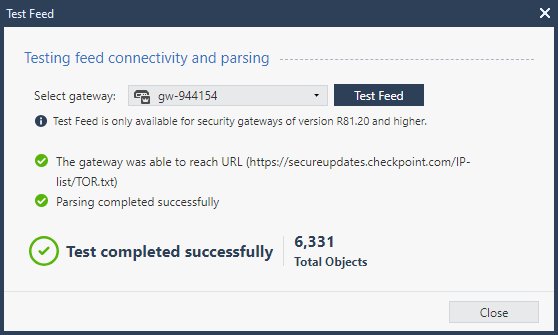
Hi,
The best practice is to use the Custom Intelligence Feed (IoC Feed) - either from SmartConsole or CLI.
Refer to sk132193 - What is the "Custom Intelligence Feeds" feature?
How it looks in R81.20 with the ability to test the feed:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Tal_Paz-Fridman . Here is my question though...considering it shows "connected" in data center object, should it not work to import it in the rule?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think the Generic Data Center file should be in .json format.
I can check it with owners. If this is correct I'll request to add a validation for this.
Regarding the message (check log file), I'll also ask to have it improved.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, I think I see what you are saying. Yea, if thats the case, its odd, as I did not get any warning when I put in txt file link. Question @Tal_Paz-Fridman ...do you think there is json version of that txt link?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Convert it as shown here: https://community.checkpoint.com/t5/Scripts/tor2json-bash-script-to-download-TOR-file-and-save-it-in...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks so much, will try later! Would you mind send the process how you did it, just curious? I followed the same yesterday, but still failed, so clearly I did it wrong.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Guenther,
I just had teams meeting with @Sorin_Gogean and he showed me exactly how this worked, I learned a lot actually. He confirmed that because there is an issue with parsing ipv6 addresses, file you gave could not be imported. Once we used file he provided (no ipv6, all worked fine).
What Im doing now is enabling ipv6 on both my mgmt and gateway and rebooting, so once thats done, will try file you gave and one I converted yesterday and see if it works and update.
Cheers and thanks again so much @Sorin_Gogean , very grateful for all you showed me 🙌🙌🙌
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Btw, how did you get to that screen for testing feed connection? I have R81.20 lab
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, never mind, got it, yes, works on mine as well, so the only question is if there is json version of that txt link? If so, I think that would probably solve this.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That file is not in a format consumable by the Generic Data Center object, which would be JSON.
See: https://support.checkpoint.com/results/sk/sk167210
The Network Feed option in R81.20 should be able to parse this file directly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @PhoneBoy . So just wondering, is there equivalent JSON format for the txt link I posted? If that exissts, it would most likely work...btw, any idea where I can find that option for networkf eed in R81.20? Have the smart console open, so can test it quick. Also, say if mgmt is R81.20 and lets say gateways on R81 base, would that still work?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Network Feed option requires R81.20 all around.
Meanwhile, you can use this took to convert IP-TOR into a JSON file: https://community.checkpoint.com/t5/Scripts/tor2json-bash-script-to-download-TOR-file-and-save-it-in...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hm, cant seem to find script there, k, may have to check later.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
K, did conversion, shows connected in data center object, but still cant import it, exact same error. This is all R81.20
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @the_rock ,
Like we talked in other occasions, we're using Generic DataCenter Objects, and for that we've adapted the script from (https://github.com/HGrigorov/checkpoint) and we added some extra functions on it.
That script collects IP's from those 6 lists and builds a JSON that contains all that data (I've attached the JSON for reference so you can have a look).
|
# Text for <name> field in JSON file NAME[1]="TOR_Exit_Nodes" NAME[2]="TOR_IPBlacklist_Nodes" NAME[3]="OpenDBL_TOR_Exit_Nodes" NAME[4]="OpenDBL_TALOS_Nodes" NAME[5]="OpenDBL_EmergThreats_Nodes" NAME[6]="OpenDL_Bruteforce_Nodes" |
# Download URL #TOR_URL="https://check.torproject.org/torbulkexitlist" TOR_URL[1]="https://secureupdates.checkpoint.com/IP-list/TOR.txt" TOR_URL[2]="https://secureupdates.checkpoint.com/IP-list/IP-blacklist.txt" TOR_URL[3]="http://www.opendbl.net/lists/tor-exit.list" TOR_URL[4]="http://www.opendbl.net/lists/talos.list" TOR_URL[5]="http://www.opendbl.net/lists/etknown.list" TOR_URL[6]="http://www.opendbl.net/lists/bruteforce.list" |
If you have questions, let me know.
Thank you,
PS: Indeed I could have used IoC Feeds, but I wanted a graphical solution, that would be easier to use . I'll go back and have a look 😊 .
(I remember why I didn't use IoC, because it's used only by AntiBot blades, and we wanted to use in Firewall rules...)
Maybe in the next version upgrade (as we're with R81) we will move to R81.20 and start using Network Feed .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The format for Generic Datacenter Object has to be json, not txt. I am pretty sure it is the reason of your issue. If you want to use plain txt files, use custom feeds. where the list is properly parsed, as @Tal_Paz-Fridman already mentioned.
The TOR list is not in json format
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Val, yes, thats correct.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to update on this further, even after enabling ipv6 on both mgmt and gateway (R81.20 lab), still cant import generic data center object, so there is definitely something preventing it. As soon as I remove ipv6 addresses as @Sorin_Gogean showed me, works like a charm.
By the way, for anyone trying to do this, if any issues, as Sorin pointed out, please do below search in the logs (not indicated in the sk)
blade:"CloudGuard IaaS"
THANKS SO MUCH @Sorin_Gogean
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey guys,
For anyone wanting to use ipv6 IP addresses, I attached the json file that works (tested in the lab). All that had to be done was remove [ and ] characters and that did it. Big thanks to my colleague who even all customers say is the best Linux guru they ever met and its true 🙂
Cheers,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter